Microsoft has supplied complete steerage for resolving the widespread Home windows error “The method can not entry the file as a result of it’s being utilized by one other course of.”
This technical difficulty, which continuously frustrates customers making an attempt to delete, transfer, or modify information, can now be systematically recognized and resolved utilizing a number of built-in Home windows utilities and free Microsoft instruments.
The error sometimes happens when a number of purposes try to entry the identical file concurrently, making a lock that stops regular file operations.
Key Takeaways1. Press Win + R, kind resmon, search file title in CPU tab’s Related Handles part to determine blocking processes.2. Set up by way of winget set up Microsoft.Sysinternals.ProcessExplorer, use Ctrl + F to search out and shut file handles.3. Use openfiles /question or deal with.exe to listing processes accessing particular information.4. Microsoft gives complete instruments eliminating want for third-party software program throughout all ability ranges.
Microsoft’s newest documentation, up to date July 14, 2025, outlines three major methodologies for figuring out and resolving these file conflicts, starting from graphical interfaces to command-line options.
Constructed-in Home windows Instruments Provide Options
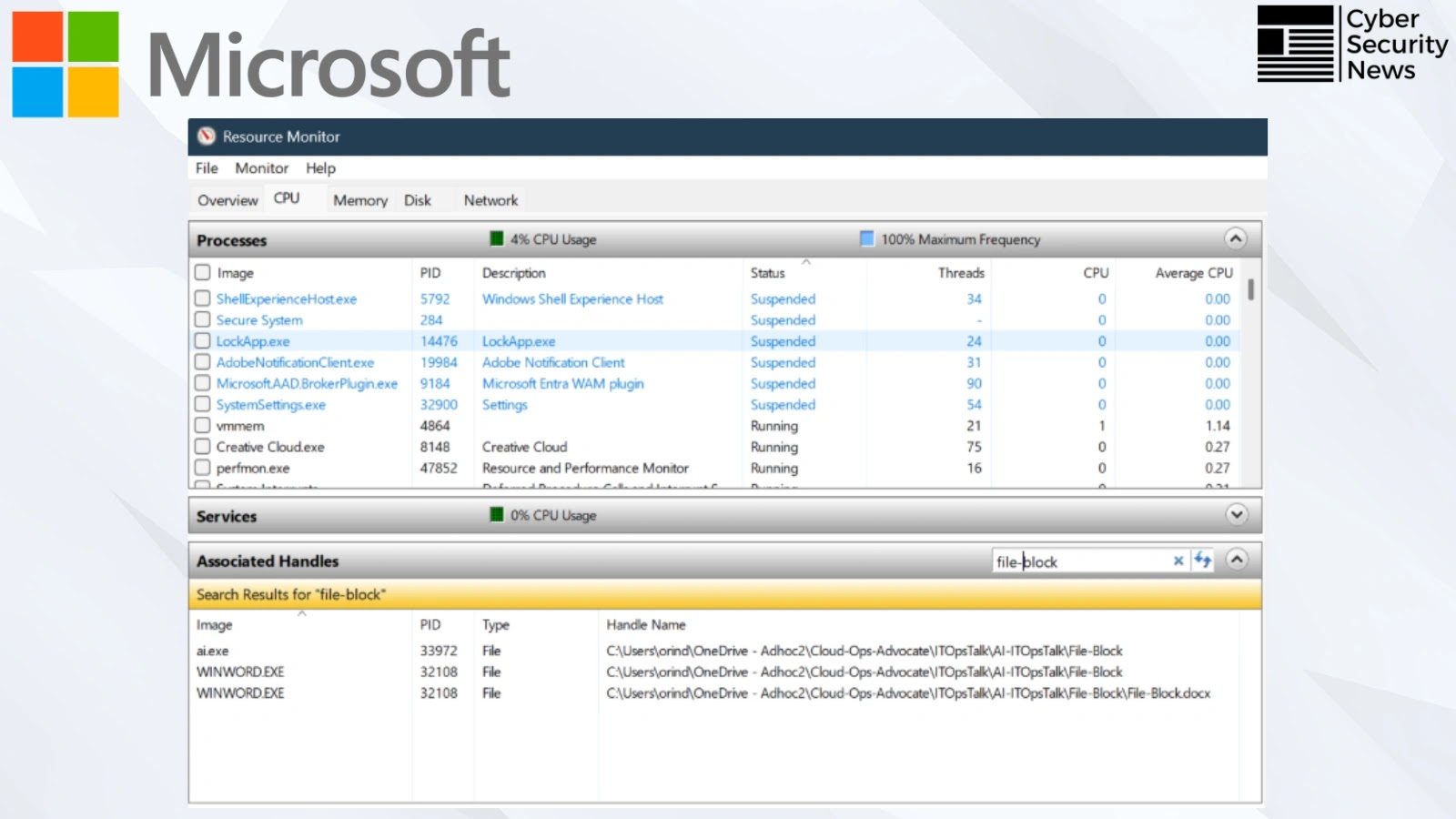
Useful resource Monitor serves as the primary line of protection for troubleshooting file entry conflicts.
Customers can launch this built-in utility by urgent Win + R, typing resmon, and urgent Enter. Throughout the CPU tab’s Related Handles part, directors can seek for particular file or folder names to determine blocking processes.
The device shows important info, together with course of names within the Picture column and Course of IDs (PIDs), enabling customers to terminate problematic processes by way of right-click context menus.
For extra superior evaluation, Microsoft recommends Course of Explorer, a Sysinternals utility accessible by way of the WinGet package deal supervisor.
The set up command winget set up Microsoft.Sysinternals.ProcessExplorer gives system directors with enhanced course of monitoring capabilities.
Course of Explorer’s search performance, accessible by way of Ctrl + F or the Discover menu, permits customers to find particular file handles and optionally shut them immediately from the interface.
Superior Command Line Strategies
Command-line lovers have entry to 2 highly effective utilities for file lock investigation. The openfiles command, executed as openfiles /question in Command Immediate, shows complete details about open information and their related processes.
Nonetheless, this performance requires prior activation utilizing openfiles /native on adopted by a system restart.
Alternatively, the deal with.exe utility from Sysinternals gives fast file lock evaluation with out system configuration modifications.
Accessible by way of winget set up Microsoft.Sysinternals.Deal with, this device accepts particular filename parameters utilizing the syntax deal with.exe to listing all processes at present accessing the goal file.
The documentation additionally acknowledges group suggestions, together with solutions for PowerToys File Locksmith, a shell extension that integrates file lock detection immediately into Home windows Explorer‘s context menu, demonstrating Microsoft’s dedication to increasing troubleshooting choices primarily based on consumer necessities.
These options collectively present Home windows directors and energy customers with complete instruments for diagnosing and resolving file entry conflicts, eliminating the necessity for third-party utilities in most eventualities.
Examine reside malware habits, hint each step of an assault, and make quicker, smarter safety selections -> Attempt ANY.RUN now