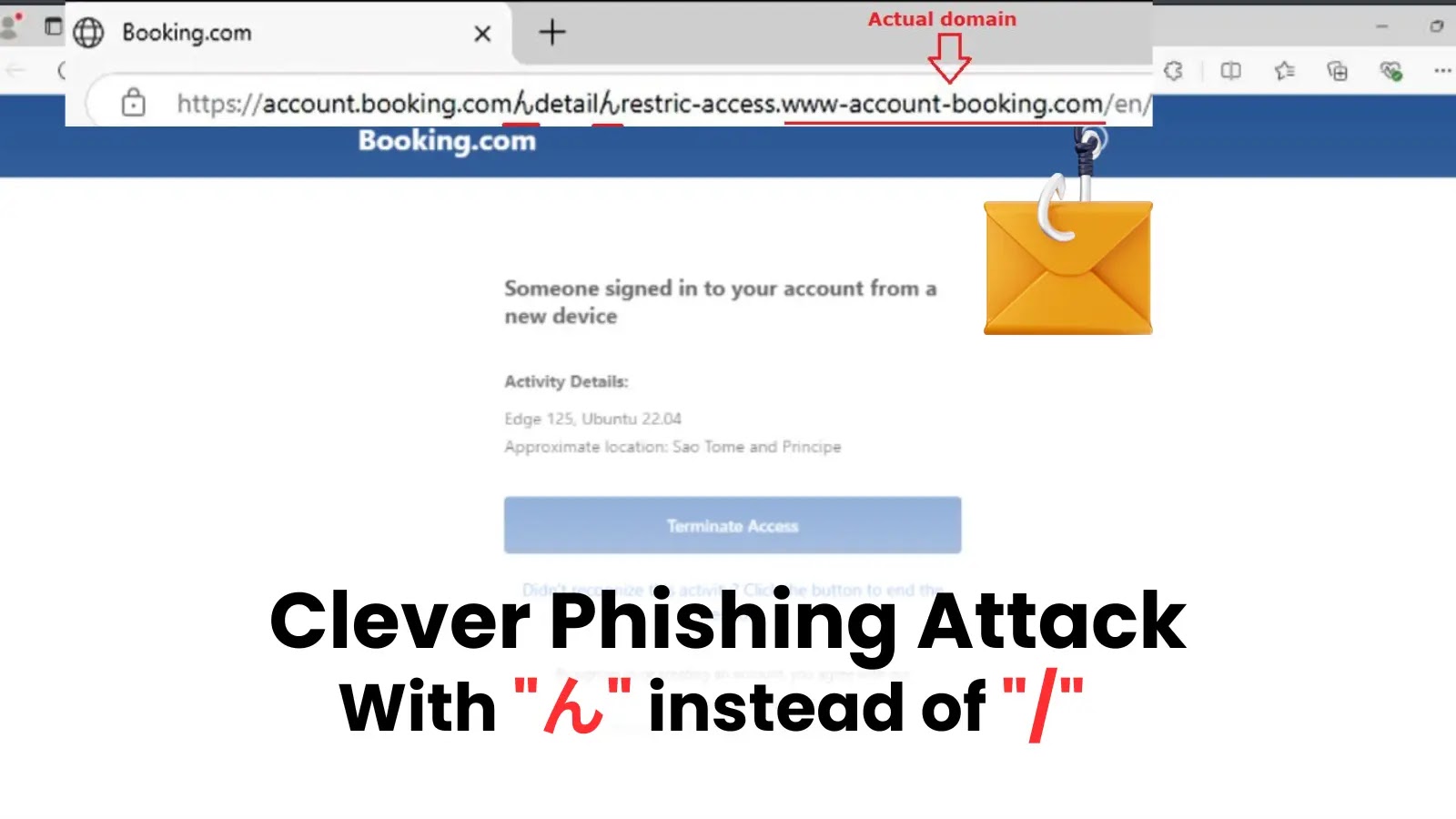
WhatsApp’s multi-device encryption protocol has lengthy leaked metadata, permitting attackers to fingerprint customers’ gadget working programs, aiding focused malware supply. Latest analysis highlights partial fixes by Meta, however transparency points persist.
Meta’s WhatsApp, with over 3 billion month-to-month lively customers, makes use of end-to-end encryption (E2EE) for message safety; nonetheless, its multi-device function reveals gadget info.
On this setup, senders set up separate classes with every recipient gadget, utilizing distinctive encryption keys generated on the gadget relatively than on servers.
Implementation variations in key IDs, like Signed Pre-Key (Signed PK) and One-Time Pre-Key (OTPK), reveal whether or not a tool runs Android or iOS, which is essential for reconnaissance in cyber kill chains.
Attackers exploit this passively by querying WhatsApp servers for session keys with out person interplay, figuring out OS varieties to deploy exact exploits and Android malware to Android units, avoiding iOS or alerting victims.
WhatsApp gadget fingerprinting (Supply: TalBeerySec)
Early 2024 analysis by Tal A. Be’ery at WOOT’24 uncovered leaks of gadget rely, varieties, and identities by way of per-device classes primarily based on Sign’s protocol.
Later that 12 months, attackers pinpointed particular units for exploits. In 2025, Gabriel Karl Gegenhuber et al. at WOOT’25 detailed OS fingerprinting: Android Signed PK IDs increment slowly from 0 month-to-month, whereas iOS patterns differ sharply.
Tal A. Be’ery verified this with customized instruments, confirming attackers chain these leaks: detect OS, ship OS-specific payloads undetected.
WhatsApp’s Silent Repair
Just lately, WhatsApp modified the project of Android Signed PK IDs to random values throughout the 24-bit vary, thwarting that vector. This transformation, detected by way of monitoring instruments, marks a shift from Meta’s prior stance, which dismissed it as non-actionable.
WhatsApp gadget fingerprinting (Supply: TalBeerySec)
Nevertheless, OTPK stays distinguishable: iOS begins low and increments each few days, versus Android’s full random span. Instruments tailored post-fix nonetheless reliably detect the OS.
This allows superior persistent threats (APTs) to make use of WhatsApp as a vector for malware, as seen within the Paragon adware circumstances. No person notifications happen throughout queries, thereby preserving stealth.
Critics word that the rollout lacked researcher alerts, bug bounties, or CVE project, in contrast to an analogous situation by which a bounty was paid with out a CVE. CVEs doc points by way of CVSS scores, not disgrace; such omissions hinder monitoring.
Whereas fixes evolve, full randomization throughout platforms and CVE transparency would higher defend billions, enabling group collaboration. Customers ought to restrict linked units and monitor exercise amid ongoing dangers.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.