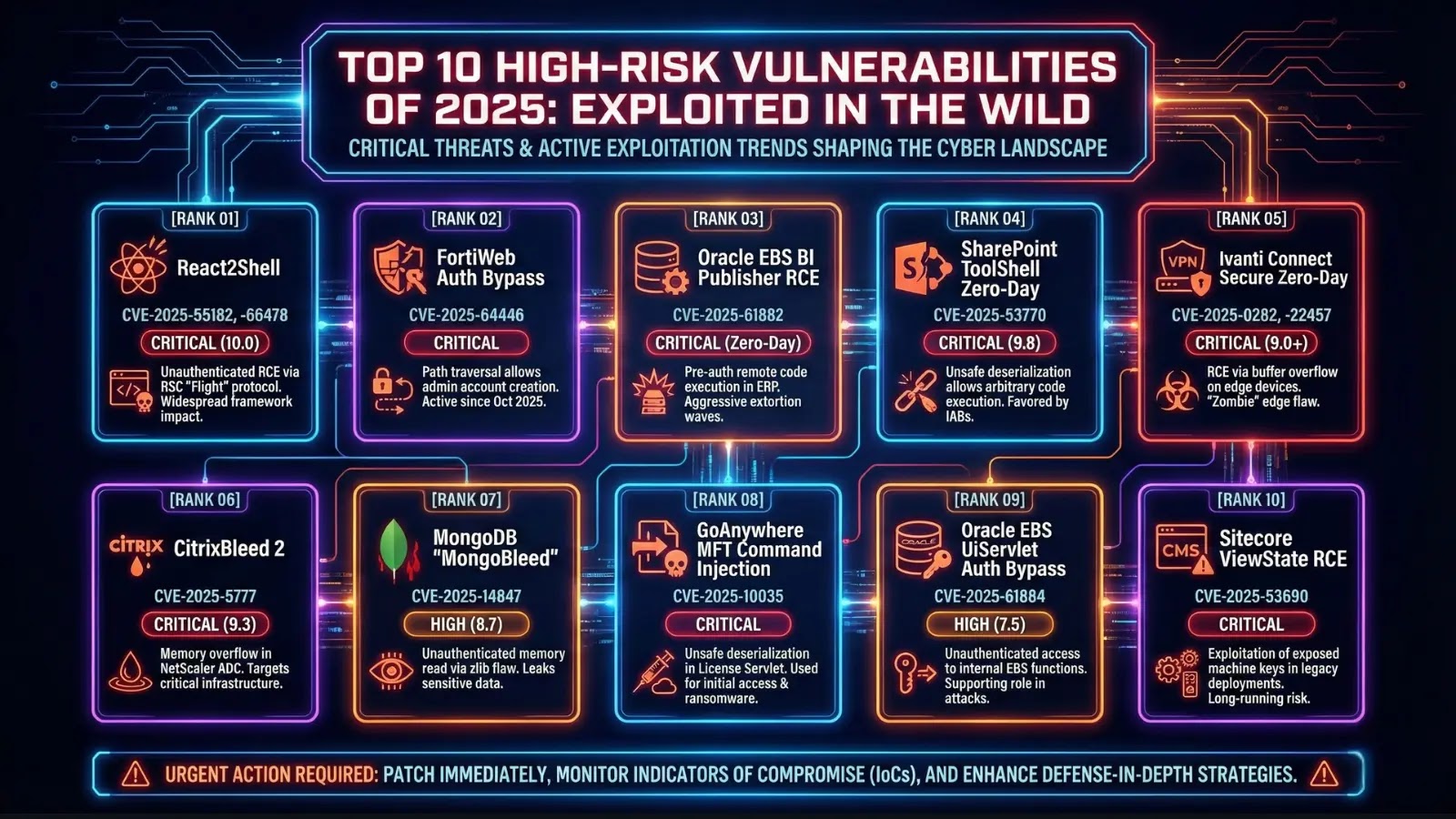
A major security flaw in Ivanti Endpoint Manager Mobile (EPMM), identified as CVE-2026-1281, is currently being exploited at a significant rate. Recent data from GreyNoise indicates that a staggering 83% of these attacks can be traced back to a single IP address: 193[.]24[.]123[.]42.
Primary Exploiting IP and Its Characteristics
The IP in question is associated with PROSPERO OOO (AS200593) and has been characterized as offering “bulletproof” hosting by Censys. It is noteworthy that this IP was absent from several of the initial indicators of compromise (IOCs) provided to cybersecurity defenders.
The exploitation of Ivanti EPMM is predominantly driven by this IP, which underscores the need for vigilance among organizations using the affected software.
Understanding the Vulnerabilities
The critical vulnerability, CVE-2026-1281, has a CVSS score of 9.8 and allows unauthorized attackers to execute commands by manipulating Bash arithmetic expansion within backend scripts. In addition to this, another vulnerability, CVE-2026-1340, presents a similar risk in a different component of the EPMM system.
On January 29, Ivanti issued a security advisory regarding these vulnerabilities. Shortly thereafter, the Cybersecurity and Infrastructure Security Agency (CISA) included CVE-2026-1281 in its catalog of Known Exploited Vulnerabilities, highlighting the urgency of addressing these issues.
Impact and Patterns of Attack
Between February 1 and 9, GreyNoise recorded 417 distinct exploitation attempts involving eight different IP addresses. Notably, February 8 saw 269 exploitation sessions, markedly higher than the preceding daily averages.
The primary IP, 193[.]24[.]123[.]42, has also been implicated in attacks on Oracle WebLogic Server, GNU Inetutils telnetd, and GLPI. The use of numerous user-agent strings suggests a strategy of automated mass exploitation.
Challenges in Detection and Mitigation
Many shared IOCs did not align with data on Ivanti exploitation. For example, although Windscribe VPN exit nodes generated significant traffic, they did not target Ivanti EPMM specifically. Similarly, a residential router was identified with limited activity.
Organizations focusing on blocking only these VPN or residential IPs may overlook the primary threat source, which is the AS200593 network.
Furthermore, approximately 85% of observed payloads employed DNS callbacks for code execution confirmation without immediately deploying malware. This behavior aligns with tactics used by initial access brokers, suggesting a sophisticated level of threat.
Additionally, “sleeper” webshells located at /mifs/403.jsp might persist undetected in systems even after patching, if attackers had prior access.
Stay informed on the latest cybersecurity developments by following us on Google News, LinkedIn, and X. For those interested in sharing their stories, please get in touch with us.