A novel and extremely difficult phishing marketing campaign is actively stealing Microsoft 365 credentials by exploiting Microsoft’s personal Energetic Listing Federation Companies (ADFS) to redirect customers from legit workplace.com hyperlinks to malicious login pages.
The approach, recognized by researchers on the cybersecurity agency Push Safety, marks a major evolution in phishing assaults, successfully bypassing each person vigilance and conventional safety filters.
The assault leverages a mixture of malvertising and a intelligent abuse of Microsoft’s infrastructure. As a substitute of counting on suspicious emails, the attackers place malicious adverts on engines like google.
A person trying to find “Workplace 365” would possibly click on a seemingly legit advert that directs them to a real outlook.workplace.com URL. Nevertheless, this URL is specifically crafted to set off an exploit.
On the coronary heart of the scheme is the abuse of ADFS, a Microsoft characteristic that facilitates single sign-on (SSO) by connecting a company’s native listing with cloud companies.
The menace actors arrange their very own Microsoft tenant and configured its ADFS settings to redirect authentication requests to a phishing area they management.
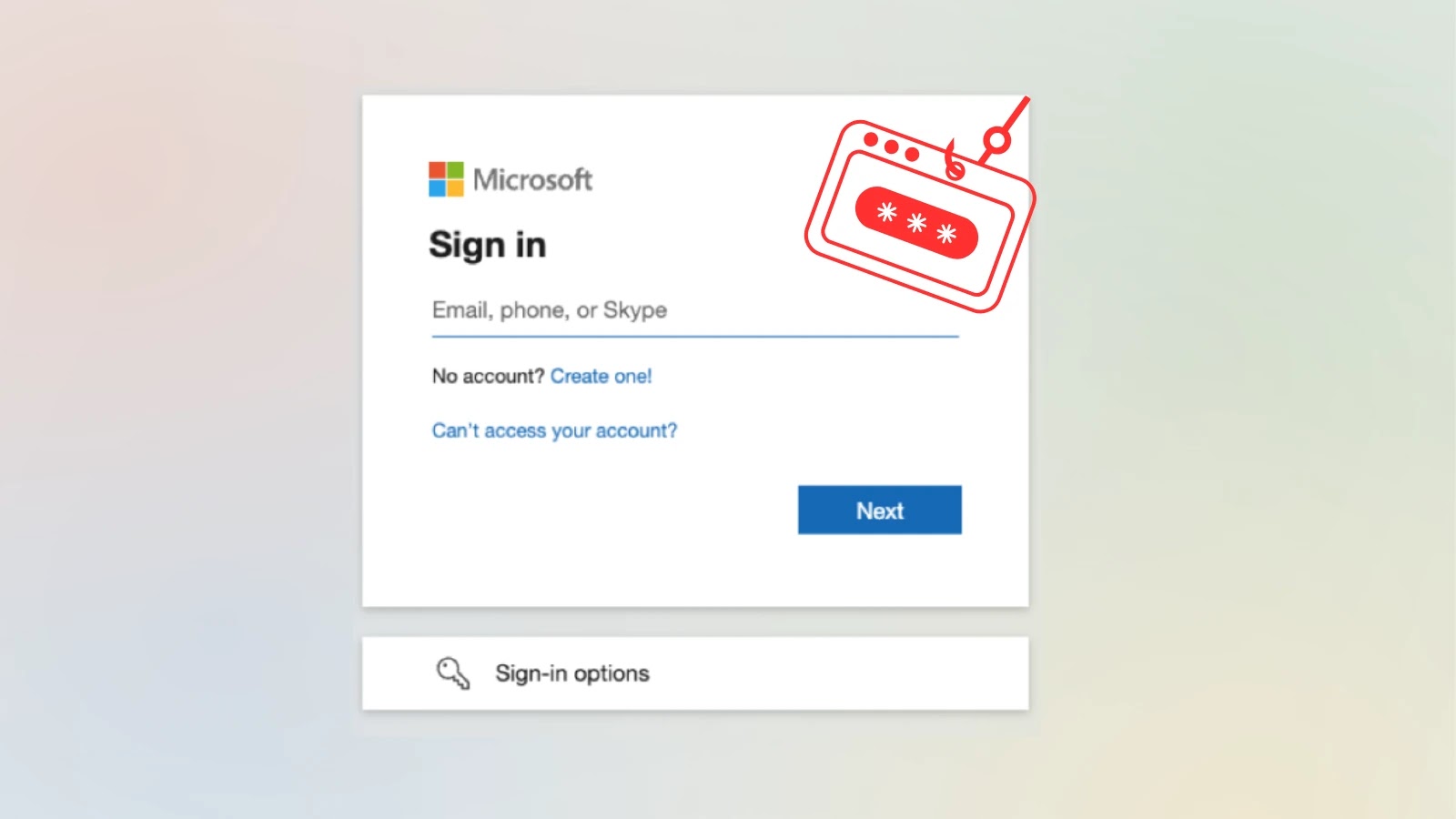
This manipulation forces Microsoft’s personal servers to ship the unsuspecting sufferer from the trusted workplace.com area to an ideal, pixel-for-pixel duplicate of the Microsoft login web page, Push Safety mentioned.
“That is principally the equal to Outlook.com having an open redirect vulnerability,” famous a researcher from Push of their evaluation.
Phishing Assault Chain
This “ADFSjacking,” because it has been dubbed, is potent as a result of the preliminary redirect originates from a trusted Microsoft supply, making it almost unattainable for URL-based safety instruments and cautious customers to detect the menace.
Request Passing
The investigation revealed a multi-stage redirect chain designed for evasion. After clicking the malicious advert, the person’s browser is invisibly handed via an middleman area, in a single case, a pretend journey weblog, earlier than touchdown on the ultimate phishing website.
This middleman step is designed to idiot automated area categorization instruments, which could classify the hyperlink as innocent, permitting it to go via internet filters.
As soon as on the pretend login web page, which features as an Attacker-in-the-Center (AitM) proxy, any credentials entered are instantly captured. This methodology additionally permits attackers to steal session cookies, enabling them to bypass multi-factor authentication (MFA) protections and acquire full entry to the sufferer’s account.
Malicious Login Web page
This marketing campaign highlights a troubling pattern the place attackers are shifting their supply strategies away from e-mail to channels like malvertising, social media, and prompt messaging, thereby sidestepping sturdy e-mail safety gateways.
To mitigate this menace, safety consultants advocate organizations monitor their community logs for uncommon ADFS redirects, notably these resulting in unfamiliar domains.
Filtering for Google Advert parameters in site visitors directed to workplace.com may assist determine this particular malvertising approach. For end-users, deploying a good advert blocker throughout all internet browsers stays a important protection towards the preliminary lure.
Safely detonate suspicious recordsdata to uncover threats, enrich your investigations, and minimize incident response time. Begin with an ANYRUN sandbox trial →