Ravie LakshmananJan 17, 2026Law Enforcement / Cybercrime
Ukrainian and German regulation enforcement authorities have recognized two Ukrainians suspected of working for the Russia-linked ransomware-as-a-service (RaaS) group Black Basta.
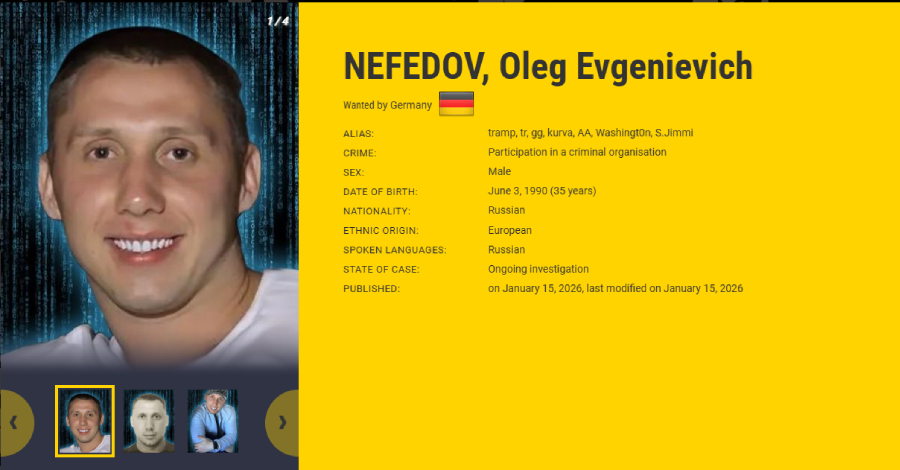
As well as, the group’s alleged chief, a 35-year-old Russian nationwide named Oleg Evgenievich Nefedov (Нефедов Олег Евгеньевич), has been added to the European Union’s Most Needed and INTERPOL’s Pink Discover lists, authorities famous.
“In keeping with the investigation, the suspects specialised in technical hacking of protected techniques and had been concerned in making ready cyberattacks utilizing ransomware,” the Cyber Police of Ukraine mentioned in an announcement.
The company mentioned the accused people functioned as “hash crackers,” who concentrate on extracting passwords from info techniques utilizing specialised software program. As soon as the credential info was obtained, members of the ransomware group broke into company networks and in the end deployed ransomware and extorted cash to get well the encrypted info.
Authorities carried out searches on the defendants’ residences situated in Ivano-Frankivsk and Lviv, permitting them to grab digital storage units and cryptocurrency property.
Black Basta first emerged within the risk panorama in April 2022, and is claimed to have focused greater than 500 corporations throughout North America, Europe, and Australia. The ransomware group is estimated to have earned a whole bunch of thousands and thousands of {dollars} in cryptocurrency from illicit funds.
Early final yr, a yr’s value of inside chat logs from Black Basta leaked on-line, providing a glimpse into the group’s interior workings, its construction and key members, and the varied safety vulnerabilities exploited to realize preliminary entry to organizations of curiosity.
The leaked file additionally unmasked Nefedov as Black Basta’s ringleader, including he goes by numerous aliases, corresponding to Tramp, Trump, GG, and AA. Some paperwork alleged that Nefedov had ties to high-ranking Russian politicians and intelligence companies, together with the FSB and GRU.
Nefedov is believed to have leveraged these connections to guard his operations and evade worldwide justice. A subsequent evaluation from Trellix revealed that Nefedov was capable of safe his freedom regardless of getting arrested in Yerevan, Armenia, in June 2024. His different aliases embrace kurva, Washingt0n, and S.Jimmi. Though Nefedov is claimed to be in Russia, his precise whereabouts are unknown.
Moreover, there may be proof linking Nefedov to Conti, a now-defunct group that sprang forth in 2020 as a successor to Ryuk. In August 2022, the U.S. State Division introduced a $10 million reward for info associated to 5 people related to the Conti ransomware group. They included Goal, Tramp, Dandis, Professor, and Reshaev.
It is value mentioning right here that Black Basta surfaced as an autonomous group, alongside BlackByte and KaraKurt, following the retirement of the Conti model in 2022. Different members joined teams like BlackCat, Hive, AvosLocker, and HelloKitty, all of which at the moment are now not lively.
“He served as the top of the group. As such, he determined who or which organisations could be the targets of assaults, recruited members, assigned them duties, took half in ransom negotiations, managed the ransom obtained by extortion, and used it to pay the members of the group,” Germany’s Federal Legal Police Workplace (BKA or Bundeskriminalamt) mentioned.
The leaks have led to Black Basta’s obvious demise, with the group remaining silent after February and taking down its knowledge leak later that month. However with ransomware gangs recognized to close down, rebrand, and reemerge underneath a unique identification, it will not be shocking if members of the erstwhile prison syndicate pivot to different ransomware teams or type new ones.
Certainly, per studies from ReliaQuest and Pattern Micro, it is suspected that a number of of the previous Black Basta associates might need migrated to the CACTUS ransomware operation – an evaluation primarily based on the truth that there was a large spike in organizations named on the latter’s knowledge leak website in February 2025, coinciding with Black Basta’s website going offline.