Safety researchers have uncovered a complicated new phishing marketing campaign that exploits the Japanese hiragana character “ん” to create deceptively authentic-looking URLs that may idiot even vigilant web customers.
The assault, first recognized by safety researcher JAMESWT, targets explicitly prospects of the favored journey reserving platform Reserving.com.
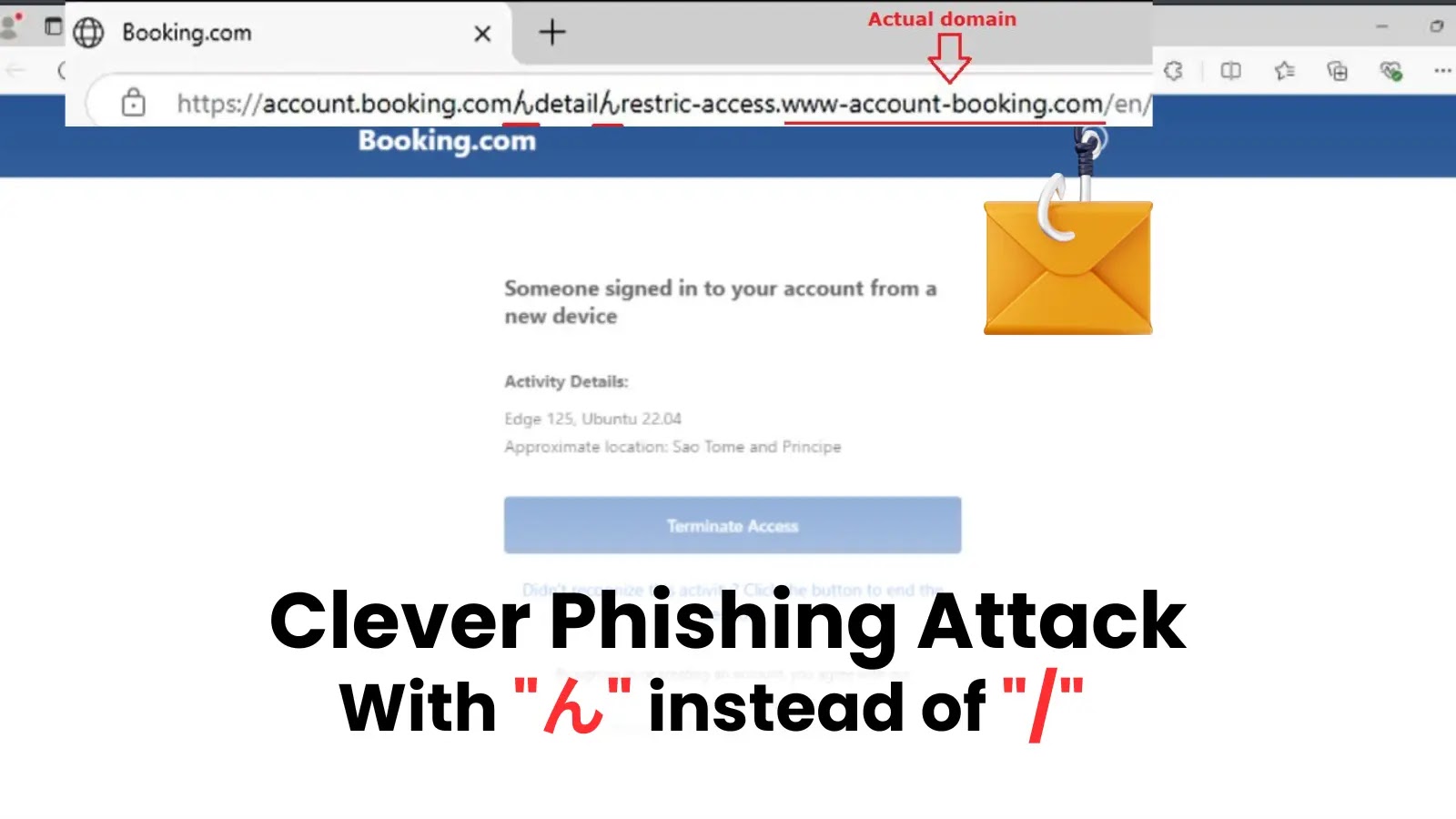
The malicious method leverages the visible similarity between the Japanese character “ん” (Unicode U+3093) and the ahead slash (“/”) character in sure fonts and programs.
When rendered in net browsers, URLs containing this character can seem nearly an identical to professional subdirectory paths, creating an virtually excellent phantasm of authenticity.
How the Phishing Assault Works
The phishing marketing campaign makes use of URLs that look like professional Reserving[.]com addresses, resembling what seems like “https://account.reserving[.]com/element/restric-access.www-account-booking[.]com/en/”.
Nevertheless, upon nearer examination, the ahead slashes are literally changed with the Japanese “ん” character, making the actual vacation spot a totally totally different area: www-account-booking[.]com.
“This visible deception is especially harmful as a result of it bypasses conventional safety consciousness coaching,” explains a cybersecurity professional in an evaluation from current risk intelligence reviews. “Customers who’ve been taught to fastidiously study URLs should fall sufferer as a result of the spoofed handle seems professional at first look.”
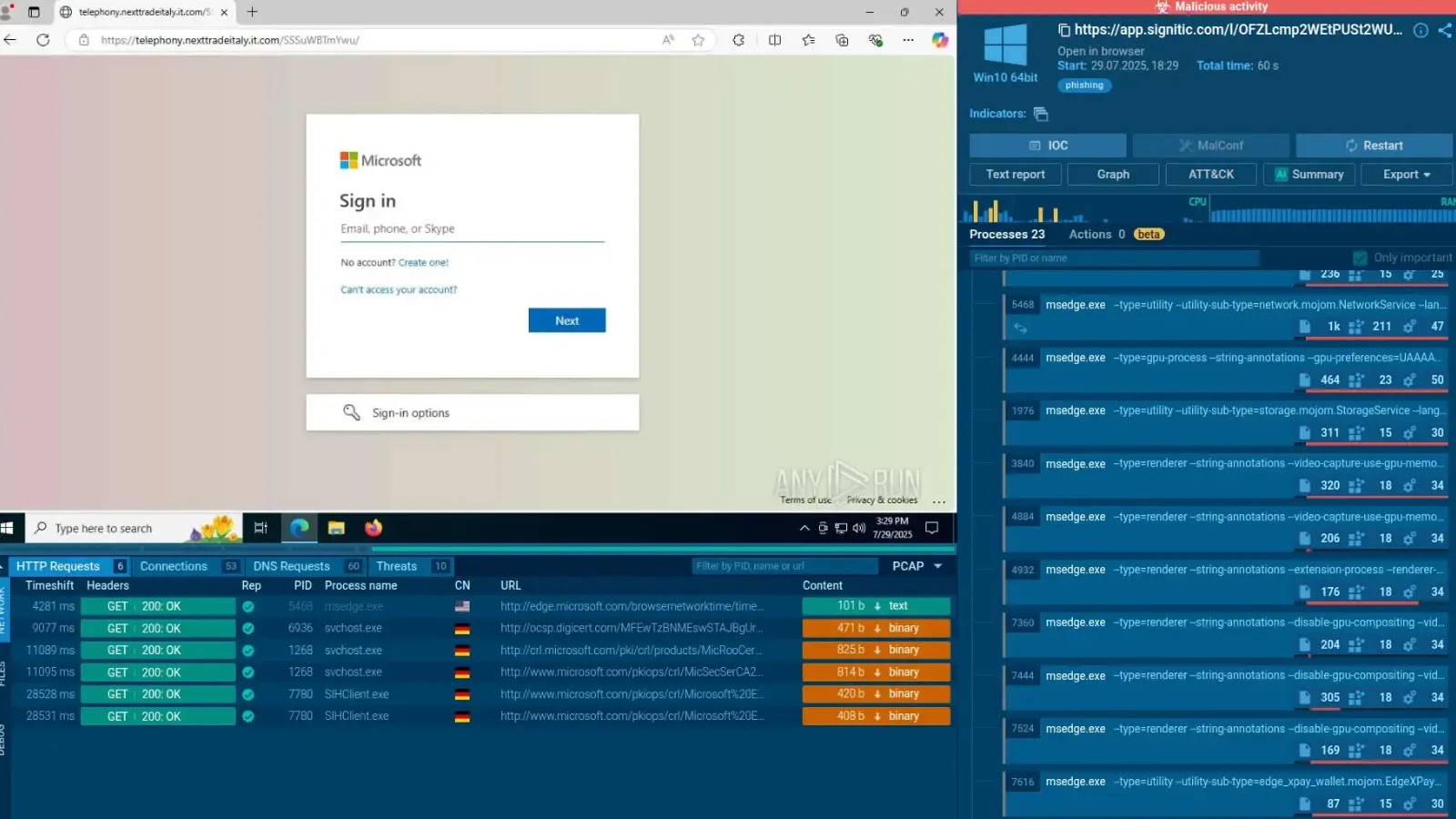
In keeping with Cybersecuritynews.com evaluation with ANY.RUN sandbox reveals that the assault begins with phishing emails that direct victims to those disguised URLs.
As soon as customers click on by, they’re ultimately redirected to malicious websites that ship MSI installer recordsdata containing malware, doubtlessly together with info stealers and distant entry trojans.
This Reserving[.]com-focused marketing campaign represents the most recent evolution in homograph assaults, the place cybercriminals exploit visually comparable characters from totally different Unicode character units to deceive customers. The method builds on years of comparable assaults utilizing Cyrillic characters to imitate Latin letters in domains.
In keeping with the 2025 Phishing Traits Report, homograph assaults have develop into more and more subtle as cybercriminals search new methods to bypass e mail filters and safety instruments.
Using the Japanese “ん” character is especially intelligent as a result of it maintains visible consistency whereas circumventing many present detection programs.
Safety consultants suggest a number of protecting measures in opposition to these Unicode-based assaults. Customers ought to hover over hyperlinks earlier than clicking to disclose the precise vacation spot URL, although this method has limitations when coping with subtle character spoofing.
Trendy browsers like Chrome have carried out protections in opposition to many homograph assaults, however safety researchers emphasize that visible URL inspection alone is now not foolproof.
The simplest protection combines up to date safety software program, e mail filtering, and consumer schooling about these evolving assault vectors.
As phishing campaigns proceed to evolve, this Japanese character exploitation demonstrates how cybercriminals consistently adapt their methods to use even the smallest visible ambiguities in digital communication programs.
Enhance your SOC and assist your group shield your corporation with free top-notch risk intelligence: Request TI Lookup Premium Trial.