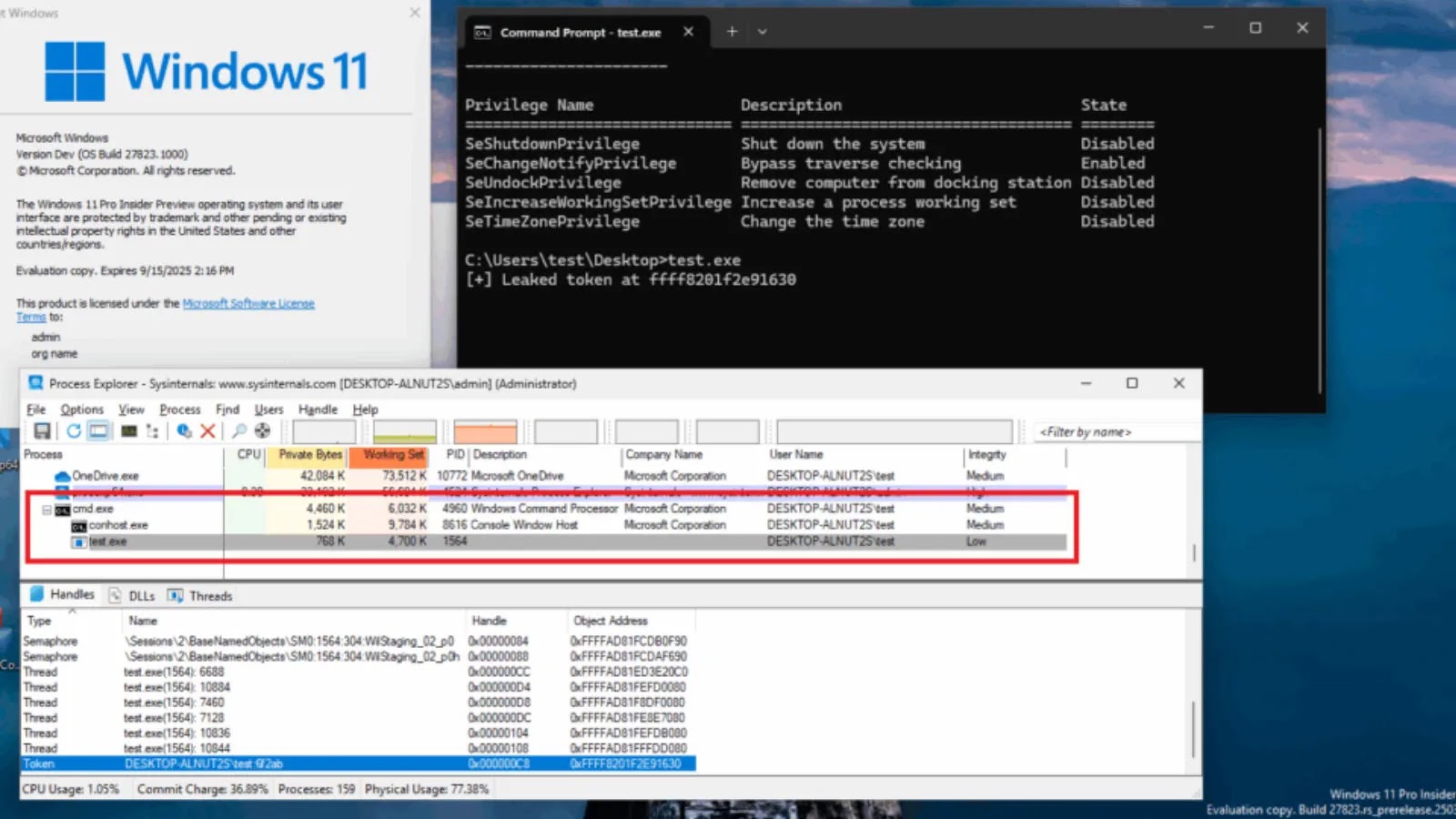
OpenClaw has rolled out version 2026.2.12, marking a significant enhancement in the security of its AI agent platform. This release addresses more than 40 vulnerabilities, reinforcing various components including hooks, browser controls, scheduling, messaging channels, and gateway security.
Enhanced Security Measures
The central aim of this update is to provide defense-in-depth, particularly in the light of previous concerns around exposed OpenClaw agents and remote code execution (RCE) vulnerabilities. A strict SSRF deny policy is now enforced for URL-based input requests, with additional measures like hostname allowlists and per-request URL limits to thwart potential internal network probes.
Moreover, outputs from browsers and web tools are treated with caution, being wrapped in structured metadata before processing to mitigate the risk of prompt-injection attacks. Hooks and webhooks have also been fortified, with secret comparisons now employing constant-time checks and per-client rate limiting to deter brute-force attempts.
Key Component Improvements
The update introduces several component-specific enhancements. Gateway and OpenResponse components now include SSRF protection with strict URL allowlists and request limits. Browser control has been bolstered with mandatory authentication, and the scheduler (cron) has been improved to prevent job skips and duplicates.
Messaging channels such as Telegram, WhatsApp, Slack, Signal, and Discord have seen improvements in security and functionality. Additionally, the release packages now feature signed Mac packages with SHA-256 verification to ensure integrity.
Impact and Future Outlook
With these comprehensive updates, OpenClaw addresses critical vulnerabilities such as unauthenticated tampering and unauthorized access. The mandatory authentication for loopback browser control now significantly reduces the risk of RCE and token theft.
Reliability has also been improved, notably in the cron scheduler, which now correctly re-arms timers and prevents job blocking. Gateway updates ensure safe session handling, while WebSocket limits have been increased to accommodate larger data exchanges.
OpenClaw 2026.2.12 establishes a robust security baseline crucial for operators in the current threat landscape. Prompt deployment is advised to safeguard systems against potential exploits. Stay informed with the latest cybersecurity updates by following us on Google News, LinkedIn, and X.