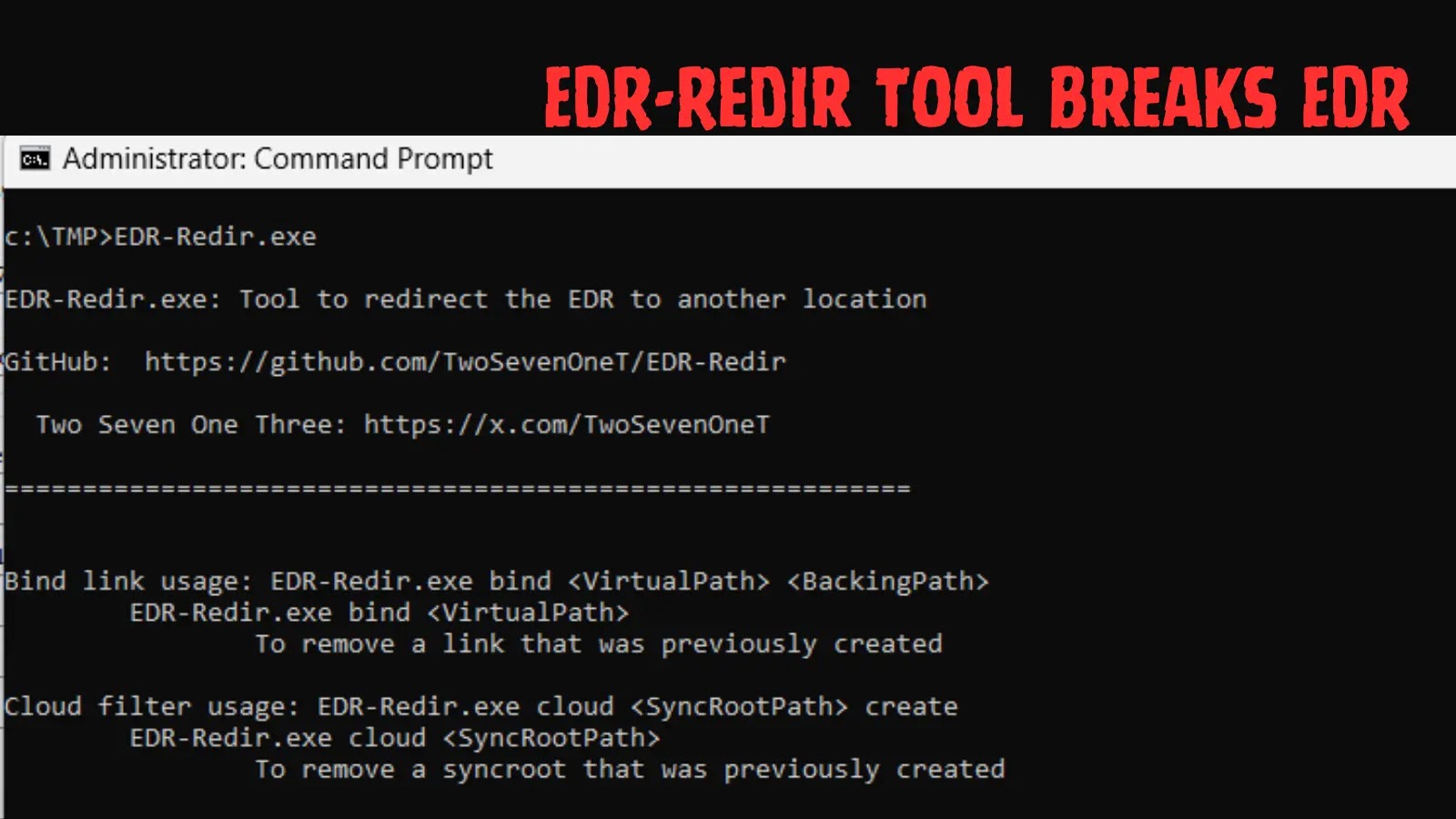
A significant security breach has emerged, involving Feiniu (fnOS) Network Attached Storage (NAS) devices. These systems have become the latest targets of the Netdragon botnet, a sophisticated malware that surfaced in October 2024. The botnet has been exploiting undisclosed vulnerabilities in the fnOS platform to deploy harmful code.
Exploitation of Vulnerabilities
The attack campaign is uniquely aimed at compromising storage infrastructures. Unlike previous random infections, this operation specifically targets high-value hardware. The attackers exploit exposed services on the NAS devices, deploying an HTTP backdoor interface. This access allows them to install a modular malware setup, including a loader and a component for Distributed Denial of Service (DDoS) attacks.
This configuration enables remote execution of commands, turning the infected devices into part of a botnet network. These compromised units are subsequently used to execute large-scale DDoS attacks on various targets. A particularly alarming aspect of this malware is its deletion of a critical private key file, rsa_private_key.pem, posing a severe threat to data integrity.
Widespread Impact
According to analysts at Qi An Xin X Lab, the campaign successfully infiltrated approximately 1,500 devices by January’s end. The impacted devices are widely distributed, with notable concentrations in countries such as China, the United States, and Singapore. The affected industries range from software services to public administration.
The Netdragon botnet’s persistence and evasion techniques are notable. It ensures its survival by creating systemd services in user space and kernel modules in kernel space. This dual approach means that even if one component is removed, the other can persist through a system reboot. Additionally, the malware sabotages the device’s update mechanisms by altering the system’s hosts file to prevent security patches.
Recovery and Prevention Strategies
Netdragon’s ability to remain hidden is enhanced by its use of dynamic key packing to obscure its code, deletion of system logs, and manipulation of process lists. These tactics make detection difficult, particularly during active attacks when it disrupts network monitoring tools to conceal traffic spikes.
Recovery from this infection requires manual intervention, as standard updates are disabled. Users should remove any manipulated firewall rules injected by the malware and delete the malicious kernel module named async_memcpys.ko and the service dockers.service. Restoring the system’s update path by correcting the hosts file and monitoring for the backdoor port 57199 is crucial to prevent reinfection.
For ongoing updates on cybersecurity threats, follow us on Google News, LinkedIn, and X. Ensure to set as a preferred source in Google for real-time information.