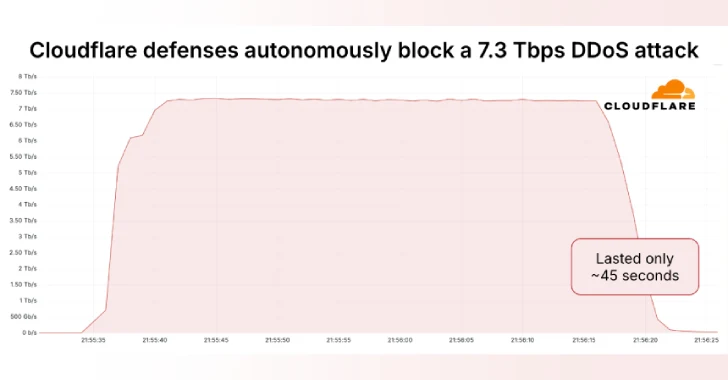
Cloudflare on Thursday mentioned it autonomously blocked the biggest ever distributed denial-of-service (DDoS) assault ever recorded, which hit a peak of seven.3 terabits per second (Tbps).
The assault, which was detected in mid-Could 2025, focused an unnamed internet hosting supplier.
“Internet hosting suppliers and important Web infrastructure have more and more turn out to be targets of DDoS assaults,” Cloudflare’s Omer Yoachimik mentioned. “The 7.3 Tbps assault delivered 37.4 terabytes in 45 seconds.”
Earlier this January, the online infrastructure and safety firm mentioned it had mitigated a 5.6 Tbps DDoS assault geared toward an unnamed web service supplier (ISP) from Jap Asia. The assault originated from a Mirai-variant botnet in October 2024.
Then in April 2025, Cloudflare revealed it defended in opposition to an enormous 6.5 Tbps flood that doubtless emanated from Eleven11bot, a botnet comprising roughly 30,000 webcams and video recorders. The hyper-volumetric assault lasted about 49 seconds.
The 7.3 Tbps DDoS assault, compared, carpet-bombed a mean of 21,925 vacation spot ports of a single IP tackle owned and used the internet hosting supplier, hitting a crest of 34,517 vacation spot ports per second.
The multi-vector assault originated from an analogous distribution of supply ports and has been recognized as a mix of UDP flood, QOTD reflection assault, echo reflection assault, NTP reflection assault, Mirai UDP flood assault, portmap flood, and RIPv1 amplification assault. The UDP flood accounted for 99.996% of the assault visitors.
Cloudflare additionally identified that the assault got here from over 122,145 supply IP addresses spanning 5,433 Autonomous Techniques (AS) throughout 161 nations. The highest sources of assault visitors included Brazil, Vietnam, Taiwan, China, Indonesia, Ukraine, Ecuador, Thailand, the US, and Saudi Arabia.
“The common variety of distinctive supply IP addresses per second was 26,855 with a peak of 45,097,” Yoachimik mentioned.
“Telefonica Brazil (AS27699) accounted for the biggest portion of the DDoS assault visitors, accountable for 10.5% of the whole. Viettel Group (AS7552) follows intently with 9.8%, whereas China Unicom (AS4837) and Chunghwa Telecom (AS3462) contributed 3.9% and a pair of.9% respectively. China Telecom (AS4134) accounted for two.8% of the visitors.”
The disclosure comes because the QiAnXin XLab staff mentioned the DDoS botnet tracked as RapperBot was behind an assault geared toward synthetic intelligence (AI) firm DeepSeek in February 2025, and that the most recent samples of the malware trying to extort victims to pay them “safety charges” to keep away from being focused by DDoS assaults sooner or later.
China, the US, Israel, Mexico, the UK, Greece, Iran, Australia, Malaysia, and Thailand are the first nations the place gadgets contaminated by RapperBot are positioned. The botnet is thought to be energetic since 2022.
RapperBot campaigns are identified to focus on routers, network-attached storage gadgets, and video recorders with default weak passwords or firmware vulnerabilities to acquire preliminary entry, and drop malware that may set up contact with a distant server over DNS TXT information to fetch DDoS assault instructions.
The malware additionally makes use of customized encryption algorithms to encrypt the TXT information and command-and-control (C2) domains used.
“Since March, its assault conduct has been considerably energetic, with a mean of greater than 100 assault targets per day and greater than 50,000 bots noticed,” the Chinese language safety vendor mentioned.
“RapperBot’s assault targets are everywhere in the fields of varied industries, together with public administration, social safety and social organizations, Web platforms, manufacturing, monetary companies, and so forth.”
Discovered this text attention-grabbing? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.