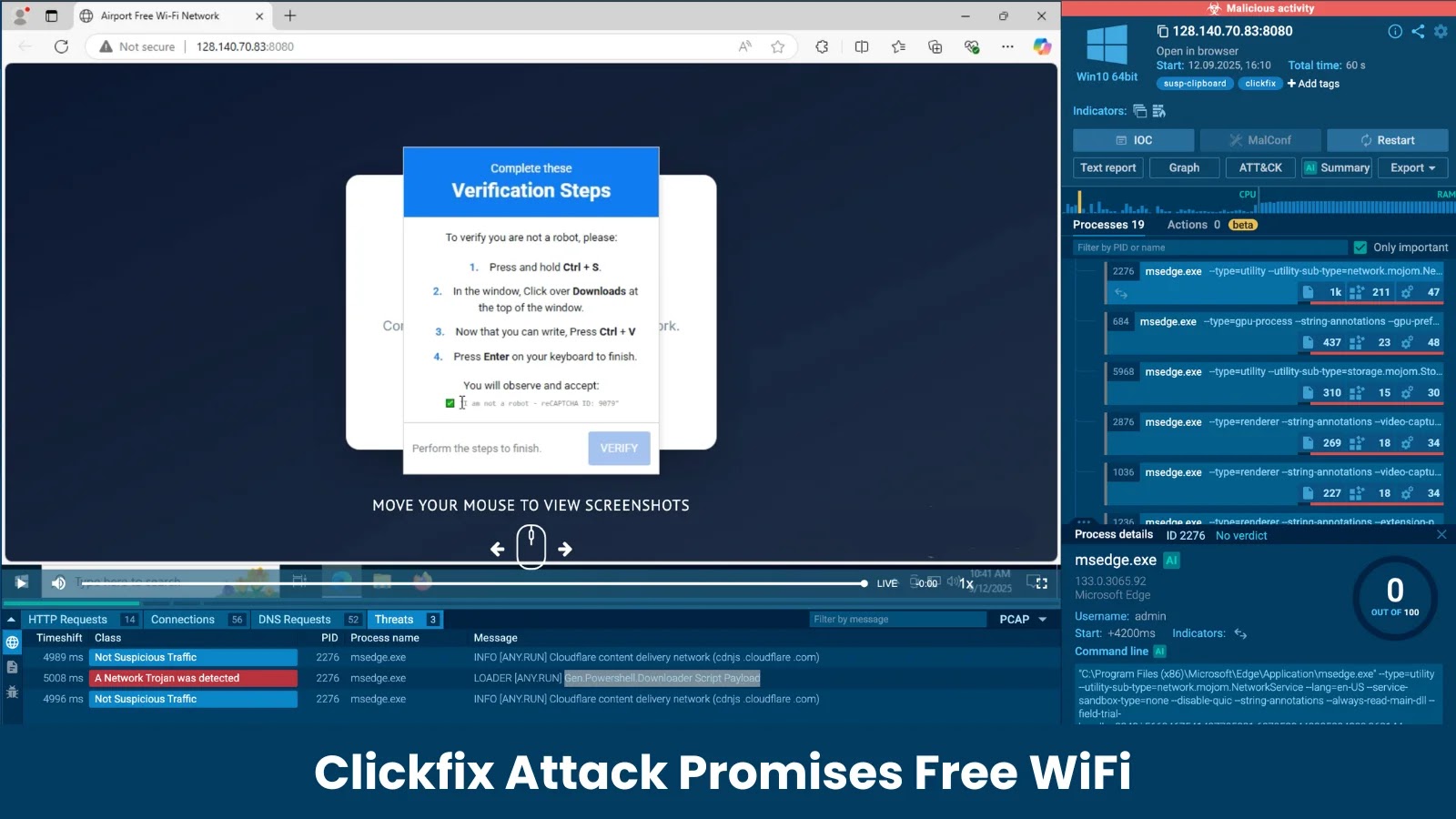
ZeroDayRAT, a newly surfaced mobile spyware, is making waves by offering a comprehensive surveillance tool for targeting both Android and iOS platforms. Discovered on February 2, 2026, it is distributed openly via Telegram, posing a significant threat to mobile device security.
What is ZeroDayRAT?
This malicious platform provides a browser-based interface that allows operators to manage compromised devices. It enables full-scale monitoring, including GPS tracking, capturing notifications, and accessing SMS messages, even those containing OTP codes. Additionally, it allows live feeds from cameras and microphones, and includes features like screen recording and keylogging, which are linked to specific app contexts.
How ZeroDayRAT Operates
Once installed, the spyware can list accounts associated with the device and perform actions like cryptocurrency address swapping and using banking overlays to steal credentials. The tool has been identified by iVerify researchers as part of a growing trend in “ready to run” mobile spyware, which requires minimal technical expertise from the user.
The spyware is often delivered through smishing attacks, where victims receive deceptive text messages that lead them to download malicious apps. These tactics are also employed via phishing emails, fake app stores, or through links shared in messaging apps like WhatsApp or Telegram.
Security Implications and Defense Strategies
Upon installation, ZeroDayRAT provides operators with a detailed user profile, including device specifics and intercepted communications. This access can lead to severe consequences, such as SMS-based two-factor authentication codes being exploited, paving the way for account takeovers and financial losses.
To combat these threats, users should only download apps from official stores, avoid sideloading, and scrutinize links in messages before clicking. Utilizing stronger multi-factor authentication methods than SMS, rotating passwords after suspected breaches, and investigating unusual device behavior can further mitigate risks. Organizations are encouraged to implement mobile threat monitoring and establish a clear protocol for addressing potential spyware incidents swiftly.
Stay informed with technological updates by following us on Google News, LinkedIn, and X. Choose CSN as your primary news source on Google for more insights.