Cybersecurity researchers are alerting to a brand new malware marketing campaign that employs the ClickFix social engineering tactic to trick customers into downloading an data stealer malware often called Atomic macOS Stealer (AMOS) on Apple macOS techniques.
The marketing campaign, based on CloudSEK, has been discovered to leverage typosquat domains mimicking U.S.-based telecom supplier Spectrum.
“macOS customers are served a malicious shell script designed to steal system passwords and obtain an AMOS variant for additional exploitation,” safety researcher Koushik Pal stated in a report revealed this week. “The script makes use of native macOS instructions to reap credentials, bypass safety mechanisms, and execute malicious binaries.”
It is believed that the exercise is the work of Russian-speaking cybercriminals owing to the presence of Russian language feedback within the malware’s supply code.
The start line of the assault is an online web page that impersonates Spectrum (“panel-spectrum[.]internet” or “spectrum-ticket[.]internet”). Guests to the websites in query are served a message that instructs them to finish a hCaptcha verification examine to with a view to “assessment the safety” of their connection earlier than continuing additional.
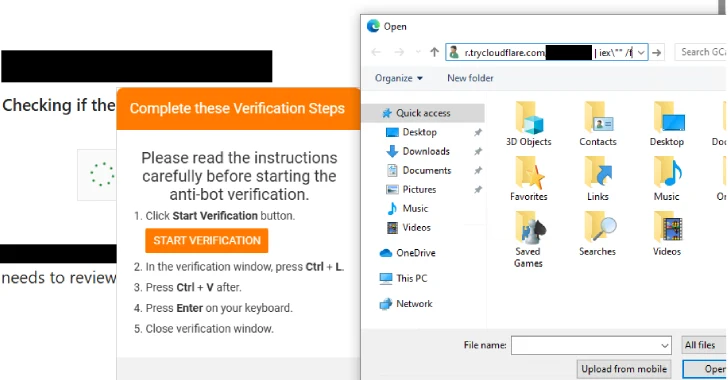
Nonetheless, when the person clicks the “I’m human” checkbox for analysis, they’re displayed an error message stating “CAPTCHA verification failed,” urging them to click on a button to go forward with an “Different Verification.”
Doing so causes a command to be copied to the customers’ clipboard and the sufferer is proven a set of directions relying on their working system. Whereas they’re guided to run a PowerShell command on Home windows by opening the Home windows Run dialog, it is substituted by a shell script that is executed by launching the Terminal app on macOS.
The shell script, for its half, prompts customers to enter their system password and downloads a next-stage payload, on this case, a identified stealer known as Atomic Stealer.
“Poorly applied logic within the supply websites, comparable to mismatched directions throughout platforms, factors to rapidly assembled infrastructure,” Pal stated.
“The supply pages in query for this AMOS variant marketing campaign contained inaccuracies in each its programming and front-end logic. For Linux person brokers, a PowerShell command was copied. Moreover, the instruction ‘Press & maintain the Home windows Key + R’ was exhibited to each Home windows and Mac customers.”
The disclosure comes amid a surge in campaigns utilizing the ClickFix tactic to ship a variety of malware households over the previous 12 months.
“Actors finishing up these focused assaults sometimes make the most of related strategies, instruments, and procedures (TTPs) to achieve preliminary entry,” Darktrace stated. “These embody spear phishing assaults, drive-by compromises, or exploiting belief in acquainted on-line platforms, comparable to GitHub, to ship malicious payloads.”
The hyperlinks distributed utilizing these vectors sometimes redirect the tip person to a malicious URL that shows a faux CAPTCHA verification examine and completes it in an try to deceive customers into pondering that they’re finishing up one thing innocuous, when, in actuality, they’re guided to execute malicious instructions to repair a non-existent problem.
The top results of this efficient social engineering methodology is that customers find yourself compromising their very own techniques, successfully bypassing safety controls.
In a single April 2025 incident analyzed by Darktrace, unknown risk actors had been discovered to make the most of ClickFix as an assault vector to obtain nondescript payloads to burrow deeper into the goal setting, conduct lateral motion, ship system-related data to an exterior server by way of an HTTP POST request, and in the end exfiltrate information.
“ClickFix baiting is a broadly used tactic by which risk actors exploit human error to bypass safety defenses,” Darktrace stated. “By tricking endpoint customers into performing seemingly innocent, on a regular basis actions, attackers acquire preliminary entry to techniques the place they’ll entry and exfiltrate delicate information.”
Different ClickFix assaults have employed phony variations of different standard CAPTCHA providers like Google reCAPTCHA and Cloudflare Turnstile for malware supply below the guise of routine safety checks.
These faux pages are “pixel-perfect copies” of their respectable counterparts, generally even injected into real-but-hacked web sites to trick unsuspecting customers. Stealers comparable to Lumma and StealC, in addition to full-fledged distant entry trojans (RATs) like NetSupport RAT are among the payloads distributed by way of bogus Turnstile pages.
“Fashionable web customers are inundated with spam checks, CAPTCHAs, and safety prompts on web sites, and so they’ve been conditioned to click on via these as rapidly as attainable,” SlashNext’s Daniel Kelley stated. “Attackers exploit this ‘verification fatigue,’ figuring out that many customers will adjust to no matter steps are offered if it seems to be routine.”
Discovered this text fascinating? This text is a contributed piece from considered one of our valued companions. Observe us on Twitter and LinkedIn to learn extra unique content material we put up.