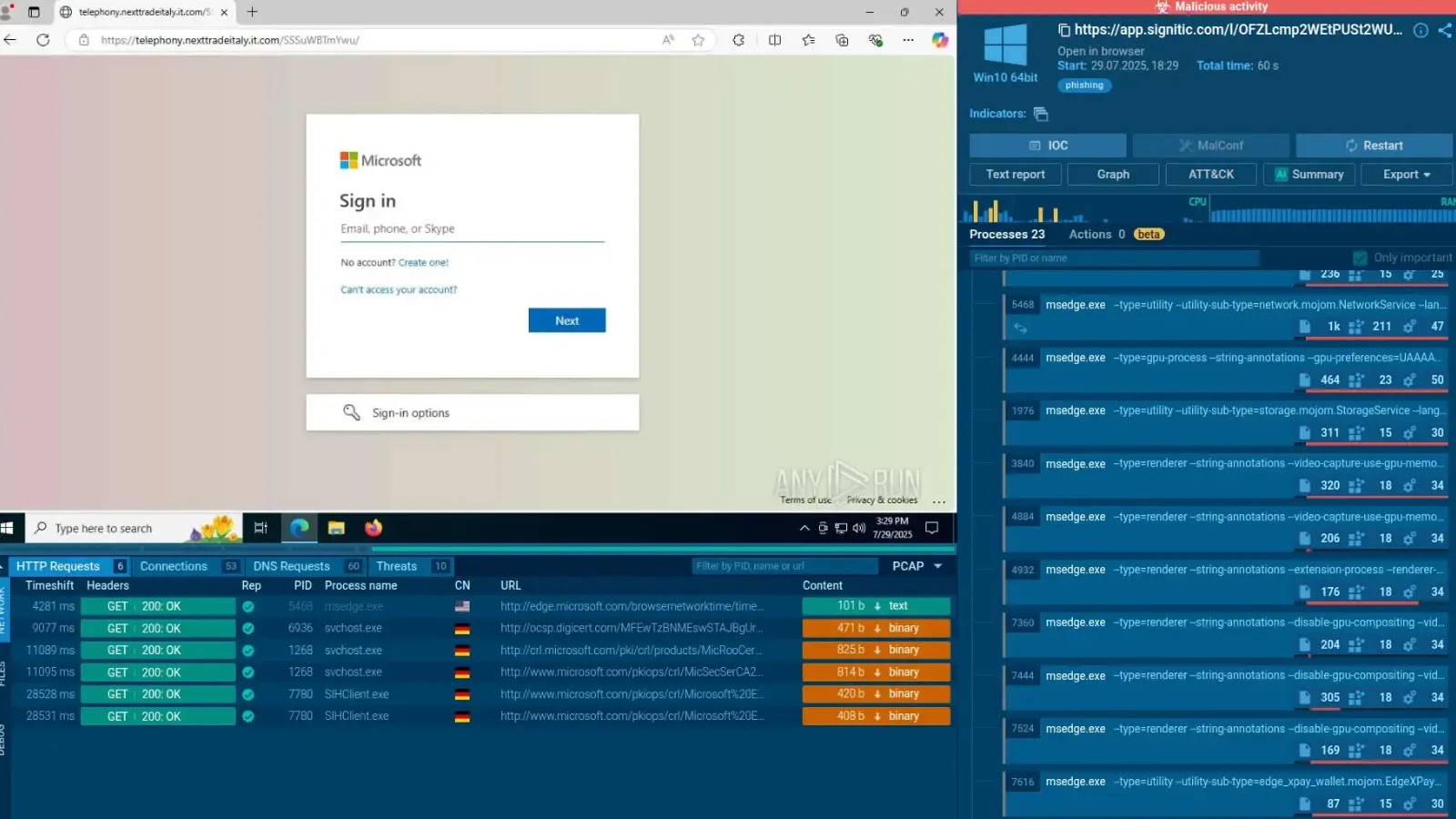
Constructing analyst experience is a race towards time that many Safety Operations Facilities (SOCs) are dropping. New hires typically require over six months to deal with complicated incidents with confidence, making a bottleneck the place senior analysts should compensate for the abilities hole.
Conventional coaching, reliant on theories and simulations, struggles to maintain tempo with the velocity of real-world assaults. To bridge this hole, main SOCs are shifting their technique: turning each day investigations right into a steady studying surroundings the place experience scales alongside operations.
To construct lasting experience, safety leaders are redesigning workflows to show as they defend. The best groups now use interactive environments that enable analysts to discover, experiment, and study from stay information with out risking organizational safety.
This “learning-while-doing” method depends on protected experimentation. By permitting analysts to check hypotheses and hint attacker habits in real-time, SOCs foster vital pondering fairly than simply reactive button-pushing instruments like ANY.RUN Interactive Sandbox facilitates this by offering a protected, collaborative area the place analysts in any respect ranges can work together immediately with threats. As an alternative of separating coaching from each day duties, each evaluation turns into a twin alternative for protection and talent acquisition.
AI-Powered Insights Speed up Course of
The combination of AI into evaluation workflows is a main driver for quicker experience scaling. Trendy sandboxes now make use of AI assistants to behave as power multipliers for junior analysts. For instance, ANY.RUN’s sandbox consists of AI-powered summaries that immediately clarify malicious processes and behaviors.
These options bridge the hole between complicated information and analyst understanding:
Prompt Explanations: AI critiques present real-time context for particular malware behaviors, resembling why a course of is executing a selected command or connecting to a selected IP.
Verdict Readability: ChatGPT-powered evaluation gives detailed verdicts, explaining why a file is malicious fairly than simply flagging it, which helps junior workers perceive the “why” behind the alert.
Lowered Studying Curve: By embedding these insights into routine investigations, the expertise reduces the intimidation issue of complicated threats, permitting newer analysts to make assured selections quicker.
Experience grows quickest when it’s shared. Trendy SOC platforms are shifting away from remoted investigations towards collaborative environments. Options that enable groups to share periods, add feedback, and overview investigations side-by-side allow junior specialists to study immediately from senior friends on stay instances.
Past the interior group, entry to a broader neighborhood performs a vital function. Analysts can now faucet into huge libraries of public evaluation periods, 1000’s of that are uploaded each day, to check the most recent Indicators of Compromise (IOCs) and ways mapped to the MITRE ATT&CK framework. This transforms scattered particular person information right into a structured, globally accessible useful resource.
Shifting to an interactive, AI-supported workflow delivers quantifiable operational enhancements. Organizations adopting these strategies report important positive factors in effectivity and velocity, permitting them to deal with increased alert volumes with out increasing headcount.
Key Efficiency Metrics for Modernized SOCs
MetricImpactDescriptionInvestigation Speed94% FasterReal-time interplay and automation reveal malicious exercise nearly immediately, drastically slicing dwell time.SOC Efficiency3x HigherTeams cut back guide work, permitting for extra deal with validation, correlation, and proactive protection.Tier 1 Workload20% LowerStreamlined processes and AI help cut back the quantity of repetitive duties and noise for entry-level analysts.Escalation Rate30% ReductionBetter visibility and intuitive instruments empower Tier 1 analysts to resolve extra incidents independently, decreasing Tier 2 bottlenecks.Onboarding TimeWeeks vs. MonthsHands-on entry to real-world threats accelerates operational readiness for brand new hires.
By integrating AI-powered insights and interactive studying into the each day workflow, organizations are doing extra than simply closing tickets quicker; they’re constructing a resilient, self-improving safety group able to adapting to tomorrow’s threats.
Comply with us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.