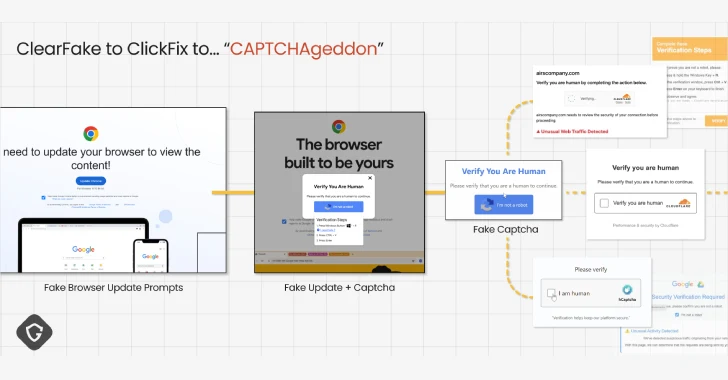
The cybersecurity landscape is constantly evolving, presenting new challenges for defenders across various platforms and industries. Recent developments highlight significant vulnerabilities and emerging threats that could impact global security infrastructures.
OpenSSL Vulnerabilities and Their Impact
The OpenSSL project has recently addressed a critical vulnerability, identified as CVE-2025-15467, which could allow remote code execution under specific conditions. This flaw, rooted in how the library processes Cryptographic Message Syntax data, poses a significant risk to systems relying on OpenSSL for secure communications. Attackers could exploit this vulnerability using maliciously crafted CMS packets, leading to potential system crashes and unauthorized code execution.
In addition to this, another high-severity flaw, CVE-2025-11187, has been identified. Both vulnerabilities underscore the importance of promptly updating and securing cryptographic libraries to mitigate exploitation risks.
Advancements in Ransomware Tactics
Ransomware-as-a-service (RaaS) operations continue to evolve, with the latest version of LockBit 5.0 incorporating advanced evasion techniques and targeting enterprise environments. The ransomware’s ability to support multiple systems, including Proxmox, an open-source virtualization platform, highlights the growing sophistication of threat actors seeking to expand their reach across diverse technological infrastructures.
Moreover, new campaigns using social engineering tactics, like the Matryoshka technique, are targeting macOS users. These campaigns employ nested obfuscation layers to deceive users into executing harmful commands, showcasing the need for heightened vigilance and security measures against such sophisticated threats.
AI and Security Challenges
The integration of artificial intelligence (AI) in technology has introduced new security challenges. Research indicates that passwords generated by large language models (LLMs) may appear robust but lack true randomness, making them insecure. This discovery emphasizes the necessity for secure password generation practices, as relying on AI-generated passwords could inadvertently weaken security postures.
Additionally, the misuse of AI tools for phishing campaigns, as seen with the Noodlophile malware, reflects the increasing exploitation of AI technologies by cybercriminals to enhance their attack strategies.
Overall, these developments highlight the dynamic nature of cybersecurity threats and the critical need for continuous monitoring and adapting defense strategies to safeguard against evolving risks.