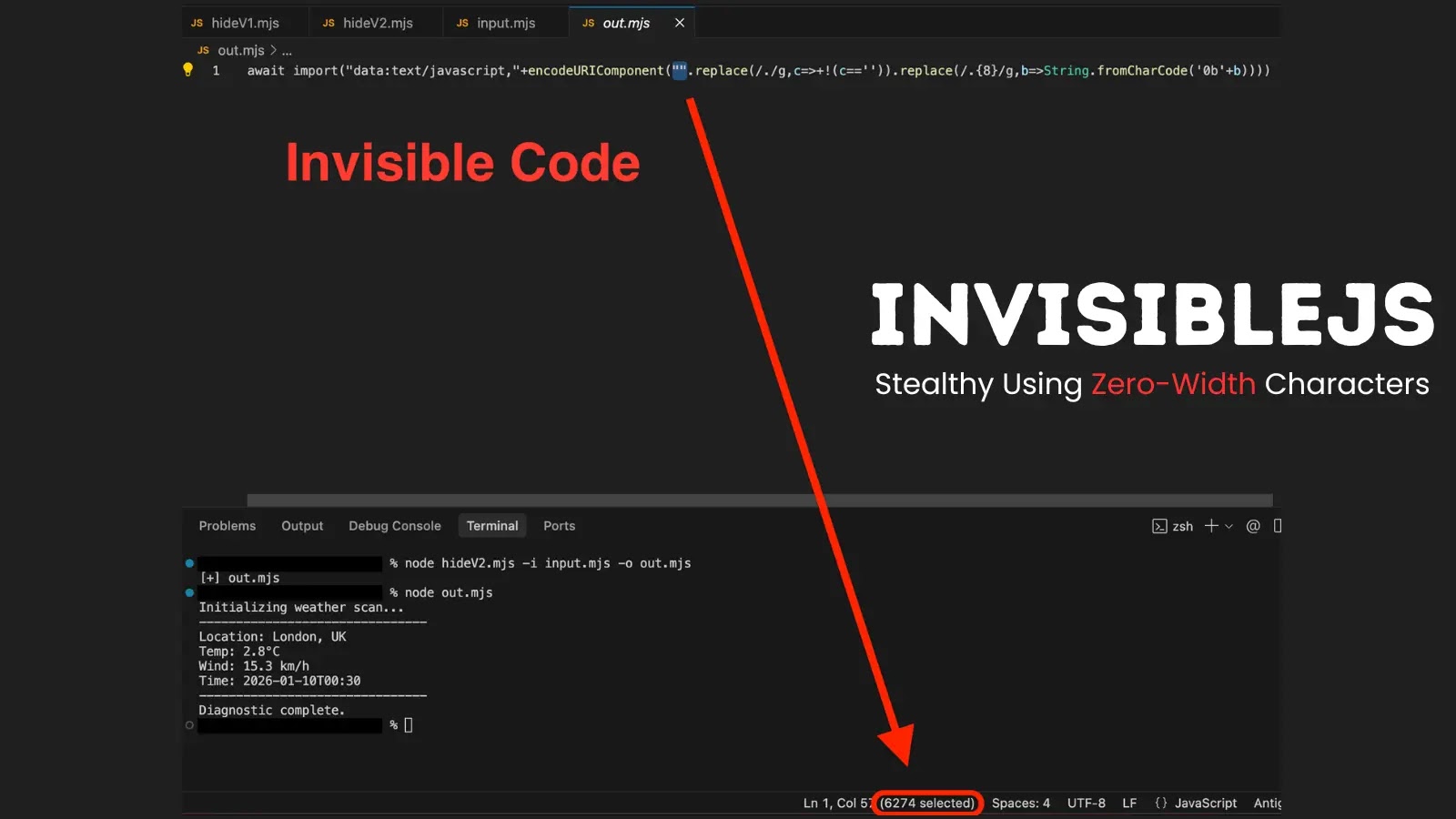
InvisibleJS, a brand new open-source software that conceals JavaScript code utilizing invisible zero-width Unicode characters, raises alarms about potential misuse in malware campaigns.
InvisibleJS, hosted on GitHub by developer With alias oscarmine, employs steganography to embed supply code into seemingly clean recordsdata. The method converts JavaScript into binary strings, mapping 0s to Zero Width House (U+200B) and 1s to Zero Width Non-Joiner (U+200C).
A small bootstrap loader then decodes and runs the hidden payload at runtime, making the code invisible to the bare eye in editors like VS Code.
Two Variations for Totally different Environments
The repository presents Model 1 (Traditional with eval), supreme for CommonJS and legacy Node.js setups, supporting require and module.exports natively.
Model 2 (Trendy with import) targets ES Modules, utilizing dynamic await import() for top-level await and exports, although it requires .mjs recordsdata or “sort”: module configuration.
Hiding code is easy by way of CLI:
Model 1: node hideV1.mjs -i enter.js -o hidden.js
Model 2: node hideV2.mjs -i enter.js -o hidden.js
Execution follows with node hidden.js, producing regular output regardless of the clean look.
FeatureVersion 1 (eval)Model 2 (import)Invisibility100percent100percentCommonJS SupportNativeLimitedESM SupportNoFullTop-Degree AwaitNoYesExecutionSynchronousAsynchronousDecoder LengthShortLong
This method echoes prior zero-width JS proofs-of-concept relationship again to 2018, now weaponized in phishing assaults. Attackers have abused related Unicode obfuscation utilizing Hangul characters for binary to cover payloads in scripts, evading scanners with anti-debug checks.
InvisibleJS might amplify such threats, enabling stealthy malware loaders in Node.js environments or net apps, complicating menace detection.
As obfuscation instruments proliferate, safety groups should improve Unicode-aware scanning and behavioral evaluation. Whereas pitched experimentally, InvisibleJS underscores the dual-use nature of coding improvements in cybersecurity.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.