Might 23, 2025Ravie LakshmananThreat Intelligence / Community Safety
Cybersecurity researchers have disclosed {that a} menace actor codenamed ViciousTrap has compromised practically 5,300 distinctive community edge gadgets throughout 84 nations and turned them right into a honeypot-like community.
The menace actor has been noticed exploiting a vital safety flaw impacting Cisco Small Enterprise RV016, RV042, RV042G, RV082, RV320, and RV325 Routers (CVE-2023-20118) to corral them right into a set of honeypots en masse. A majority of the infections are positioned in Macau, with 850 compromised gadgets.
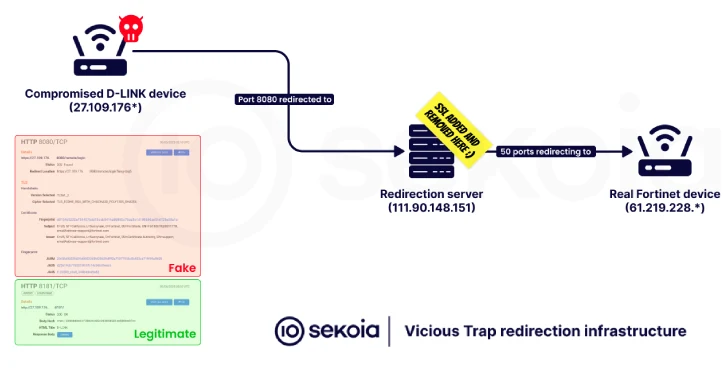
“The an infection chain includes the execution of a shell script, dubbed NetGhost, which redirects incoming site visitors from particular ports of the compromised router to a honeypot-like infrastructure below the attacker’s management permitting them to intercept community flows,” Sekoia mentioned in an evaluation revealed Thursday.
It is price noting that the exploitation of CVE-2023-20118 was beforehand attributed by the French cybersecurity firm to a different botnet dubbed PolarEdge.
Whereas there isn’t a proof that these two units of actions are related, it is believed that the menace actor behind ViciousTrap is probably going organising honeypot infrastructure by breaching a variety of internet-facing tools, together with SOHO routers, SSL VPNs, DVRs, and BMC controllers from greater than 50 manufacturers like Araknis Networks, ASUS, D-Hyperlink, Linksys, and QNAP.
“This setup would permit the actor to look at exploitation makes an attempt throughout a number of environments and doubtlessly gather personal or zero-day exploits, and reuse entry obtained by different menace actors,” it added.
The assault chain entails the weaponization of CVE-2023-20118 to obtain and execute a bash script through ftpget, which then contacts an exterior server to fetch the wget binary. Within the subsequent step, the Cisco flaw is exploited a second time, utilizing it to execute a second script retrieved utilizing the beforehand dropped wget.
The second-stage shell script, internally referenced as NetGhost, is configured to redirect community site visitors from the compromised system to third-party infrastructure managed by the attacker, thereby facilitating adversary-in-the-middle (AitM) assaults. It additionally comes with capabilities to take away itself from the compromised host to attenuate forensic path.
Sekoia mentioned all exploitation makes an attempt have originated from a single IP deal with (“101.99.91[.]151”), with the earliest exercise courting again to March 2025. In a noteworthy occasion noticed a month later, the ViciousTrap actors are mentioned to have repurposed an undocumented internet shell beforehand employed in PolarEdge botnet assaults for their very own operations.
“This assumption aligns with the attacker’s use of NetGhost,” safety researchers Felix Aimé and Jeremy Scion mentioned. “The redirection mechanism successfully positions the attacker as a silent observer, able to accumulating exploitation makes an attempt and, doubtlessly, internet shell accesses in transit.”
As lately as this month, exploitation efforts have additionally focused ASUS routers however from a special IP deal with (“101.99.91[.]239”), though the menace actors haven’t been discovered to create any honeypot on the contaminated gadgets. All of the IP addresses actively used within the marketing campaign are positioned in Malaysia and are a part of an Autonomous System (AS45839) operated by internet hosting supplier Shinjiru.
The actor is believed to be of Chinese language-speaking origin on the idea of a weak overlap with the GobRAT infrastructure and the truth that site visitors is redirected to quite a few belongings in Taiwan and the US.
“The ultimate goal of ViciousTrap stays unclear even [though] we assess with excessive confidence that it is a honeypot-style community,” Sekoia concluded.
Discovered this text fascinating? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.