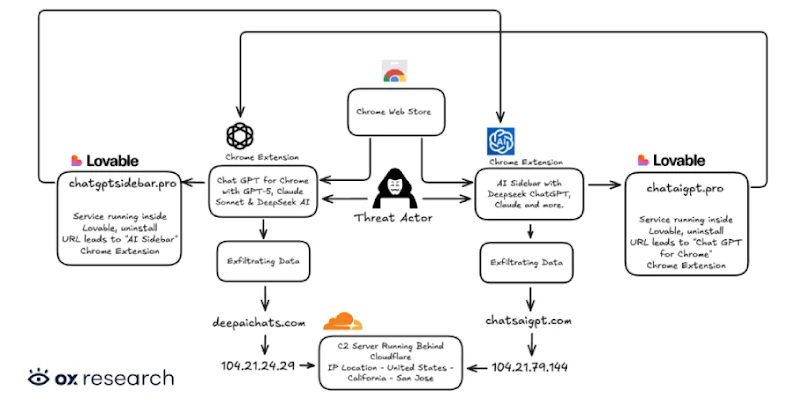
Cybersecurity researchers have found two new malicious extensions on the Chrome Net Retailer which might be designed to exfiltrate OpenAI ChatGPT and DeepSeek conversations alongside looking information to servers underneath the attackers’ management.
The names of the extensions, which collectively have over 900,000 customers, are beneath –
Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI (ID: fnmihdojmnkclgjpcoonokmkhjpjechg, 600,000 customers)
AI Sidebar with Deepseek, ChatGPT, Claude, and extra. (ID: inhcgfpbfdjbjogdfjbclgolkmhnooop, 300,000 customers)
The findings comply with weeks after City VPN Proxy, one other extension with tens of millions of installations on Google Chrome and Microsoft Edge, was caught spying on customers’ chats with synthetic intelligence (AI) chatbots. This tactic of utilizing browser extensions to stealthily seize AI conversations has been codenamed Immediate Poaching by Safe Annex.
The 2 newly recognized extensions “had been discovered exfiltrating person conversations and all Chrome tab URLs to a distant C2 server each half-hour,” OX Safety researcher Moshe Siman Tov Bustan stated. “The malware provides malicious capabilities by requesting consent for ‘nameless, non-identifiable analytics information’ whereas really exfiltrating full dialog content material from ChatGPT and DeepSeek classes.”
The malicious browser add-ons have been discovered to impersonate a legit extension named “Chat with all AI fashions (Gemini, Claude, DeepSeek…) & AI Brokers” from AITOPIA that has about 1 million customers. They’re nonetheless accessible for obtain from the Chrome Net Retailer as of writing, though “Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI” has since been stripped of its “Featured” badge.
As soon as put in, the rogue extensions request that customers grant them permissions to gather anonymized browser habits to purportedly enhance the sidebar expertise. Ought to the person comply with the observe, the embedded malware begins to reap details about open browser tabs and chatbot dialog information.
To perform the latter, it seems to be for particular DOM parts inside the net web page, extracts the chat messages, and shops them regionally for subsequent exfiltration to distant servers (“chatsaigpt[.]com” or “deepaichats[.]com”).
What’s extra, the menace actors have been discovered to leverage Lovable, a synthetic intelligence (AI)-powered internet improvement platform, to host their privateness insurance policies and different infrastructure elements (“chataigpt[.]professional” or “chatgptsidebar[.]professional”) in an try and obfuscate their actions.
The results of putting in such add-ons may be extreme, as they’ve the potential to exfiltrate a variety of delicate data, together with information shared with chatbots like ChatGPT and DeepSeek, and internet looking exercise, together with search queries and inside company URLs.
“This information may be weaponized for company espionage, id theft, focused phishing campaigns, or offered on underground boards,” OX Safety stated. “Organizations whose staff put in these extensions could have unknowingly uncovered mental property, buyer information, and confidential enterprise data.”
Legit Extensions Be part of Immediate Poaching
The disclosure comes as Safe Annex stated it recognized legit browser extensions equivalent to Similarweb and Sensor Tower’s Stayfocusd – every with 1 million and 600,000 customers, respectively – partaking in immediate poaching.
Similarweb is alleged to have launched the power to observe conversations in Could 2025, with a January 1, 2026, replace including a full phrases of service pop-up that makes it express that information entered into AI instruments is being collected to “present the in-depth evaluation of visitors and engagement metrics.” A December 30, 2025, privateness coverage replace additionally spells this out –
This data consists of prompts, queries, content material, uploaded or hooked up information (e.g., pictures, movies, textual content, CSV information) and different inputs that you could be enter or undergo sure synthetic intelligence (AI) instruments, in addition to the outcomes or different outputs (together with any hooked up information included in such outputs) that you could be obtain from such AI instruments (“AI Inputs and Outputs”).
Contemplating the character and normal scope of AI Inputs and Outputs and AI Metadata that’s typical to AI instruments, some Delicate Knowledge could also be inadvertently collected or processed. Nonetheless, the intention of the processing is to not accumulate Private Knowledge so as to have the ability to establish you. Whereas we can’t assure that every one Private Knowledge is eliminated, we do take steps, the place potential, to take away or filter out identifiers that you could be enter or submit to those AI instruments.
Additional evaluation has revealed that Similarweb makes use of DOM scraping or hijacks native browser APIs like fetch() and XMLHttpRequest() – like within the case of City VPN Proxy – to assemble the dialog information by loading a distant configuration file that features customized parsing logic for ChatGPT, Anthropic Claude, Google Gemini, and Perplexity.
Safe Annex’s John Tuckner informed The Hacker Information that the habits is frequent to each Chrome and Edge variations of the Similarweb extension. Similarweb’s Firefox add-on was final up to date in 2019.
“It’s clear immediate poaching has arrived to seize your most delicate conversations and browser extensions are the exploit vector,” Tuckner stated. “It’s not clear if this violates Google’s insurance policies that extensions ought to be constructed for a single function and never load code dynamically.”
“That is just the start of this pattern. Extra corporations will start to comprehend these insights are worthwhile. Extension builders searching for a solution to monetize will add refined libraries like this one provided by the advertising and marketing corporations to their apps.”
Customers who’ve put in these add-ons and are involved about their privateness are suggested to take away them from their browsers and chorus from putting in extensions from unknown sources, even when they’ve the “Featured” tag on them.