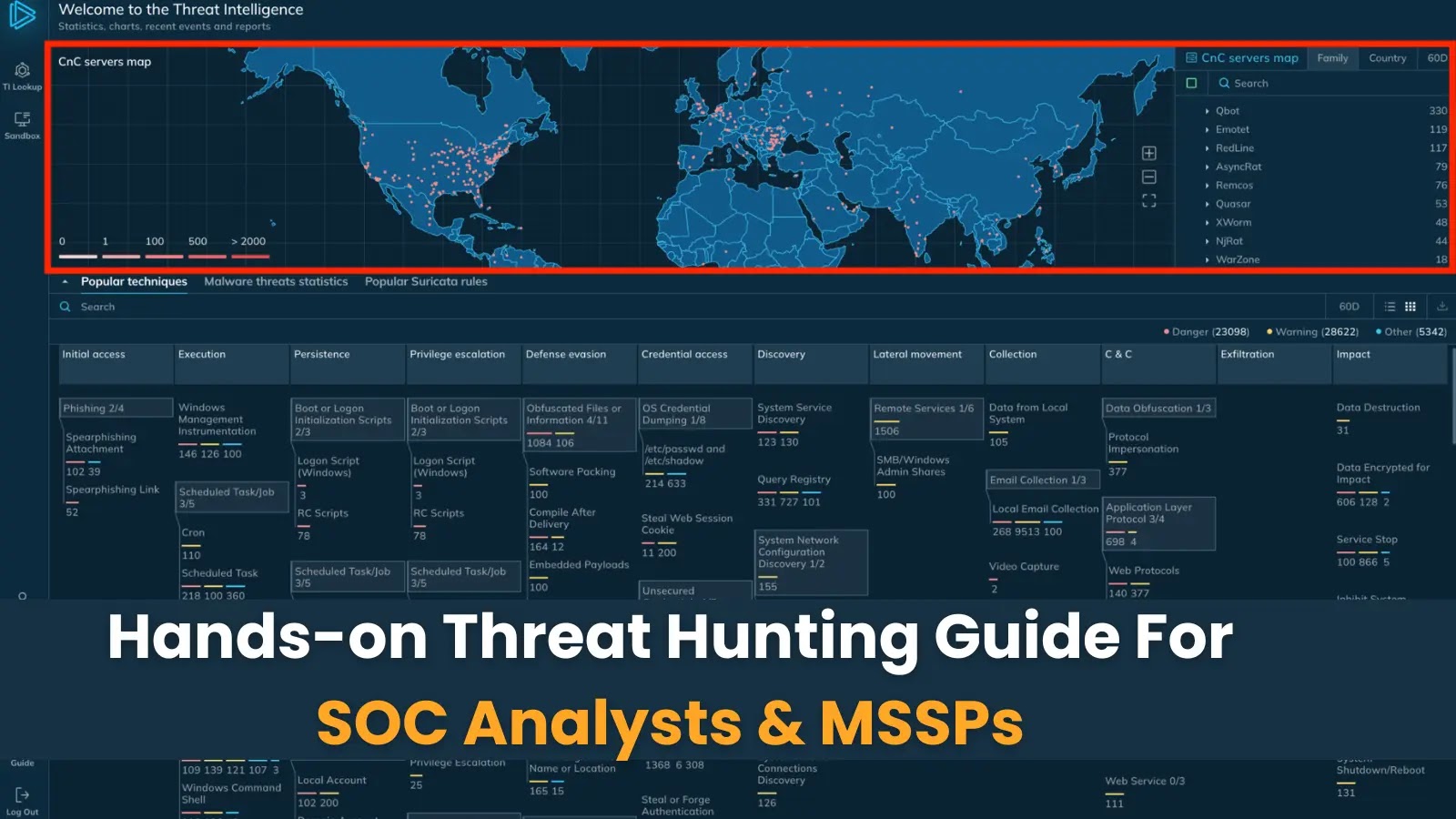
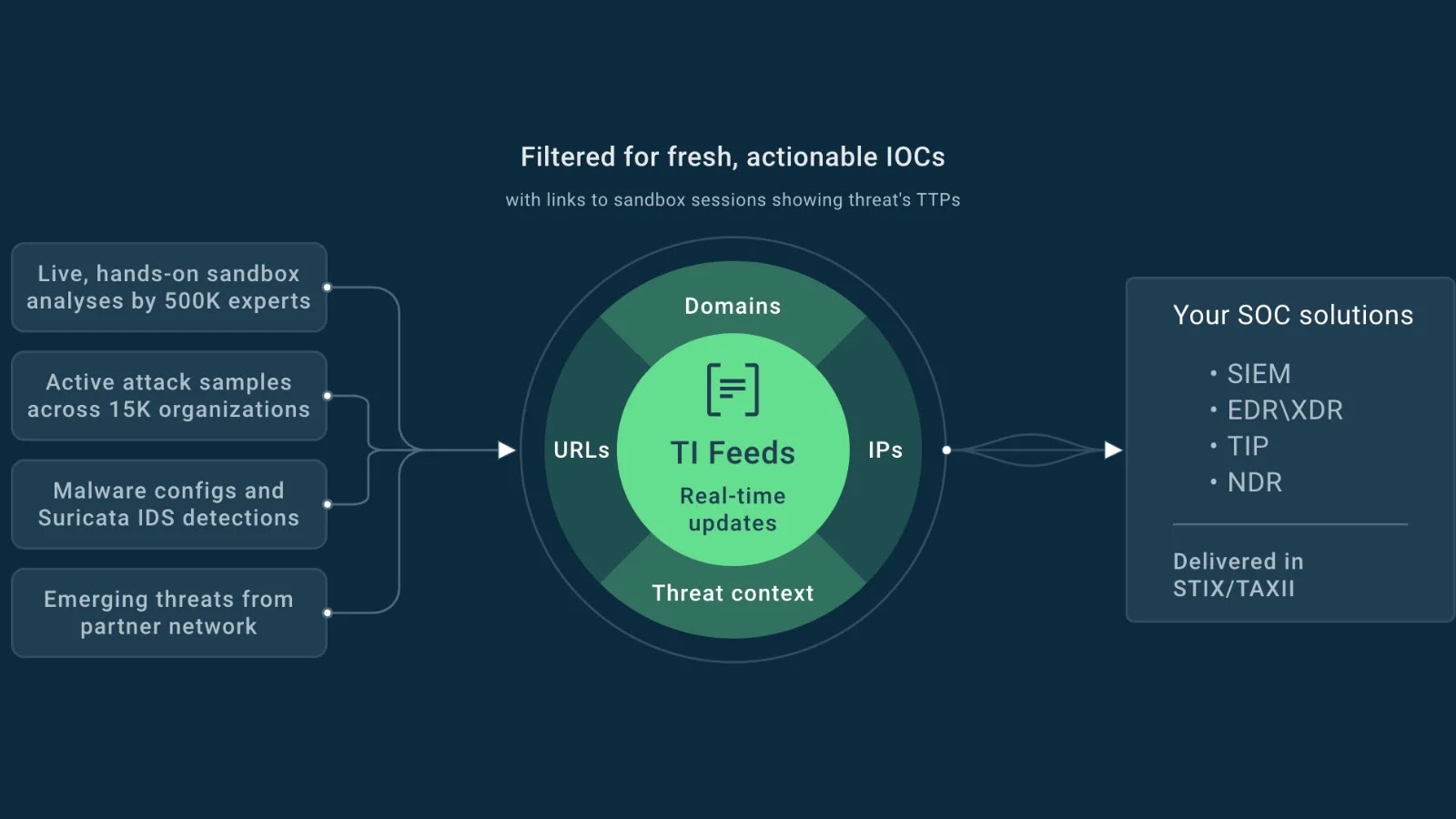
Over 10,000 Fortinet firewalls worldwide stay weak to CVE-2020-12812, a multi-factor authentication (MFA) bypass flaw disclosed over 5 and a half years in the past.
Shadowserver just lately added the difficulty to its day by day Susceptible HTTP Report, highlighting persistent publicity amid energetic exploitation confirmed by Fortinet in late 2025.
CVE-2020-12812 stems from improper authentication in FortiOS SSL VPN portals, affecting variations 6.4.0, 6.2.0 via 6.2.3, and 6.0.9 and earlier. Attackers can bypass the second authentication issue, usually FortiToken, by merely altering the case of a professional username, corresponding to altering “consumer” to “Person,” throughout login.
This happens because of mismatched case sensitivity: FortiGate treats native usernames as case-sensitive, whereas LDAP servers (like Energetic Listing) typically ignore case, permitting authentication by way of group membership with out prompting for MFA.
The flaw carries a CVSS v3.1 base rating of seven.5 (Excessive), with community accessibility, low complexity, and potential for confidentiality, integrity, and availability impacts. It was added to CISA’s Identified Exploited Vulnerabilities catalog in 2021 after ransomware actors leveraged it.
In December 2025, Fortinet issued a PSIRT advisory (FG-IR-19-283 replace) detailing “latest abuse” of the vulnerability within the wild, tied to particular configurations: native FortiGate customers with MFA enabled, linked to LDAP, and belonging to LDAP teams mapped to authentication insurance policies for SSL VPN, IPsec, or admin entry. Menace actors exploited this to achieve unauthorized inner community entry, prompting Fortinet to induce fast checks and patches.
Shadowserver’s scans affirm the flaw’s persistence, scanning for weak HTTP providers on uncovered ports.
Shadowserver’s dashboard reveals over 10,000 weak situations as of early January 2026. The USA dominates with 1.3K uncovered firewalls, adopted by Thailand (909), Taiwan (728), Japan (462), and China (462).
A world map visualization exhibits dense clusters in North America, East Asia, and Europe, with lighter publicity in Africa and components of South America.
High CountriesVulnerable CountUnited States1.3KThailand909Taiwan728Japan462China462
Fortinet recommends upgrading to fastened FortiOS variations (6.0.10+, 6.2.4+, 6.4.1+) and verifying configurations to keep away from hybrid local-LDAP MFA setups.
Disable pointless SSL VPN publicity, implement least privilege, and monitor logs for case-variant login makes an attempt. Organizations ought to subscribe to Shadowserver experiences for tailor-made alerts and run their Susceptible HTTP scans promptly.
This ongoing menace underscores the dangers posed by legacy vulnerabilities in enterprise firewalls, which might allow ransomware or lateral motion inside breached networks.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.