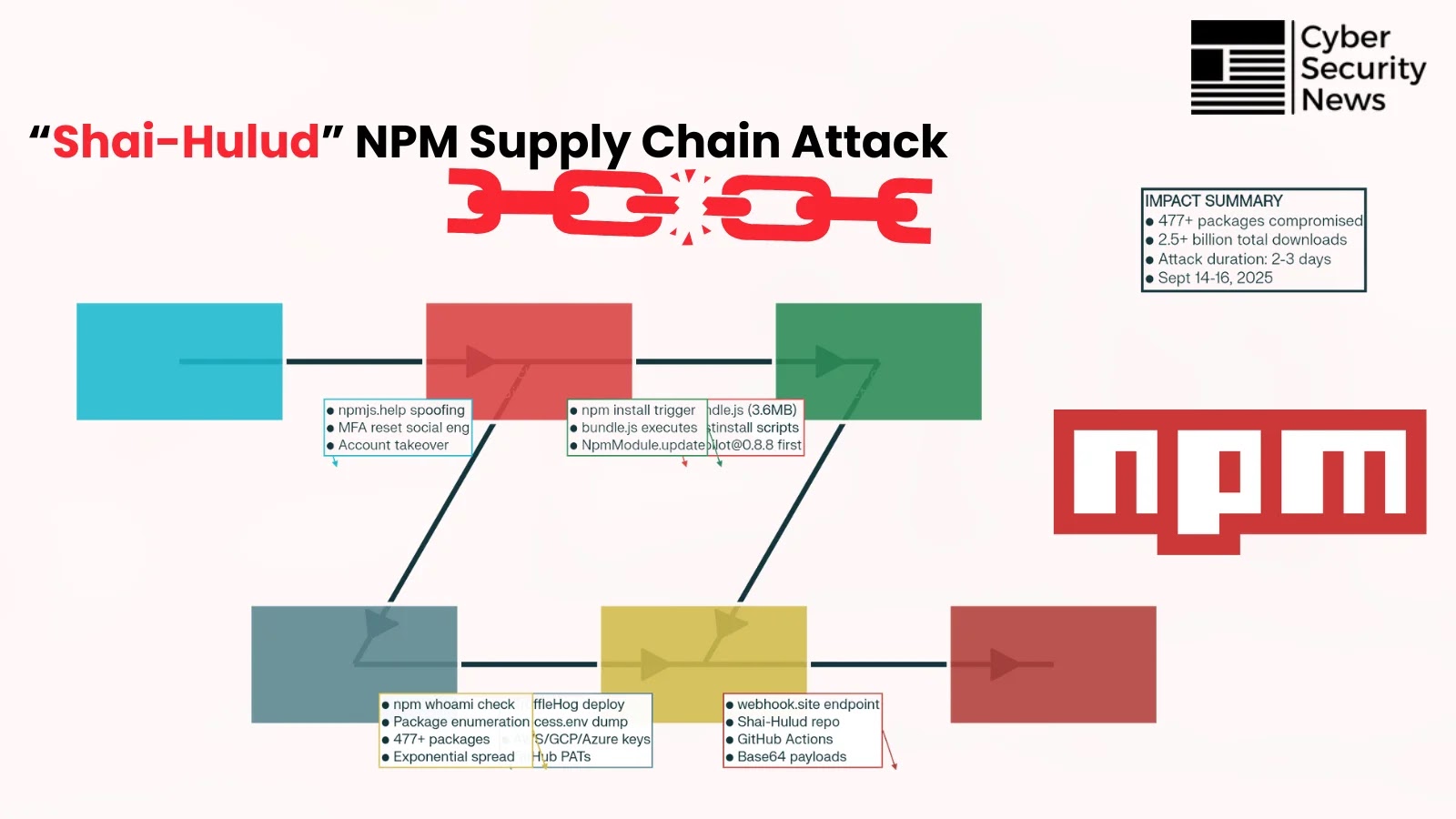
A recent cyberattack has compromised more than 1,800 Windows servers across the globe, deploying a malware known as BADIIS. This attack, targeting Internet Information Services (IIS) environments, has transformed legitimate server infrastructures into a vast network for SEO poisoning.
Impact on Search Engines
The compromised servers are manipulated by cybercriminals to alter search engine results, promoting illegal gambling and fraudulent cryptocurrency platforms. This tactic allows attackers to monetize compromised systems while evading conventional security measures, posing significant threats to various sectors globally.
The cyber operation impacts high-profile sectors, including government, educational, and financial institutions across multiple countries. BADIIS malware integrates deeply into the core processes of web servers, enabling real-time interception and modification of HTTP traffic. This allows attackers to redirect specific visitors to malicious sites without disrupting normal server operations.
Discovery and Analysis
Elastic Security Labs discovered the malware following a forensic investigation of a multinational organization, identifying peculiar post-compromise activities. Researchers linked this activity to a threat group known as UAT-8099, noting the campaign’s sophisticated operational security. The malware’s deployment across diverse industries, with a notable focus in the Asia-Pacific region, suggests a strategic exploitation of distinct internet usage patterns.
BADIIS’s sophistication is highlighted by its implementation as a malicious native IIS module, which facilitates persistence and evasion of detection. Unlike standalone malware processes, BADIIS loads into the IIS worker process, making it indistinguishable from legitimate server activities.
Advanced Evasion Techniques
The malware employs a “context-aware” filtering system to manage incoming traffic. It examines HTTP headers, focusing on User-Agent strings linked to search engine crawlers like Googlebot. When detected, BADIIS injects SEO keywords and links into the server’s response, enhancing the ranking of harmful sites. For system administrators or regular users, the malware serves clean, original content, ensuring the compromise remains undetected by human operators while actively poisoning search results.
Furthermore, the use of direct system calls enables the malware to bypass endpoint detection and response (EDR) mechanisms, maintaining its presence on the targeted systems.
Prevention and Future Outlook
Organizations are advised to routinely inspect installed IIS modules for any unauthorized or unsigned components to detect potential infections. Monitoring unexpected network connections initiated by the IIS worker process and ensuring all Windows Servers are updated against known vulnerabilities are crucial steps in preventing future compromises.
For continuous updates on cybersecurity developments, follow us on Google News, LinkedIn, and X. Set CSN as a preferred source in Google for more instant updates.