Notepad++ has fortified its software update mechanism with a newly released security update, addressing vulnerabilities exploited by a Chinese cyber threat group. The latest version, 8.9.2, introduces a ‘double lock’ strategy to ensure a more rigorous and secure update process.
Enhanced Update Security
The update process for Notepad++ has been significantly improved by verifying both the installer downloaded from GitHub and the signed XML from the update server at notepad-plus-plus[.]org. This measure, detailed by maintainer Don Ho, aims to prevent exploitation by unauthorized entities.
Additionally, significant changes have been made to WinGUp, Notepad++’s auto-updater, to eliminate potential security risks. These changes include removing the libcurl.dll to mitigate DLL side-loading threats and disabling two unsecured cURL SSL options, namely CURLSSLOPT_ALLOW_BEAST and CURLSSLOPT_NO_REVOKE. Moreover, plugin management execution is now restricted to programs signed with the same certificate as WinGUp.
Addressing Critical Vulnerabilities
The update also resolves a high-severity vulnerability, identified as CVE-2026-25926, which scored 7.3 on the CVSS scale. This vulnerability could potentially allow arbitrary code execution through an unsafe search path when Windows Explorer launches without a defined executable path.
Ho explained that this flaw could be exploited if an attacker manages to control the process’s working directory, potentially leading to malicious execution within the running application.
Response to Previous Attacks
This development follows a recent disclosure by Notepad++ regarding a breach at the hosting provider level, which allowed attackers to hijack update traffic starting June 2025. By December 2025, it was discovered that certain user requests were redirected to malicious servers, resulting in the deployment of a compromised update.
Security firms Rapid7 and Kaspersky identified the tampered updates as a vector for delivering the Chrysalis backdoor, a novel threat attributed to the China-based hacking group Lotus Panda. This supply chain attack was registered under CVE-2025-15556, with a CVSS score of 7.7.
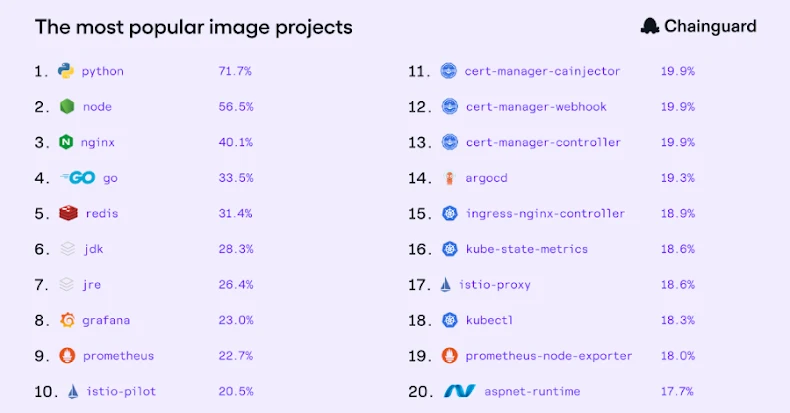
Notepad++ users are urged to upgrade to version 8.9.2 immediately and ensure that installations are sourced from the official website to safeguard against these threats.