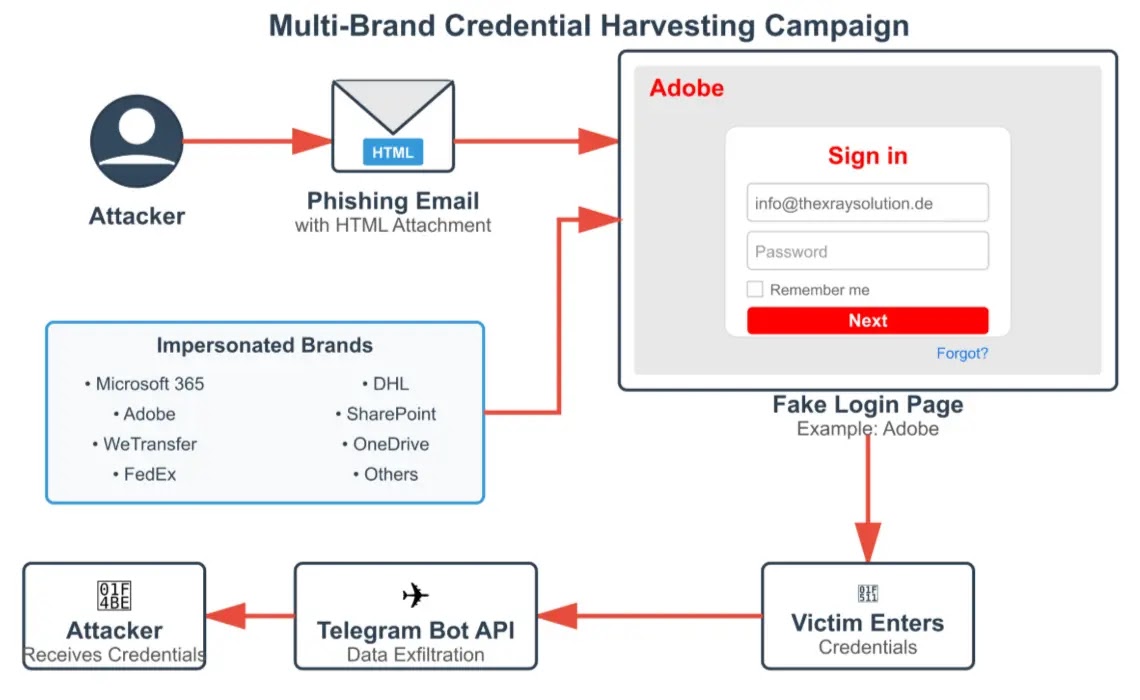
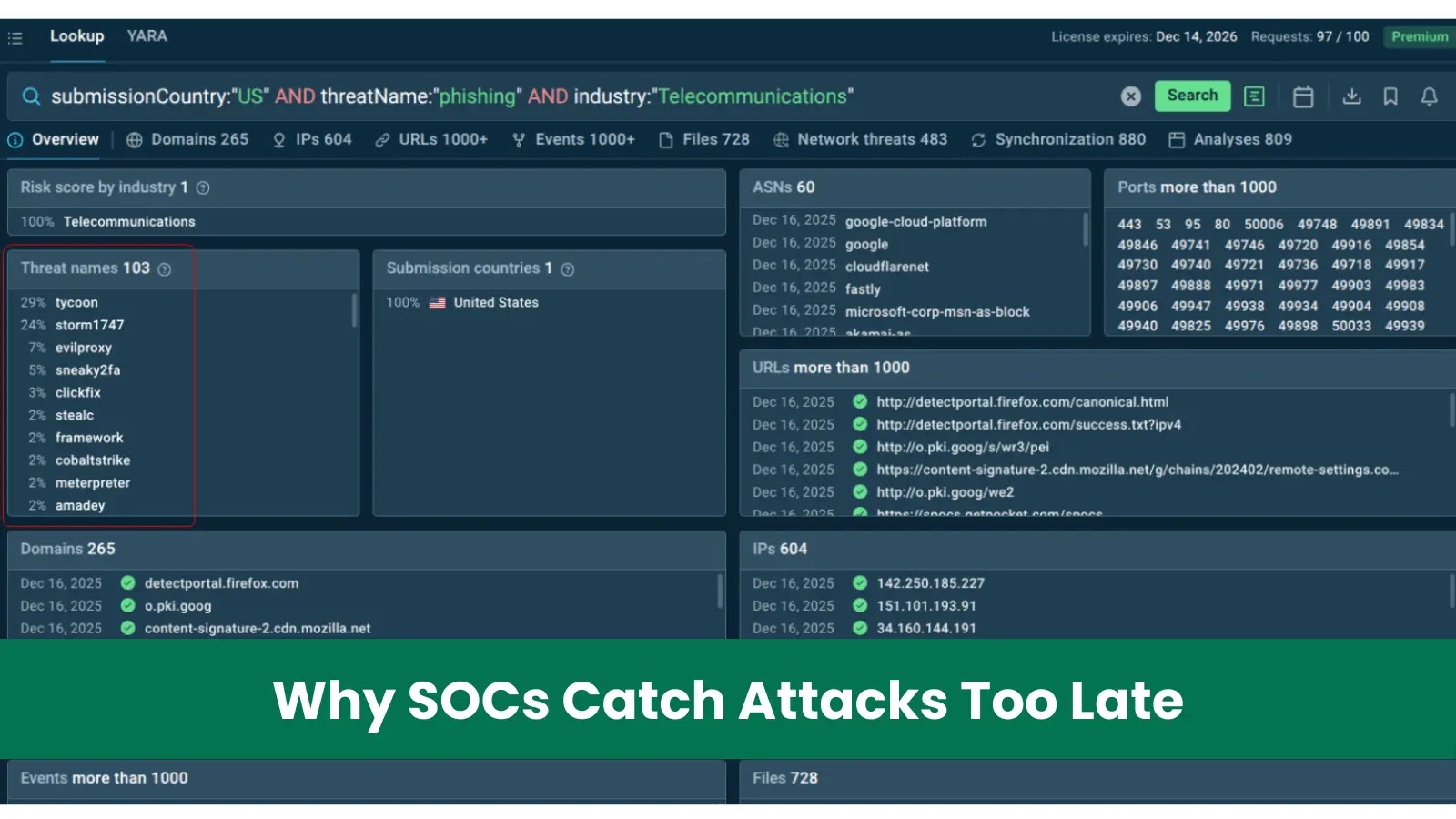
A world ecosystem of refined rip-off operations has emerged, focusing on susceptible populations by way of impersonation ways and fraudulent monetary support guarantees.
The marketing campaign, dubbed “Vulnerability Vultures,” primarily focuses on older adults who signify profitable targets for risk actors.
In response to the FBI’s Web Crime Criticism Heart, the 60-plus age group filed the best variety of complaints in 2024, with losses totaling $4.8 billion, practically double the following highest class.
Federal Commerce Fee information additional reveals that adults 70 years or older expertise considerably greater median greenback losses in comparison with youthful demographics.
The scammers leverage main social media platforms as preliminary contact factors, subsequently redirecting victims to fraudulent web sites or personal messaging channels the place they harvest monetary particulars and delicate private data.
These operations show geographic variety, with proof suggesting operators primarily based in Nigeria, South Asia, and america.
The risk actors intentionally goal people prone to provides of bodily or monetary advantages, together with each older adults and former rip-off victims who could also be searching for restitution.
Graphika analysts recognized that the cross-platform construction of those rip-off operations allows scalability, anonymity, and efficient evasion of platform moderation measures.
The risk actors deploy inauthentic personas and manipulated media to impersonate trusted figures, establishments, and types such because the FBI and established information organizations.
By incorporating AI-generated audio, cloned web sites, and repurposed genuine content material, the scammers create convincing simulations of legitimacy and authority that deceive even cautious victims.
Assault Methodology and Social Engineering Techniques
The operations observe a constant three-stage assault sample: constructing belief by way of authoritative impersonation, ushering victims to off-platform communication channels, and extracting private or monetary information by way of registration varieties for non-existent reduction applications.
These schemes function at excessive quantity, deploying an identical short-lived ads, AI automation, paid promotion, and disposable accounts that keep operational persistence regardless of ongoing enforcement efforts from platform suppliers and regulation enforcement companies.
Observe us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most well-liked Supply in Google.