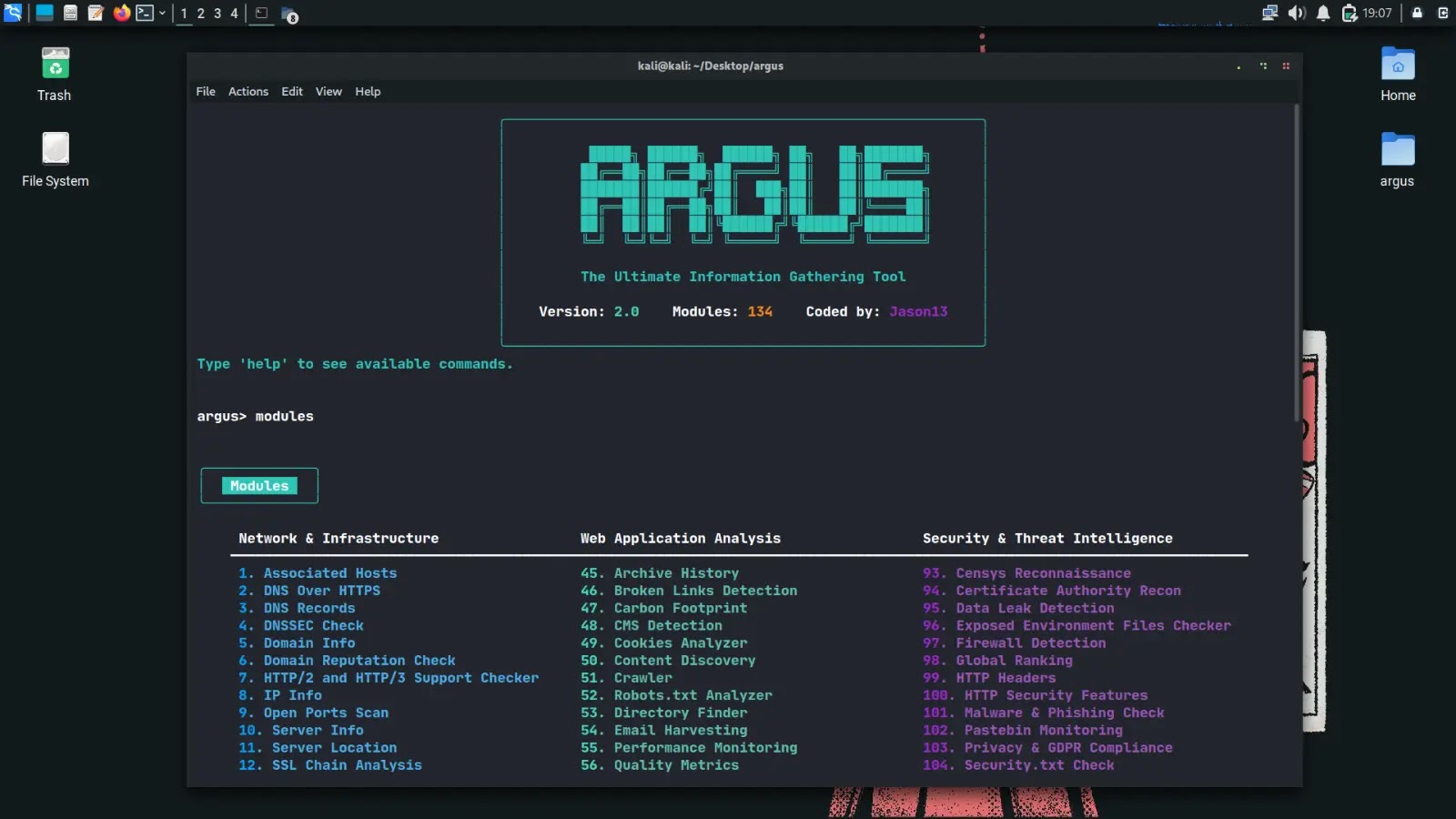
Argus is a complete Python-based toolkit designed for reconnaissance duties in cybersecurity. The builders not too long ago launched model 2.0, increasing it to incorporate 135 modules.
This device consolidates community evaluation, net app scanning, and menace intelligence into one interface. Customers entry modules via an interactive CLI that helps looking out, favorites, and batch runs. Community and infrastructure modules cowl DNS information, open ports, SSL chain evaluation, and traceroute from 1 to 52.
Internet software evaluation spans 53 to 102, together with CMS detection, content material discovery, JavaScript analyzers, and CORS scanners. Safety and menace intelligence modules, numbered 103 to 135, deal with Shodan queries, VirusTotal scans, subdomain takeovers, and cloud publicity checks.
CategoryModule CountKey ExamplesNetwork & Infrastructure52DNS Information, Open Ports Scan, WHOIS LookupWeb Utility Analysis50Directory Finder, Know-how Stack Detection, GraphQL ProbeSecurity & Risk Intelligence33Censys Recon, Subdomain Enumeration, JS Malware Scanner
Profiles like “pace” or “deep” alter thread counts and timeouts for various scan intensities.
Set up Strategies
Set up choices go well with varied environments. Direct run requires git clone, pip set up necessities, and python -m argus. Pip customers kind pip set up argus-recon, then argus.
Full setup makes use of an set up.sh script after cloning. Docker builds a picture with quantity mounts for outcomes. All strategies help Linux, macOS, and Home windows by way of Python 3.10+.
OptionCommandsBest ForNo Installgit clone cd argus; pip set up -r necessities.txt; python -m argusQuick testsPippip set up argus-recon; argusMinimal setupFullgit clone …; chmod +x set up.sh; ./set up.sh; python -m argusDevelopmentDockergit clone …; docker construct -t argus-recon:newest .; docker run …Containers
The CLI screenshot reveals the module menu clearly.
Launch with argus, listing modules with “modules”, choose by way of “use 1”, set goal like “set goal instance.com”, then “run”. Instructions embody “runall infra” for classes and “present api_status” for integrations.
Configure API keys for Shodan, VirusTotal, and Censys in settings.py or env vars. Export outputs as TXT, CSV, or JSON. Model 2.0 breaks from legacy 1.x by including 25+ instructions, multi-threading, and UI enhancements.
Safety consultants reward its breadth for crimson teaming and OSINT, decreasing device sprawl. At all times receive permission; the device features a authorized disclaimer in opposition to misuse. Argus simplifies recon workflows for pentesters and analysts.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.