Nov 19, 2025Ravie LakshmananVulnerability / Menace Intelligence
A newly found marketing campaign has compromised tens of hundreds of outdated or end-of-life (EoL) ASUS routers worldwide, predominantly in Taiwan, the U.S., and Russia, to rope them into a large community.
The router hijacking exercise has been codenamed Operation WrtHug by SecurityScorecard’s STRIKE group. Southeast Asia and European international locations are a few of the different areas the place infections have been recorded.
The assaults seemingly contain the exploitation of six identified safety flaws in end-of-life ASUS WRT routers to take management of inclined units. All of the contaminated routers have been discovered to share a singular self-signed TLS certificates with an expiration date set for 100 years from April 2022.
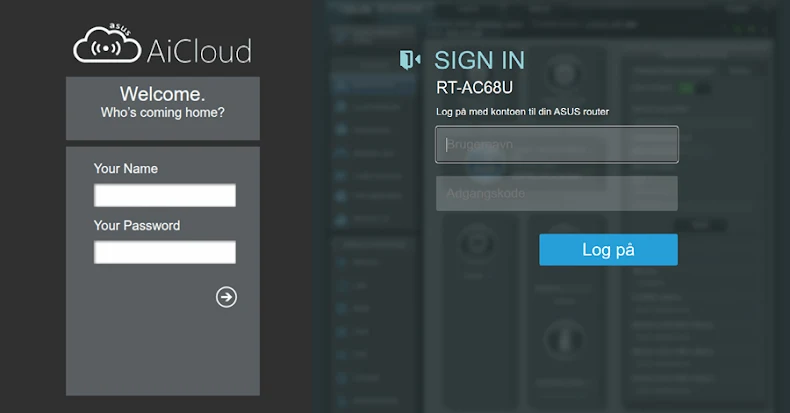
SecurityScorecard stated 99% of the companies presenting the certificates are ASUS AiCloud, a proprietary service designed to allow entry to native storage by way of the web.
“It leverages the proprietary AiCloud service with n-day vulnerabilities with a view to achieve excessive privileges on Finish-Of-Life ASUS WRT routers,” the corporate stated in a report shared with The Hacker Information, including the marketing campaign, whereas not precisely an Operational Relay Field (ORB), bears similarities with different China-linked ORBs and botnet networks.
The assaults seemingly exploit vulnerabilities tracked as CVE-2023-41345, CVE-2023-41346, CVE-2023-41347, CVE-2023-41348, CVE-2024-12912, and CVE-2025-2492 for proliferation. Apparently, the exploitation of CVE-2023-39780 has additionally been linked to a different Chinese language-origin botnet dubbed AyySSHush (aka ViciousTrap). Two different ORBs which have focused routers in latest months are LapDogs and PolarEdge.
Out of all of the contaminated units, seven IP addresses have been flagged for exhibiting indicators of compromise related to each WrtHug and AyySSHush, doubtlessly elevating the likelihood that the 2 clusters could possibly be associated. That being stated, there isn’t a proof to again this speculation past the shared vulnerability.
The listing of router fashions focused within the assaults is beneath –
ASUS Wi-fi Router 4G-AC55U
ASUS Wi-fi Router 4G-AC860U
ASUS Wi-fi Router DSL-AC68U
ASUS Wi-fi Router GT-AC5300
ASUS Wi-fi Router GT-AX11000
ASUS Wi-fi Router RT-AC1200HP
ASUS Wi-fi Router RT-AC1300GPLUS
ASUS Wi-fi Router RT-AC1300UHP
It is at present not clear who’s behind the operation, however the in depth focusing on of Taiwan and overlaps with earlier techniques noticed in ORB campaigns from Chinese language hacking teams recommend it could possibly be the work of an unknown China-affiliated actor.
“This analysis highlights the rising development of malicious risk actors focusing on routers and different community units in mass an infection operations,” SecurityScorecard stated. “These are generally (however not completely) linked to China Nexus actors, who execute their campaigns in a cautious and calculated method to broaden and deepen their world attain.”
“By chaining command injections and authentication bypasses, risk actors have managed to deploy persistent backdoors by way of SSH, typically abusing official router options to make sure their presence survives reboots or firmware updates.”