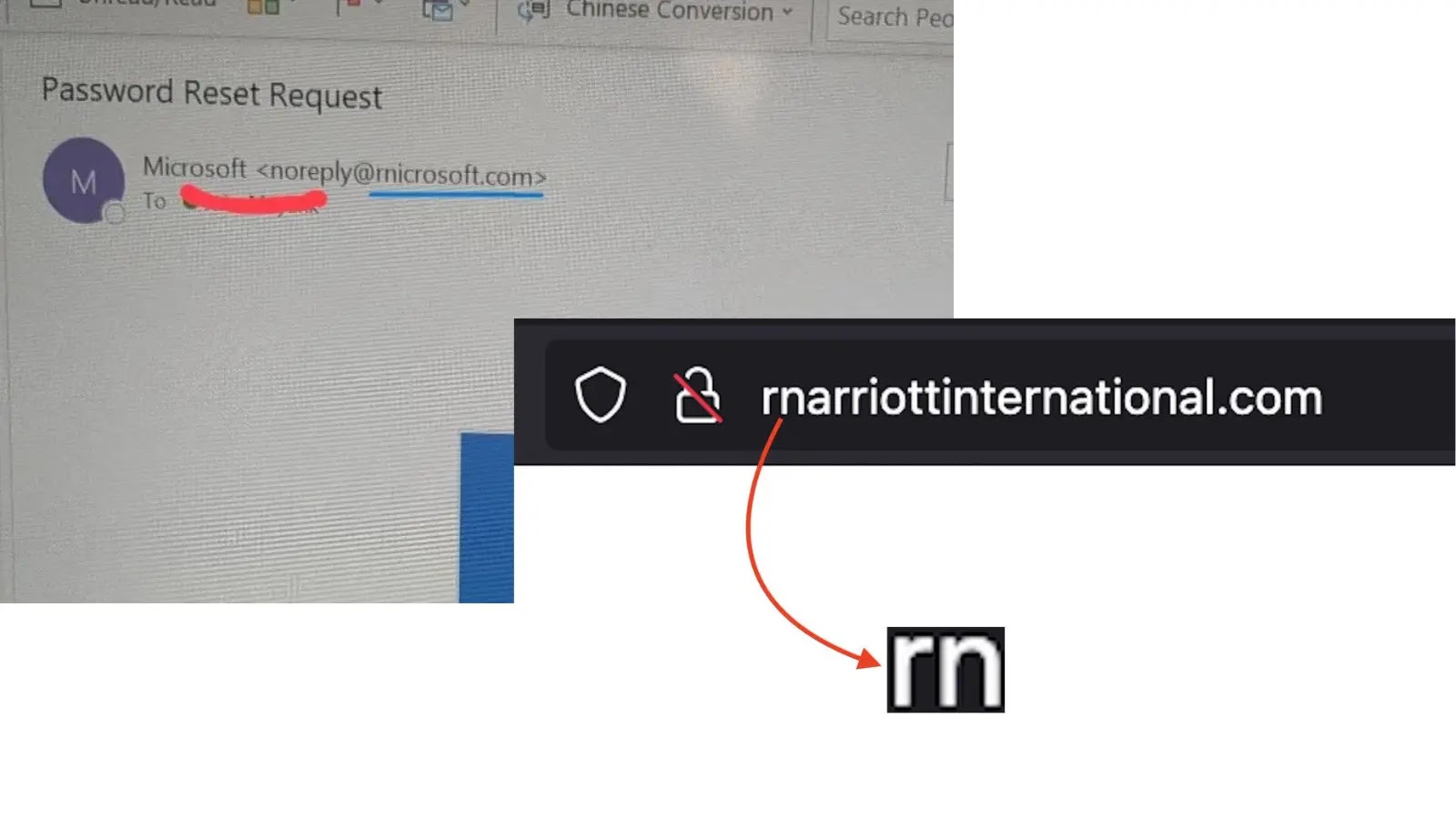
A complicated “homoglyph” phishing marketing campaign focusing on prospects of Marriott Worldwide and Microsoft. Attackers are registering domains that substitute the letter “m” with the mix “rn” (r + n), creating pretend web sites that look practically an identical to the true ones.
This method, often called typosquatting or a homoglyph assault, exploits the best way trendy fonts show textual content. In lots of fonts, the letters “r” and “n” are positioned subsequent to one another (rn) look visually indistinguishable from the letter “m” (m).
Hackers depend on this visible trick to bypass your mind’s skill to identify errors. While you look shortly at a URL like rnarriottinternational.com, your mind typically “autocorrects” what it sees, assuming it says “Marriott”.
Latest Campaigns Recognized
Marriott Worldwide Focused
Safety agency Netcraft lately recognized a cluster of malicious domains trying to impersonate the lodge big. These domains are doubtless used to steal loyalty account credentials or private visitor information.
The first area recognized is rnarriottinternational.com.
Attackers have additionally registered variations like rnarriotthotels.com to focus on particular lodge manufacturers.
Microsoft Customers Beneath Hearth
Harley Sugarman, CEO of the safety agency Anagram, highlighted an analogous marketing campaign focusing on Microsoft customers. Phishing emails on this marketing campaign use the area rnicrosoft.com to ship pretend safety alerts or bill notifications.
These emails mimic the official Microsoft brand, tone, and format.
The assault is especially harmful on cellular units, the place small screens make the “rn” vs. “m” distinction nearly inconceivable to see.
Indicators of Compromise (IOCs)
The next domains have been flagged as malicious. Safety groups ought to block these instantly, and customers ought to be cautious of any hyperlinks directing to them.
Phishing DomainImpersonated ServiceTyposquatting TechniqueDetection Difficultyrnarriottinternational.comMarriott Worldwide‘m’ changed with ‘rn’Vital rnarriotthotels.comMarriott Resorts‘m’ changed with ‘rn’Criticalrnicrosoft.comMicrosoft 365 / Login‘m’ changed with ‘rn’Excessive (Cell)micros0ft.comMicrosoft‘o’ changed with ‘0’Mediummicrosoft-support.comMicrosoft SupportHyphenation / SuffixLow
How you can Keep Secure
Broaden the Sender Deal with: On cellular e mail apps, faucet the sender’s title to disclose the total e mail handle. Look carefully for the “rn” trick.
Hover Earlier than You Click on: On a pc, hover your mouse cursor over hyperlinks with out clicking to see the precise vacation spot URL.
Handbook Entry: If you happen to obtain an pressing e mail a few lodge reserving or account reset, don’t click on the hyperlink. Open a browser and sort marriott.com or microsoft.com your self.
Use Password Managers: A password supervisor won’t auto-fill your credentials on a pretend web site like rnicrosoft.com as a result of it acknowledges that the area is completely different from the true one.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.