Sep 05, 2025Ravie LakshmananMalware / Cryptocurrency
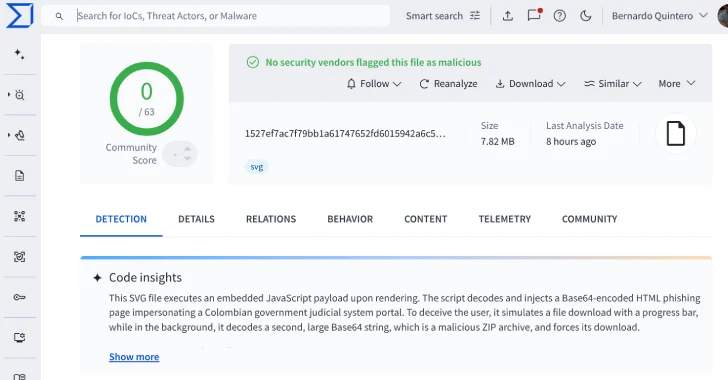
Cybersecurity researchers have flagged a brand new malware marketing campaign that has leveraged Scalable Vector Graphics (SVG) information as a part of phishing assaults impersonating the Colombian judicial system.
The SVG information, in accordance with VirusTotal, are distributed through e-mail and designed to execute an embedded JavaScript payload, which then decodes and injects a Base64-encoded HTML phishing web page masquerading as a portal for Fiscalía Normal de la Nación, the Workplace of the Lawyer Normal of Colombia.
The web page then simulates an official authorities doc obtain course of with a faux progress bar, whereas it stealthily triggers the obtain of a ZIP archive within the background. The precise nature of the ZIP file was not disclosed.
The Google-owned malware scanning service stated it discovered 44 distinctive SVG information, all of which have remained undetected by antivirus engines, owing to the usage of methods like obfuscation, polymorphism, and enormous quantities of junk code to evade static detection strategies.
In all, as many as 523 SVG information have been detected within the wild, with the earliest pattern courting again to August 14, 2025.
“Wanting deeper, we noticed that the earliest samples had been bigger, round 25 MB, and the dimensions decreased over time, suggesting the attackers had been evolving their payloads,” VirusTotal stated.
The disclosure comes as cracked variations of legit software program and ClickFix-style ways are getting used to lure customers into infecting their Apple macOS programs with an info stealer referred to as Atomic macOS Stealer (AMOS), exposing companies to credential stuffing, monetary theft, and different follow-on assaults.
“AMOS is designed for broad knowledge theft, able to stealing credentials, browser knowledge, cryptocurrency wallets, Telegram chats, VPN profiles, keychain gadgets, Apple Notes, and information from widespread folders,” Pattern Micro stated. “AMOS reveals that macOS is now not a peripheral goal. As macOS units acquire floor in enterprise settings, they’ve turn out to be a extra engaging and profitable focus for attackers.”
The assault chain primarily includes focusing on customers in search of cracked software program on websites like haxmac[.]cc, redirecting them to bogus obtain hyperlinks that present set up directions designed to trick them into working malicious instructions on the Terminal app, thus triggering the deployment of AMOS.
It is value noting that Apple prevents the set up of .dmg information missing correct notarization on account of macOS’s Gatekeeper protections, which require the applying packages to be signed by an recognized developer and notarized by Apple.
“With the discharge of macOS Sequoia, makes an attempt to put in malicious or unsigned .dmg information, comparable to these utilized in AMOS campaigns, are blocked by default,” the corporate added. “Whereas this does not remove the danger fully, particularly for customers who could bypass built-in protections, it raises the barrier for profitable infections and forces attackers to adapt their supply strategies.”
Because of this menace actors are more and more banking on ClickFix, because it permits the stealer to be put in on the machine utilizing Terminal via a curl command specified within the software program obtain web page.
“Whereas macOS Sequoia’s enhanced Gatekeeper protections efficiently blocked conventional .dmg-based infections, menace actors rapidly pivoted to terminal-based set up strategies that proved more practical in bypassing safety controls,” Pattern Micro stated. “This shift highlights the significance of defense-in-depth methods that do not rely solely on built-in working system protections.”
The event additionally follows the invention of a “sprawling cyber marketing campaign” that is focusing on avid gamers looking out for cheats with StealC stealer and crypto theft malware, netting the menace actors greater than $135,000.
Per CyberArk, the exercise is notable for leveraging StealC’s loader capabilities to obtain extra payloads, on this case, a cryptocurrency stealer that may siphon digital property from customers on contaminated machines.