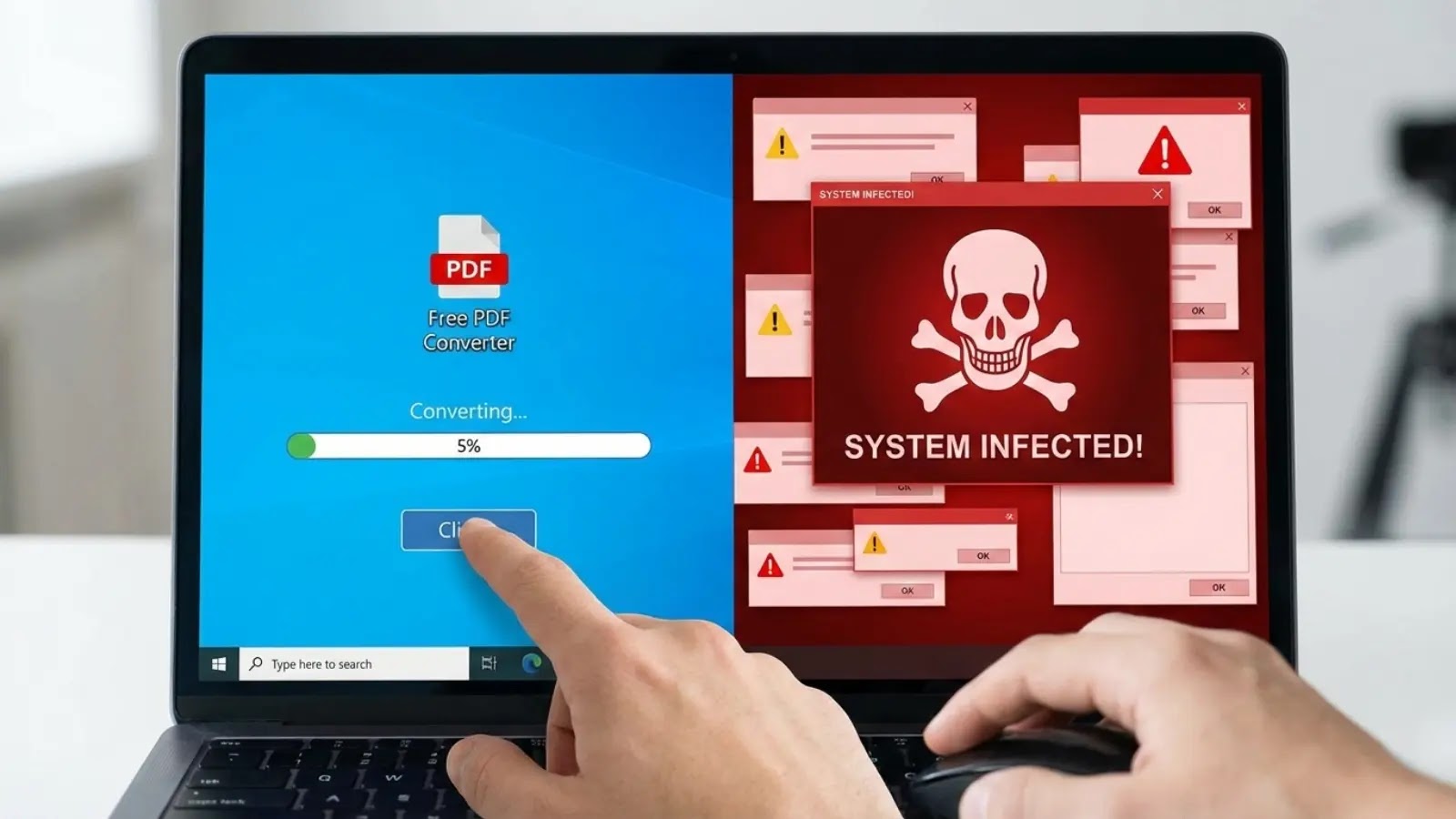
Malicious file converter functions distributed via misleading ads are infecting 1000’s of techniques with persistent distant entry trojans (RATs).
These seemingly respectable productiveness instruments carry out their marketed features whereas secretly putting in backdoors that give attackers steady entry to sufferer computer systems.
Nextron Techniques discovered that the an infection chain sometimes begins with malicious Google ads positioned on respectable web sites, together with online game obtain pages, grownup content material websites, and productiveness instrument web sites.
When customers seek for file conversion instruments like “Phrase to PDF converter” or picture converters, these adverts seem on the high of search outcomes, making them seem reliable. Clicking the advert redirects victims via a number of domains earlier than touchdown on faux converter web sites that ship trojanized software program.
The malicious payload supply web sites share distinctive traits that make them recognizable as soon as recognized. Domains like ez2convertapp[.]com, convertyfileapp[.]com, powerdocapp[.]com, and pdfskillsapp[.]com all current outstanding obtain buttons and comparable web page buildings, together with FAQs, characteristic descriptions, and privateness insurance policies.
Malicious Web sites (Supply: Nextron Techniques)
Many of those domains don’t host dropper recordsdata instantly however as an alternative redirect customers to further domains that present the precise malicious downloads.
Code Signing Creates False Legitimacy
To evade detection and seem reliable, attackers signal their malware with code signing certificates from publishers like BLUE TAKIN LTD, TAU CENTAURI LTD, and SPARROW TIDE LTD.
Whereas many certificates have been revoked after discovery, new campaigns constantly emerge with recent, legitimate certificates that bypass primary safety checks. This permits the malware to look as respectable software program to each finish customers and safety instruments performing signature verification.
After obtain, the converter functions written in C# drop further payloads into the %LocalAppData% listing and create scheduled duties that execute “updater” binaries each 24 hours.
In line with Nextron Techniques evaluation, the scheduled duties sometimes begin sooner or later after preliminary an infection, and this “+1 day” offset serves as a helpful forensic indicator for pinpointing the preliminary entry timestamp. A system-specific UUID saved in an id.txt file identifies every sufferer throughout command-and-control (C2) communications.
The ultimate-stage payload features as a generic execution engine that contacts attacker-controlled C2 servers to retrieve and execute malicious .NET assemblies. These RATs present attackers with capabilities together with knowledge theft, keylogging, display seize, file system entry, and the power to obtain further malware.
C2 Authentication (Supply: Nextron Techniques)
The UpdateRetriever.exe part authenticates with the C2 server, receives executable code, and runs it silently on the sufferer system whereas sending outcomes again to attackers.
Organizations can detect these infections by monitoring Home windows Occasion ID 4698 (scheduled job created) in Safety.evtx logs, which requires enabling object entry auditing.
Suspicious scheduled duties executing from %LocalAppData% directories function glorious detection anchors, particularly when mixed with Sysmon Occasion ID 13 registry monitoring and Process Scheduler Operational occasions.
Further defenses embrace implementing software management insurance policies, similar to AppLocker, to dam execution from user-writable places, and creating deny guidelines for recognized malicious code-signing certificates.
Malicious Payload Supply Domains
DomainTypeez2convertapp[.]comPayload Deliveryconvertyfileapp[.]comPayload Deliverypowerdocapp[.]comPayload Deliveryinfinitedocsapp[.]comPayload Deliveryconvertmasterapp[.]comPayload Deliveryconmateapp[.]comPayload Deliverypdfskillsapp[.]comPayload Deliverypdfclickapp[.]comPayload Deliveryzappdfapp[.]comPayload Deliveryonezipapp[.]comPayload Deliverycrystalpdf[.]comPayload Deliverypdfsparkware[.]comPayload Deliveryzipmatepro[.]comPayload Deliverynotawordapp[.]comPayload Supply
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.