A new and complex social engineering campaign has emerged, targeting macOS developers through counterfeit Homebrew installation pages to distribute the Cuckoo Stealer malware. This malware is designed to harvest credentials extensively.
Exploiting Trust with ClickFix Technique
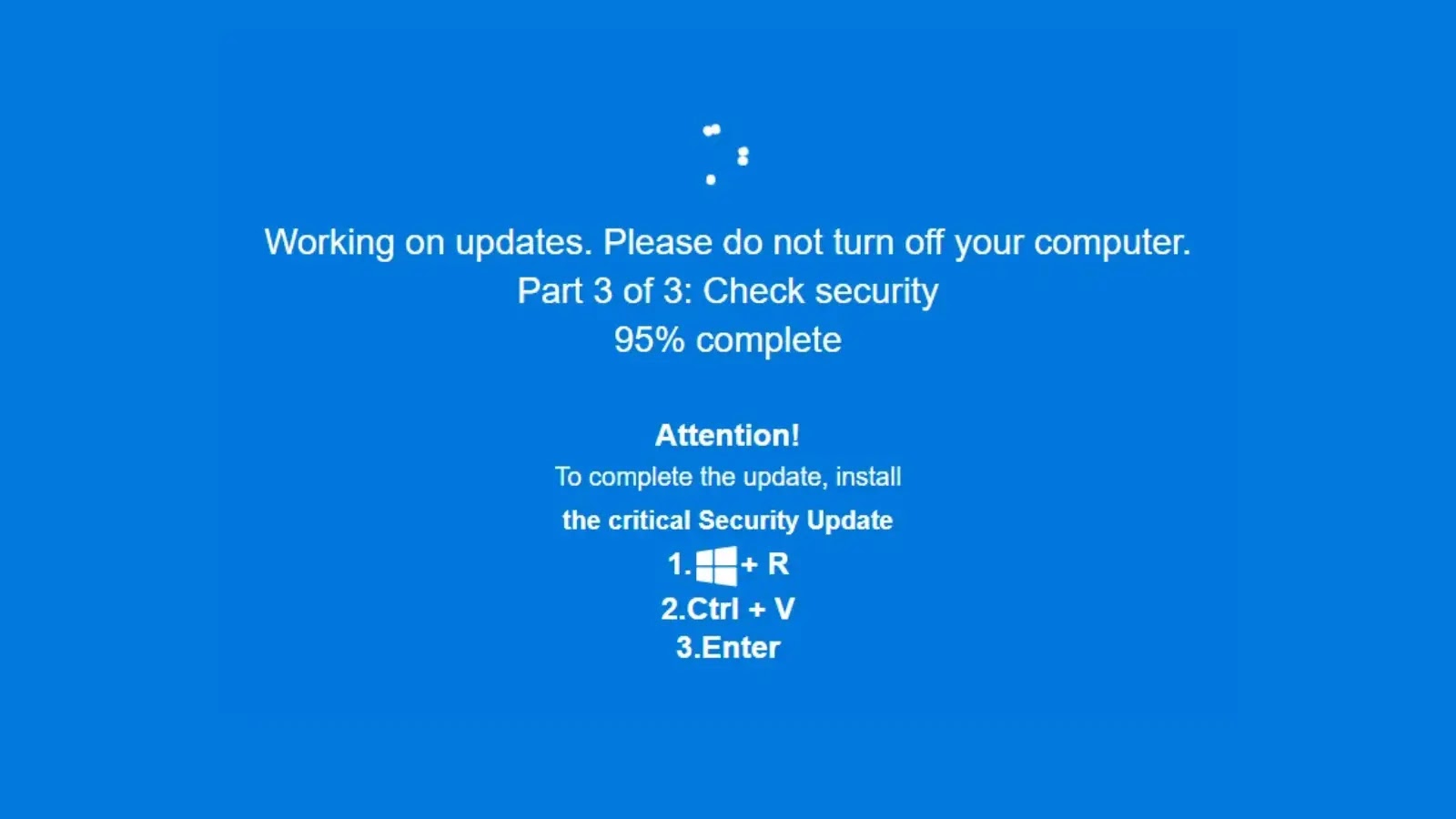
The attackers employ the ClickFix method, deceiving users into running harmful Terminal commands masquerading as legitimate software installation scripts. This method diverges from traditional attacks that exploit software vulnerabilities, instead taking advantage of user trust and standard developer workflows.
The attack is facilitated by typosquatted domains that closely resemble the genuine Homebrew site. Developers encountering these fake pages see what seems like a routine installation command with a copy button. The deceptive command subtly replaces raw.githubusercontent.com with raw.homabrews.org, a change barely noticeable at first glance.
Uncovering the Malicious Infrastructure
Hunt.io analysts unearthed this campaign by identifying the typosquatted domain homabrews.org, registered on January 13, 2026. Phishing URL detection flagged several URLs, including the critical raw.homabrews.org subdomain.
Further analysis revealed six interconnected domains on shared infrastructure at IP address 5.255.123.244, with the earliest certificates dating back to July 2025. These domains utilize various typosquatting strategies, such as character omission and alternate top-level domains, enhancing their deceptive capabilities.
Technical Details of the Attack Workflow
The attack unfolds in two primary stages. Initially, the script pretends to be a legitimate Homebrew installer while secretly checking user passwords using the dscl authonly command. This process mimics standard sudo behavior to avoid detection.
Once valid credentials are captured, a binary named brew_agent is downloaded, encoding the stolen password in Base64 and passing it as an argument for system access. Cuckoo Stealer achieves persistence through the macOS LaunchAgent system, disguising itself to blend with legitimate processes.
The malware employs several anti-analysis techniques, including locale-based filtering that blocks execution on systems configured for certain countries. All sensitive data is encrypted using complex obfuscation to evade detection.
Comprehensive Malware Capabilities
Cuckoo Stealer functions as a remote access trojan, capable of executing shell commands, rebooting systems, self-destructing, and controlling data exfiltration. It targets browser credentials, cryptocurrency wallets, macOS Keychain, Apple Notes, and messaging apps like Discord and Telegram.
This campaign highlights the importance of vigilance and security awareness among developers to protect against increasingly sophisticated cyber threats. Follow us on Google News, LinkedIn, and X for more updates and set CSN as a preferred source in Google.