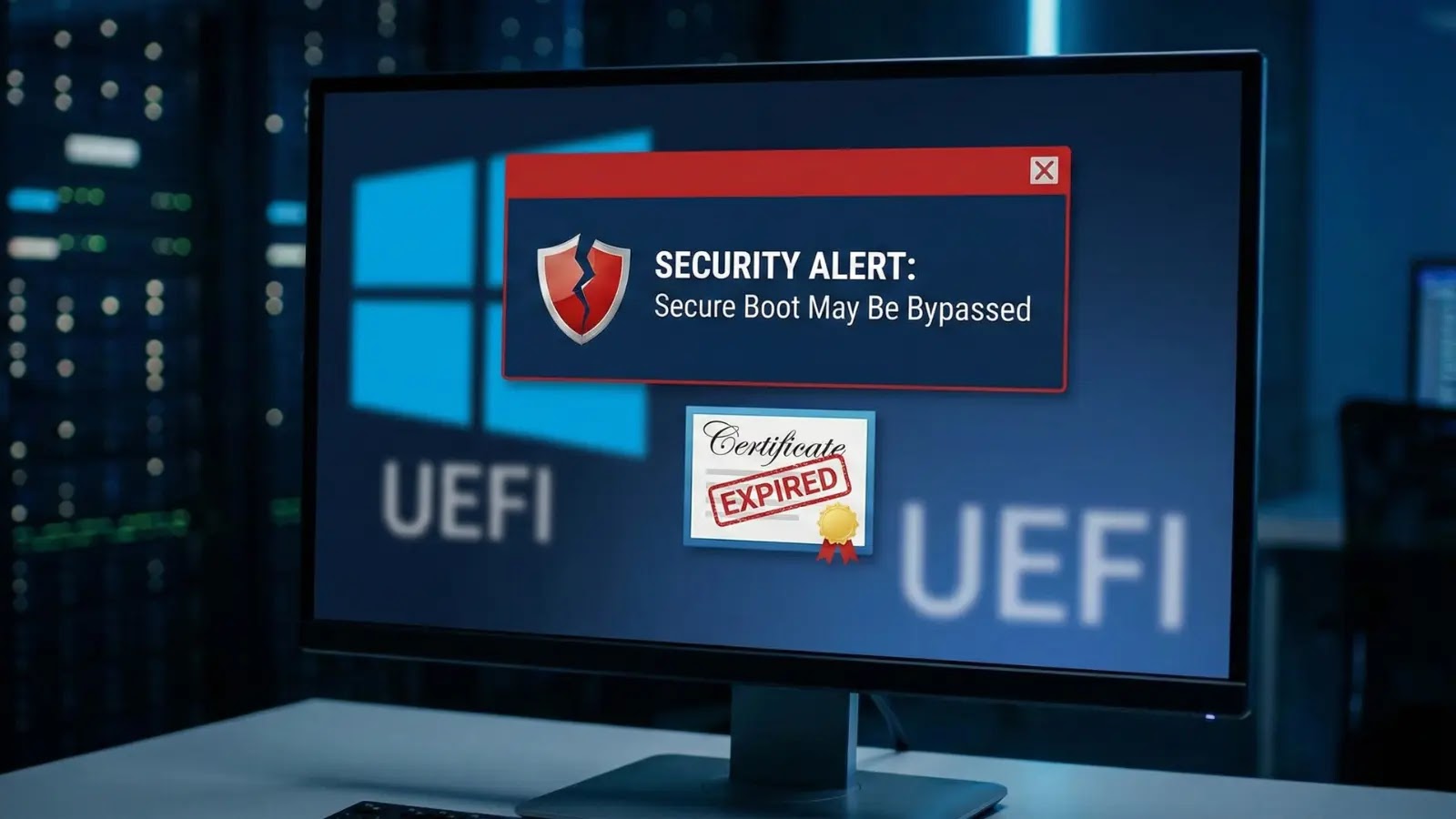
Microsoft has addressed a essential safety characteristic bypass vulnerability in Home windows Safe Boot certificates, tracked as CVE-2026-21265, by way of its January 2026 Patch Tuesday updates.
The flaw stems from expiring 2011-era certificates that underpin Safe Boot’s belief chain, probably permitting attackers to disrupt boot integrity if unpatched.
Rated Vital with a CVSS v3.1 base rating of 6.4, the difficulty requires native entry, excessive privileges, and excessive assault complexity, making exploitation much less probably.msrc.microsoft+4
CVE-2026-21265 arises as a result of Microsoft certificates saved in UEFI KEK and DB are nearing expiration dates in mid-2026, risking Safe Boot failure with out updates.
Firmware defects within the OS’s certificates replace mechanism can disrupt the belief chain, compromising Home windows Boot Supervisor and third-party loaders. Publicly disclosed however not but exploited within the wild, Microsoft urges instant deployment of 2023 substitute certificates.
Three key 2011 certificates have to be renewed to maintain Safe Boot:
Certificates AuthorityLocationPurposeExpiration DateMicrosoft Company KEK CA 2011KEKSigns updates to DB and DBX06/24/2026Microsoft Company UEFI CA 2011DBSigns third occasion boot loaders, Choice ROMs06/27/2026Microsoft Home windows Manufacturing PCA 2011DBSigns the Home windows Boot Manager10/19/2026
Failure to replace exposes gadgets to boot-time assaults, as famous in Microsoft’s November 2025 advisory.
Affected Methods and Patches
Patches goal legacy Home windows Server and extended-support editions, all marked as buyer motion required.
ProductKB ArticleBuild NumberUpdate TypeWindows Server 2012 R2 (Core)50736966.3.9600.22968Monthly RollupWindows Server 2012 R250736966.3.9600.22968Monthly RollupWindows Server 2012 (Core)50736986.2.9200.25868Monthly RollupWindows Server 201250736986.2.9200.25868Monthly RollupWindows Server 2016 (Core)507372210.0.14393.8783Security UpdateWindows Server 2016507372210.0.14393.8783Security UpdateWindows 10 Model 1607 x64507372210.0.14393.8783Security UpdateWindows 10 Model 1607 x86507372210.0.14393.8783Security Replace
Organizations with IT-managed or Microsoft-managed updates ought to prioritize deployment. Confirm firmware compatibility to keep away from post-patch boot points.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.