Professional administrative instruments are more and more changing into the weapon of selection for stylish risk actors aiming to mix in with regular community exercise.
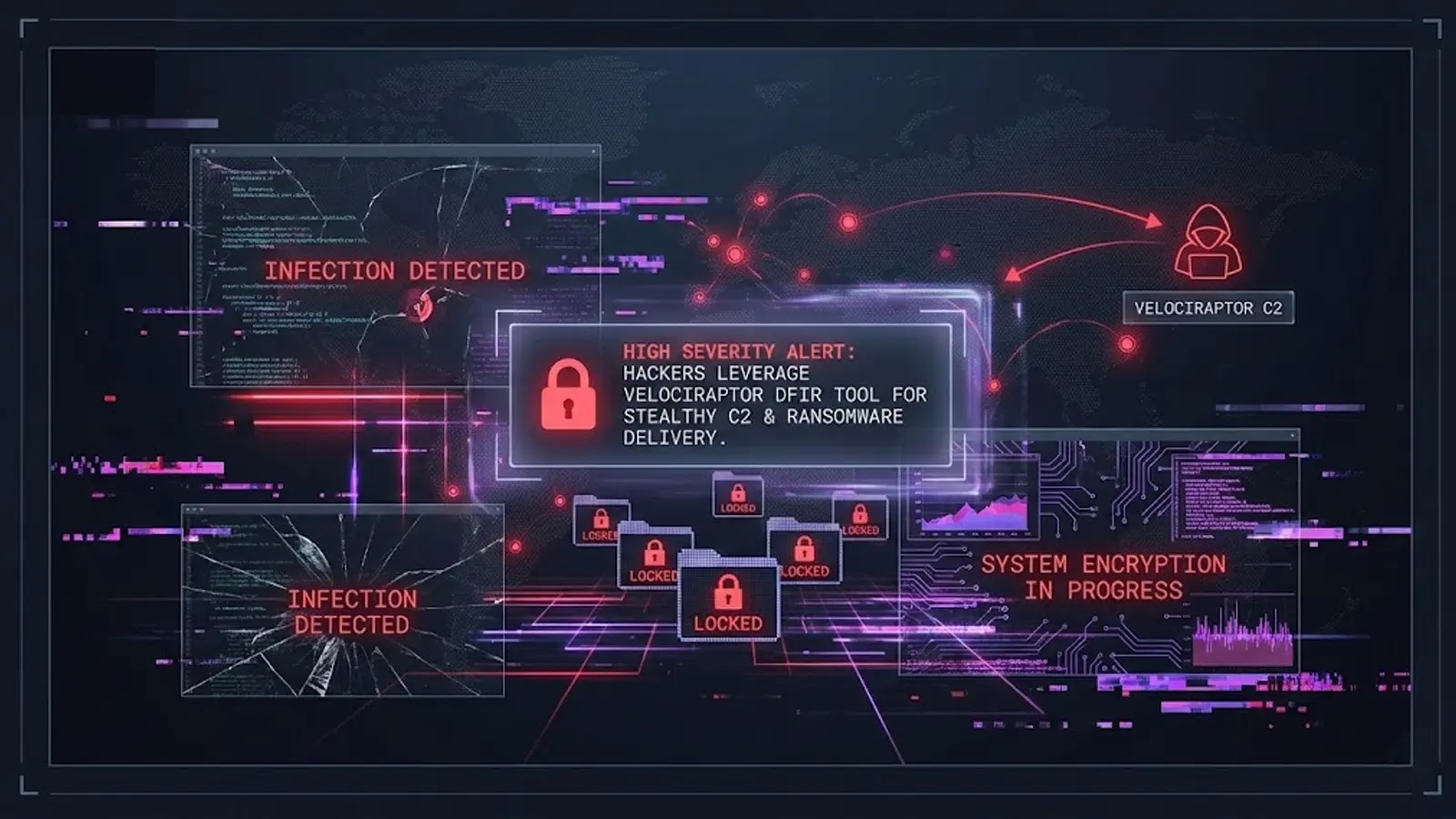
A current marketing campaign has highlighted this harmful development, the place attackers are weaponizing Velociraptor, a broadly revered Digital Forensics and Incident Response (DFIR) device.
By deploying this software program, adversaries successfully set up stealthy Command and Management (C2) channels, permitting them to execute arbitrary instructions and preserve persistent entry to compromised environments with out triggering conventional safety alarms.
The assaults, noticed all through late 2025, leverage crucial vulnerabilities in broadly used enterprise infrastructure, particularly concentrating on Home windows Server Replace Providers (WSUS) and Microsoft SharePoint.
As soon as inside, the actors deploy Velociraptor to facilitate lateral motion and, in confirmed instances, ship the Warlock ransomware.
This dual-use technique complicates detection, because the presence of forensic instruments typically alerts remediation relatively than lively compromise.
Huntress safety analysts recognized this evolving tradecraft after investigating three distinct incidents between September and November.
Their analysis linked particular indicators, such because the hostname DESKTOP-C1N9M, to the financially motivated risk cluster Storm-2603.
The attackers demonstrated a excessive degree of operational safety, using Cloudflare tunnels and digitally signed binaries to bypass endpoint defenses and evade community blocklists.
Exploiting SharePoint for Stealthy Entry
The an infection chain prominently options the exploitation of the “ToolShell” vulnerability chain in Microsoft SharePoint.
Attackers first bypass authentication utilizing CVE-2025-49706 by sending specifically crafted HTTP POST requests to /_layouts/15/ToolPane.aspx. Following this, they chain a secondary distant code execution vulnerability (CVE-2025-49704) to switch default information like begin.aspx into malicious internet shells.
IIS Entry Logs for SharePoint Server (Supply – Huntress)
This illustrates the suspicious IIS logs revealing these unauthorized requests throughout the /_layouts/15/ listing.
As soon as the net shell is lively, the risk actors execute instructions to obtain and set up Velociraptor by way of Home windows Installer. A typical command noticed in these assaults is:
msiexec /q /i
This set up registers Velociraptor as a system service, guaranteeing persistence throughout reboots. Moreover this, the Autorun depicts the creation of this autorun service.
Autorun created for Velociraptor to run as a Home windows service (Supply – Huntress)
To additional entrench their place, the attackers use the compromised Velociraptor occasion to run Base64 encoded PowerShell instructions.
These scripts obtain Visible Studio Code (code.exe) to create outbound tunnels, successfully masking their malicious site visitors inside professional improvement exercise.
VS Code logs for tunnel creation (Supply – Huntress)
The VS Code logs spotlight the occasions generated throughout this tunnel-creation course of, displaying how the actors pivot from forensic device abuse to finish community domination.
Comply with us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most popular Supply in Google.