Lower than every week after addressing a important Distant Code Execution (RCE) vulnerability, the React staff has disclosed three extra safety flaws affecting React Server Elements (RSC).
Safety researchers found these new points whereas trying to bypass the mitigations for the earlier “React2Shell” exploit.
Whereas the unique RCE patch stays efficient, the newly found vulnerabilities introduce dangers relating to Denial-of-Service (DoS) and the unauthorized publicity of server-side supply code.
The React staff emphasizes that earlier updates (variations 19.0.2, 19.1.3, and 19.2.2) contained an incomplete repair, necessitating a right away second improve.
Probably the most extreme of the brand new flaws (rated Excessive Severity) includes a Denial-of-Service vector. Researchers discovered {that a} malicious HTTP request despatched to a Server Features endpoint can set off an infinite loop throughout React’s deserialization course of.
This causes the server course of to hold and consumes out there CPU assets, successfully taking the applying offline.
A separate Medium Severity subject permits attackers to control HTTP requests to leak the supply code of Server Features. Whereas runtime secrets and techniques (like surroundings variables) stay safe, any hardcoded secrets and techniques or logic inside the operate might be uncovered.
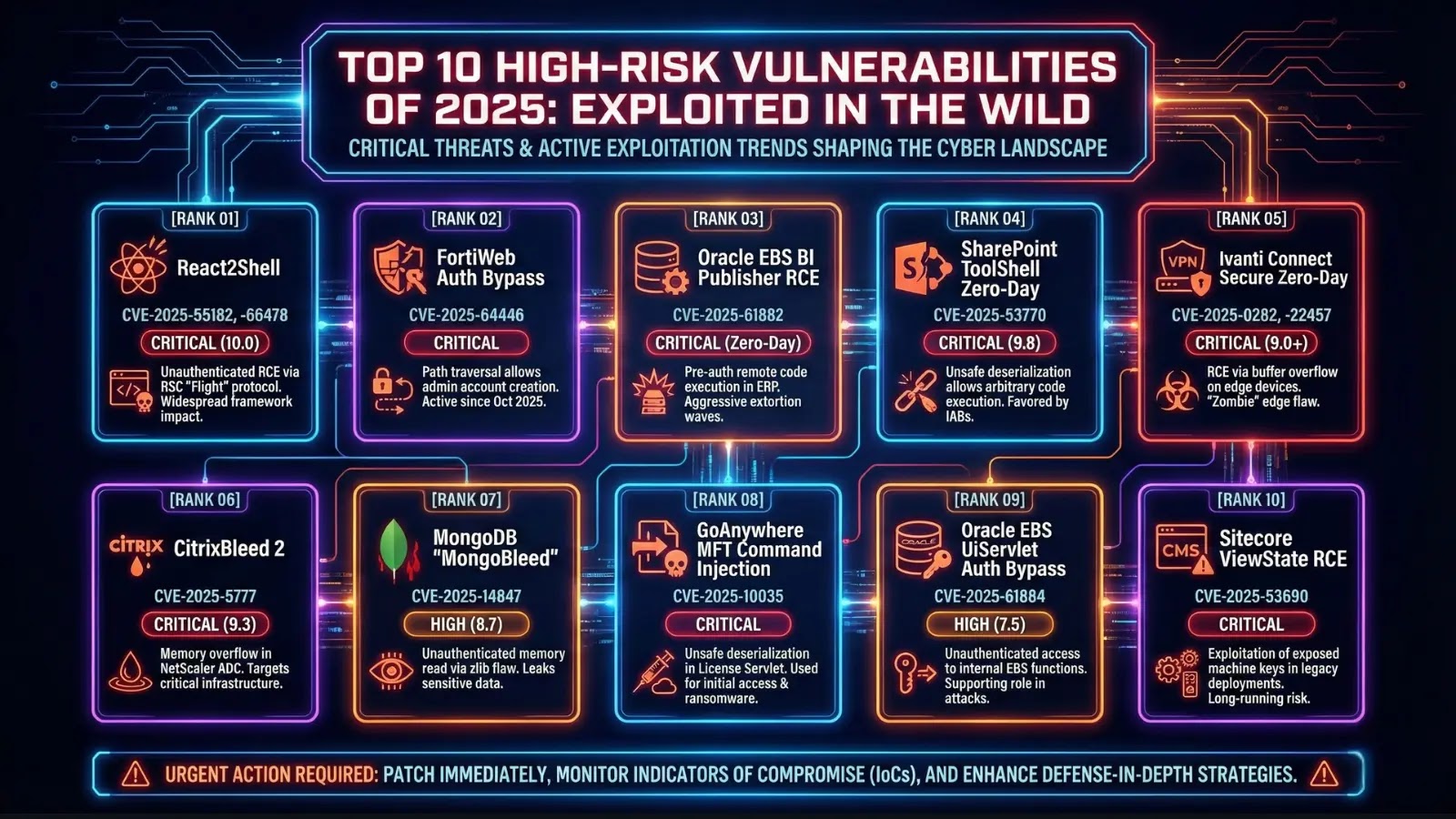
The vulnerabilities are tracked below the next identifiers:
CVE IDVulnerability TypeSeverityCVSS ScoreCVE-2025-55184Denial of ServiceHigh7.5CVE-2025-67779Denial of Service (Patch Bypass)High7.5CVE-2025-55183Source Code ExposureMedium5.3
Affected Variations
These vulnerabilities have an effect on the react-server-dom-webpack, react-server-dom-parcel, and react-server-dom-turbopack packages. Customers of frameworks equivalent to Subsequent.js, Waku, and React Router are probably impacted.
The preliminary patches launched earlier this week have been incomplete. If you’re at present operating variations 19.0.2, 19.1.3, or 19.2.2, you stay susceptible to the DoS exploit (CVE-2025-67779).
Builders should improve to the next “protected” variations instantly:
19.0.x department: Improve to 19.0.3
19.1.x department: Improve to 19.1.4
19.2.x department: Improve to 19.2.3
The React staff famous that discovering follow-up vulnerabilities is widespread after a high-profile disclosure, drawing parallels to the “Log4Shell” incident, the place group probing uncovered adjoining flaws. Credit score for these discoveries goes to researchers Andrew MacPherson, RyotaK, and Shinsaku Nomura.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.