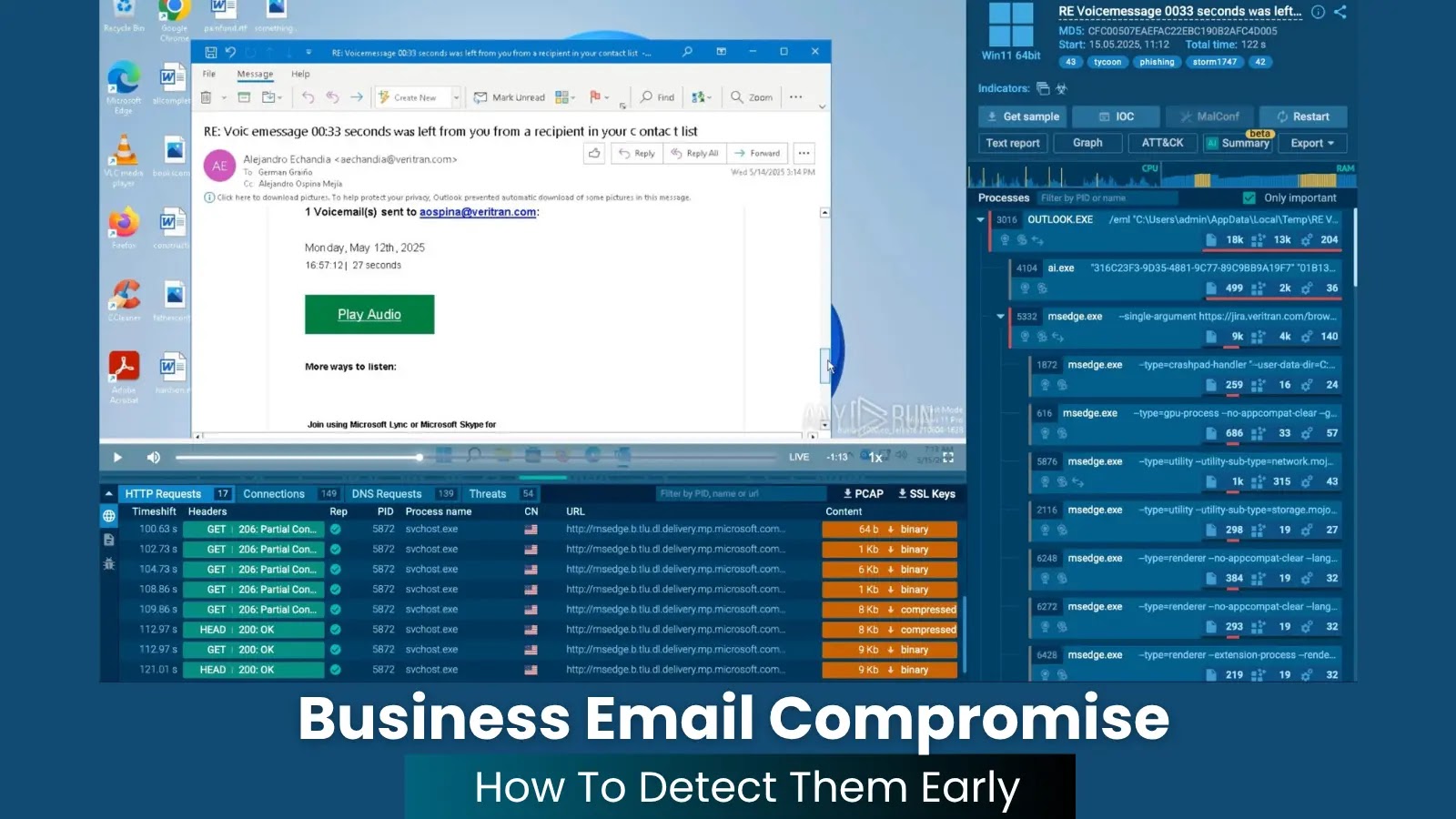
Cybersecurity researchers have uncovered a regarding improvement as malicious actors started exploiting SHELLTER, a industrial anti-virus and endpoint detection response (EDR) evasion framework, to deploy refined malware payloads.
Initially designed for professional penetration testing operations, this framework has been weaponized by cybercriminals since late April 2025, marking a major escalation in evasion capabilities accessible to menace actors.
The illicit use of SHELLTER represents a troubling development the place professional offensive safety instruments are repurposed for malicious actions.
The industrial framework, particularly Elite model 11.0 launched on April 16, 2025, offers superior capabilities permitting malware to bypass trendy safety options by refined obfuscation and evasion methods.
Its polymorphic code era and talent to embed malicious payloads inside professional purposes have made detection considerably more difficult.
Elastic Safety Labs researchers recognized a number of financially motivated campaigns using SHELLTER-protected payloads, together with deployment of infamous info stealers akin to LUMMA, RHADAMANTHYS, and ARECHCLIENT2.
These campaigns primarily focused content material creators and gaming communities by rigorously crafted phishing emails and malicious hyperlinks distributed through YouTube feedback and file-sharing platforms like MediaFire.
All analyzed samples share a constant license expiry timestamp of 2026-04-17 19:17:24.055000, suggesting use of a single illicitly acquired license.
Exercise Timeline (Supply – Elastic)
The distribution technique demonstrates refined social engineering ways, with attackers impersonating professional manufacturers together with Udemy, Skillshare, Pinnacle Studio, and Duolingo.
SHELLTER Unpacker (Supply – Elastic)
Victims are lured into downloading malicious archive information containing SHELLTER-protected executables, usually disguised as promotional content material or software program updates.
Superior Evasion Mechanisms and Technical Implementation
The technical sophistication of SHELLTER’s evasion capabilities represents a major problem for cybersecurity professionals.
The framework employs AES-128 CBC encryption to guard remaining payloads, with encryption keys both embedded immediately inside malware or fetched from attacker-controlled servers.
This dual-key method offers flexibility whereas sustaining sturdy cryptographic safety in opposition to evaluation efforts.
SHELLTER’s most notable characteristic is its implementation of polymorphic junk code insertion, producing legitimate-looking directions that serve no useful objective apart from complicated static evaluation instruments and signature-based detection programs.
Name stack of backdoored file (Supply – Elastic)
The framework makes use of oblique syscalls and name stack corruption methods to bypass user-mode API hooking mechanisms generally employed by EDR options.
These methods contain getting ready the stack with addresses of unpolluted syscall directions from ntdll.dll and utilizing return directions to redirect execution circulate.
The framework’s reminiscence safety mechanisms additional complicate evaluation by runtime encoding and decoding of important code sections.
SHELLTER repeatedly modifies reminiscence web page permissions utilizing features like NtQueryVirtualMemory and NtProtectVirtualMemory, guaranteeing delicate code stays obfuscated when not actively executing.
This dynamic safety scheme, mixed with virtualized atmosphere detection and debugging software identification, creates a number of protection layers in opposition to safety researchers and automatic evaluation programs.
Examine reside malware habits, hint each step of an assault, and make quicker, smarter safety selections -> Strive ANY.RUN now