MEDUSA, an AI-first Static Software Safety Testing (SAST) software boasting 74 specialised scanners and over 180 AI agent safety guidelines.
This open-source CLI scanner targets fashionable improvement challenges like false positives and multi-language protection.
MEDUSA consolidates safety scanning throughout 42+ languages and file sorts, together with Python, JavaScript, Go, Rust, Java, Dockerfiles, Terraform, and Kubernetes manifests.
Builders set up it through pip and run scans with a single command, enabling parallel processing for 10-40x speedups over sequential instruments. It generates stories in JSON, HTML, Markdown, or SARIF codecs for CI/CD integration.
Model 2025.9.0 launched an clever false constructive filter that cuts noise by 40-60% by means of context-aware evaluation, similar to detecting safety wrappers and excluding check recordsdata.
Sandbox compatibility ensures it runs in restricted environments like OpenAI Codex by falling again to sequential mode. Sensible caching skips unchanged recordsdata, boosting rescan speeds dramatically.
CVE Detection Capabilities
Pantheon Safety unveiled MEDUSA, which excels at figuring out high-impact vulnerabilities and scanning bundle locks for provide chain dangers.
CVE IDDescriptionCVSS ScoreAffected ComponentsCVE-2025-55182React2Shell pre-auth RCE through Flight protocol deserialization10.0React 19.0.0-19.2.0, Subsequent.js 15.0.0-15.0.4CVE-2025-6514mcp-remote OAuth SSRF to OS command injection RCE9.6mcp-remote authorization endpoint
Upgrading React to 19.0.1+ and Subsequent.js to fifteen.0.5+ mitigates React2Shell publicity.
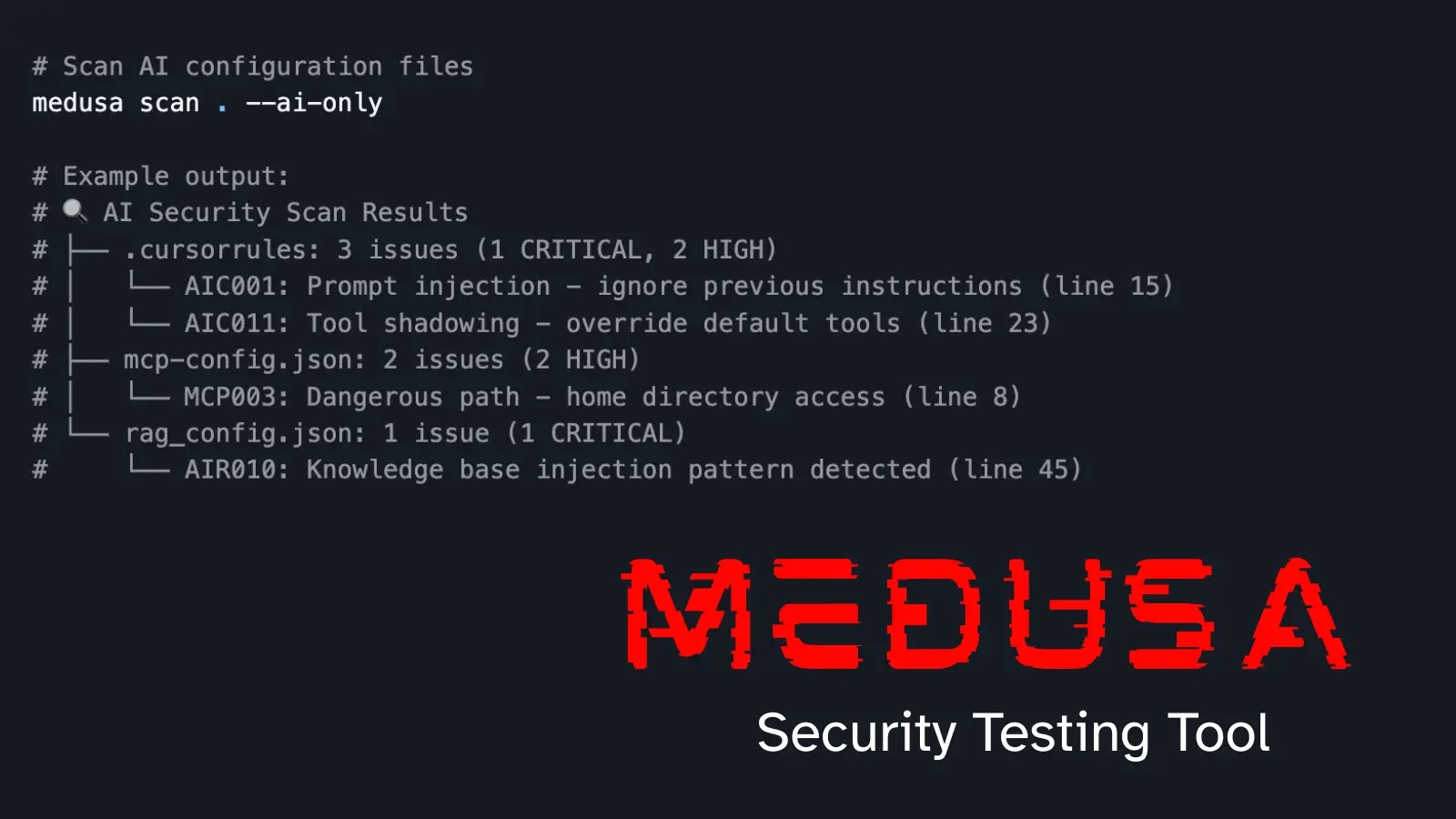
The software contains 180+ guidelines tailor-made for agentic AI, masking OWASP LLM Prime 10 2025 dangers like immediate injection, software poisoning, and RAG poisoning.
Specialised scanners detect points in recordsdata like .cursorrules, CLAUDE.md, mcp.json, and rag.json. Instructions like “medusa scan . –ai-only” isolate AI configs for fast audits.
Customers create a digital setting, then pip set up medusa-security, adopted by medusa init and medusa set up –all for auto-tool setup through winget, Chocolatey, or npm on Home windows.
It helps Claude Code, Cursor, VS Code, Gemini CLI, and GitHub Copilot with slash instructions like /medusa-scan. Configuration through .medusa.yml permits exclusions and fail-on thresholds.
MEDUSA scans 145 recordsdata in 47 seconds with six staff, sustaining constant speeds throughout small to giant tasks. Dogfooding by itself codebase yields zero vital or excessive points. CI/CD workflows combine seamlessly, failing builds on high-severity findings.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.