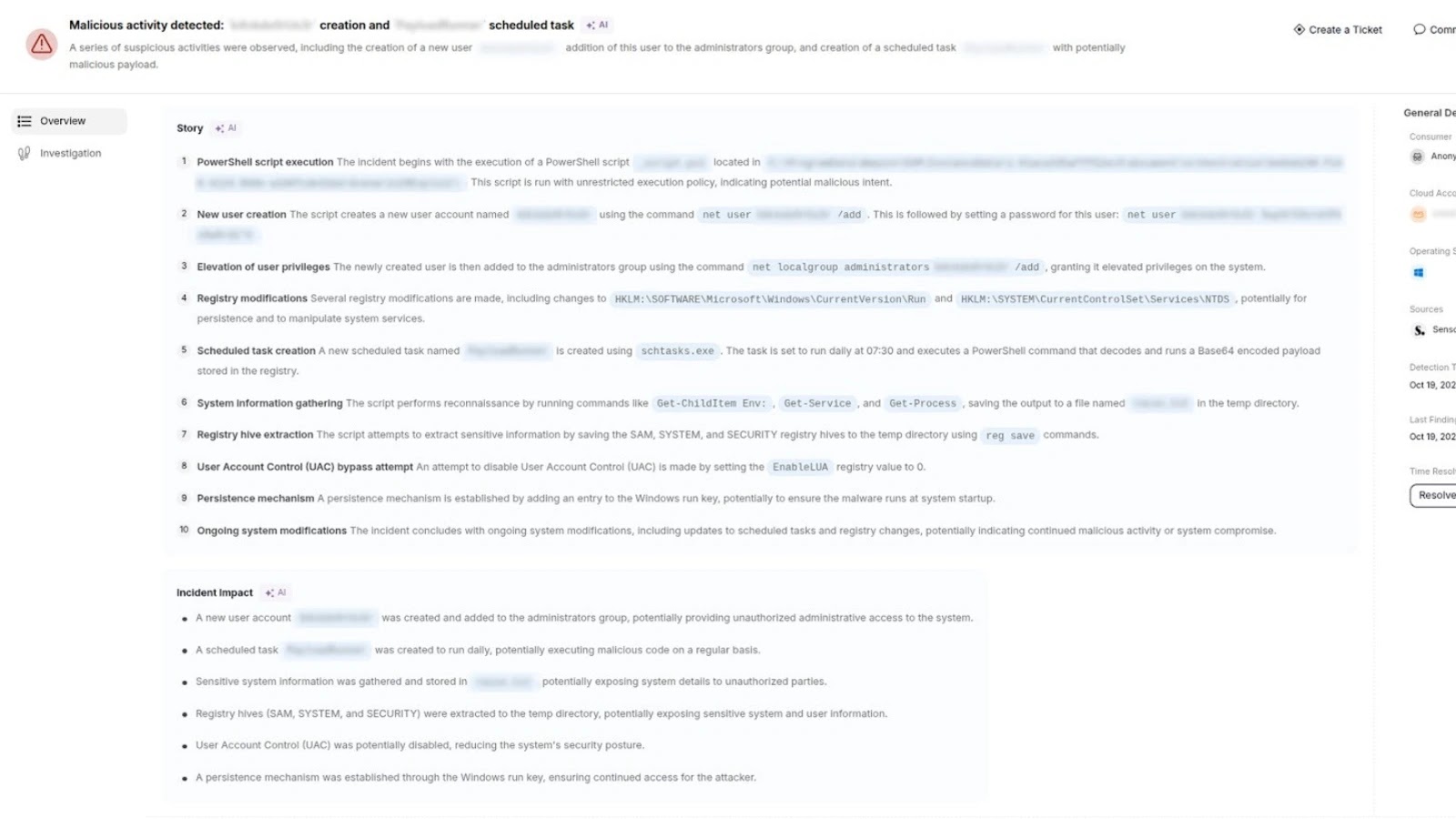
A brand new safety report reveals a troubling actuality in regards to the state of on-line phishing operations. Latest analysis has uncovered over 42,000 validated URLs and domains actively serving phishing kits, command-and-control infrastructure, and malicious payload supply techniques.
The size and class of those operations signify a big departure from conventional phishing makes an attempt.
Somewhat than easy misspelled domains and poorly written messages, fashionable phishing campaigns now function with the effectivity and group of official know-how corporations.
The menace panorama has essentially remodeled from ad-hoc particular person assaults into coordinated felony enterprises.
These operations leverage skilled infrastructure administration, sturdy uptime commitments, and engineered evasion strategies that rival enterprise-grade safety techniques.
SicuraNext safety analysts recognized that the infrastructure supporting these campaigns demonstrates outstanding operational maturity, with a 96.16% imply DNS decision price, indicating extremely secure and well-maintained malicious domains.
SicuraNext safety researchers famous that Cloudflare serves as the first infrastructure supplier for phishing operations worldwide.
The evaluation reveals that 17,202 of the 25,305 tracked malicious domains, representing 68% of all phishing infrastructure, function by Cloudflare’s community.
This focus exists as a result of Cloudflare’s free tier gives menace actors zero upfront price, world-class DDoS safety, and proxy providers that successfully masks the precise internet hosting servers.
The hundreds of malicious domains clustered on AS13335, Cloudflare’s main autonomous system quantity, have made the platform the de facto house base for phishing operations globally.
MFA Bypass Infrastructure and Protection Evasion
Essentially the most harmful growth includes Phishing-as-a-Service platforms, comparable to EvilProxy and Tycoon 2FA.
In contrast to conventional phishing kits that merely steal passwords, these providers function as adversary-in-the-middle proxies, positioning themselves between victims and bonafide providers.
When customers authenticate, the equipment intercepts their session whereas forwarding credentials to the true service, then captures the ensuing session cookie.
This strategy utterly bypasses multi-factor authentication protections. These subtle platforms incorporate a number of evasion applied sciences.
Geofencing blocks safety researchers by IP vary, whereas user-agent-based cloaking restricts content material visibility to particular machine sorts, usually displaying malicious pages solely on cell browsers.
Developer instruments detection instantly stops pages from functioning when safety researchers open inspection instruments. Cloudflare CAPTCHA filters mechanically filter out automated safety scanners.
The evaluation recognized 20 distinct phishing clusters sharing equivalent infrastructure fingerprints, rotated IP ranges, equivalent registrars, and matching evasion patterns, demonstrating coordinated, professionally-managed operations relatively than opportunistic assaults.
Comply with us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates, Set CSN as a Most well-liked Supply in Google.