Might 20, 2025Ravie LakshmananMalware / Cyber Espionage
Excessive-level authorities establishments in Sri Lanka, Bangladesh, and Pakistan have emerged because the goal of a brand new marketing campaign orchestrated by a menace actor often known as SideWinder.
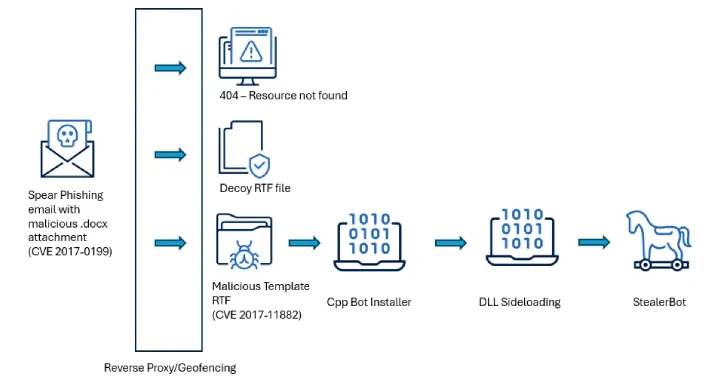
“The attackers used spear phishing emails paired with geofenced payloads to make sure that solely victims in particular international locations acquired the malicious content material,” Acronis researchers Santiago Pontiroli, Jozsef Gegeny, and Prakas Thevendaran mentioned in a report shared with The Hacker Information.
The assault chains leverage spear-phishing lures as a place to begin to activate the an infection course of and deploy a recognized malware known as StealerBot. It is price mentioning that the modus operandi is per latest SideWinder assaults documented by Kaspersky in March 2025.
A few of the targets of the marketing campaign, per Acronis, embrace Bangladesh’s Telecommunication Regulatory Fee, Ministry of Defence, and Ministry of Finance; Pakistan’s Directorate of Indigenous Technical Growth; and Sri Lanka’s Division of Exterior Assets, Division of Treasury Operations, Ministry of Defence, and Central Financial institution.
The assaults are characterised by way of years-old distant code execution flaws in Microsoft Workplace (CVE-2017-0199 and CVE-2017-11882) as preliminary vectors to deploy malware able to sustaining persistent entry in authorities environments throughout South Asia.
The malicious paperwork, when opened, set off an exploit for CVE-2017-0199 to ship next-stage payloads which might be liable for putting in StealerBot via DLL side-loading strategies.
One noteworthy tactic adopted by SideWinder is that the spear-phishing emails are coupled with geofenced payloads to make sure that solely victims assembly the focusing on standards are served the malicious content material. Within the occasion the sufferer’s IP deal with doesn’t match, an empty RTF file is shipped as a substitute as a decoy.
The malicious payload is an RTF file that weaponizes CVE-2017-11882, a reminiscence corruption vulnerability within the Equation Editor, to launch a shellcode-based loader that runs the StealerBot malware.
StealerBot, in keeping with Kaspersky, is a .NET implant that is engineered to drop extra malware, launch a reverse shell, and acquire a variety of knowledge from compromised hosts, together with screenshots, keystrokes, passwords, and information.
“SideWinder has demonstrated constant exercise over time, sustaining a gradual tempo of operations with out extended inactivity — a sample that displays organizational continuity and sustained intent,” the researchers mentioned.
“A more in-depth evaluation of their techniques, strategies, and procedures (TTPs) reveals a excessive diploma of management and precision, making certain that malicious payloads are delivered solely to rigorously chosen targets, and sometimes just for a restricted time.”
Discovered this text attention-grabbing? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.