Jan 06, 2026Ravie LakshmananMalware / Endpoint SecuritySource: Securonix
Cybersecurity researchers have disclosed particulars of a brand new marketing campaign dubbed PHALT#BLYX that has leveraged ClickFix-style lures to show fixes for faux blue display screen of loss of life (BSoD) errors in assaults focusing on the European hospitality sector.
The tip objective of the multi-stage marketing campaign is to ship a distant entry trojan generally known as DCRat, in keeping with cybersecurity firm Securonix. The exercise was detected in late December 2025.
“For preliminary entry, the risk actors make the most of a faux Reserving.com reservation cancellation lure to trick victims into executing malicious PowerShell instructions, which silently fetch and execute distant code,” researchers Shikha Sangwan, Akshay Gaikwad, and Aaron Beardslee stated.
The place to begin of the assault chain is a phishing e mail impersonating Reserving.com that incorporates a hyperlink to a faux web site (e.g., “low-house[.]com”). The messages warn recipients of sudden reservation cancellations, urging them to click on the hyperlink to substantiate the cancellation.
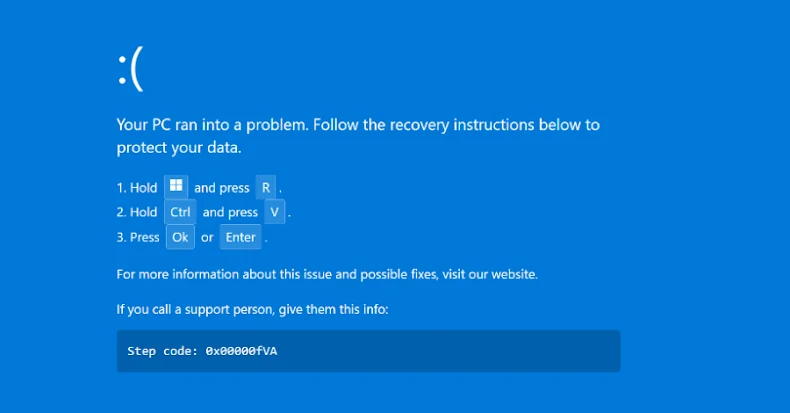
The web site to which the sufferer is redirected masquerades as Reserving.com, and serves a faux CAPTCHA web page that leads them to a bogus BSoD web page with “restoration directions” to open the Home windows Run dialog, paste a command, and press the Enter key. In actuality, this leads to the execution of a PowerShell command that in the end deploys DCRat.
Particularly, this entails a multi-step course of that commences with the PowerShell dropper downloading an MSBuild mission file (“v.proj”) from “2fa-bns[.]com”, which is then executed utilizing “MSBuild.exe” to run an embedded payload liable for configuring Microsoft Defender Antivirus exclusions to evade detection, organising persistence on the host within the Startup folder, and launching the RAT malware after downloads it from the identical location because the MSBuild mission.
It is also able to disabling the safety program altogether if discovered to be operating with administrator privileges. If it does not have elevated rights, the malware enters a loop that triggers a Home windows Consumer Account Management (UAC) immediate each two seconds for thrice in hopes that the sufferer will grant it the required permissions out of sheer frustration.
In tandem, the PowerShell code takes steps to open the reputable Reserving.com admin web page within the default browser as a distraction mechanism and to provide an impression to the sufferer that the motion was reputable.
DCRat, additionally known as Darkish Crystal RAT, is an off-the-shell .NET trojan that may harvest delicate data and increase its performance via a plugin-based structure. It is geared up to hook up with an exterior server, profile the contaminated system, and await incoming instructions from the server, enabling the attackers to log keystrokes, run arbitrary instructions, and ship further payloads like a cryptocurrency miner.
The marketing campaign is an instance of how risk actors are leveraging living-off-the-land (LotL) methods, comparable to abusing trusted system binaries like “MSBuild.exe,” to maneuver the assault to the following stage, set up a deeper foothold, and keep persistence inside compromised hosts.
“The phishing emails notably function room cost particulars in Euros, suggesting the marketing campaign is actively focusing on European organizations,” Securonix stated. “Using the Russian language inside the ‘v.proj’ MSBuild file hyperlinks this exercise to Russian risk elements utilizing DCRat.”
“Using a custom-made MSBuild mission file to proxy execution, coupled with aggressive tampering of Home windows Defender exclusions, demonstrates a deep understanding of contemporary endpoint safety mechanisms.”