Oct 29, 2025Ravie LakshmananMalware / Menace Intelligence
Cybersecurity researchers have found a set of 10 malicious npm packages which might be designed to ship an data stealer focusing on Home windows, Linux, and macOS programs.
“The malware makes use of 4 layers of obfuscation to cover its payload, shows a pretend CAPTCHA to look respectable, fingerprints victims by IP deal with, and downloads a 24MB PyInstaller-packaged data stealer that harvests credentials from system keyrings, browsers, and authentication providers throughout Home windows, Linux, and macOS,” Socket safety researcher Kush Pandya stated.
The npm packages have been uploaded to the registry on July 4, 2025, and gathered over 9,900 downloads collectively –
deezcord.js
dezcord.js
dizcordjs
etherdjs
ethesjs
ethetsjs
nodemonjs
react-router-dom.js
typescriptjs
zustand.js
The multi-stage credential theft operation manifested within the type of numerous typosquatted packages impersonating common npm libraries equivalent to TypeScript, discord.js, ethers.js, nodemon, react-router-dom, and zustand.
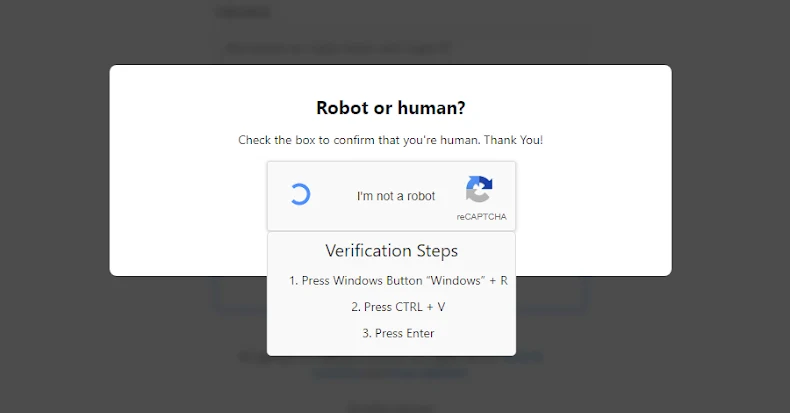
As soon as put in, the malware serves a pretend CAPTCHA immediate and shows authentic-looking output that mimics respectable bundle installations to offer the impression that the setup course of is continuing alongside anticipated strains. Nonetheless, within the background, the bundle captures the sufferer’s IP deal with, sends it to an exterior server (“195.133.79[.]43”), after which proceeds to drop the principle malware.
In every bundle, the malicious performance is robotically triggered upon set up by the use of a postinstall hook, launching a script named “set up.js” that detects the sufferer’s working system and launches an obfuscated payload (“app.js”) in a brand new Command Immediate (Home windows), GNOME Terminal or x-terminal-emulator (Linux), or Terminal (macOS) window.
“By spawning a brand new terminal window, the malware runs independently of the npm set up course of,” Pandya famous. “Builders who look at their terminal throughout set up see a brand new window briefly seem, which the malware instantly clears to keep away from suspicion.”
The JavaScript contained inside “app.js” is hidden via 4 layers of obfuscation — equivalent to XOR cipher with a dynamically generated key, URL-encoding of the payload string, and utilizing hexadecimal and octal arithmetic to obscure program circulation — which might be designed to withstand evaluation.
The top purpose of the assault is to fetch and execute a complete data stealer (“data_extracter”) from the identical server that is outfitted to completely scan the developer’s machine for secrets and techniques, authentication tokens, credentials, and session cookies from net browsers, configuration recordsdata, and SSH keys.
The stealer binary additionally incorporates platform-specific implementations to extract credentials from the system keyring utilizing the keyring npm library. The harvested data is compressed right into a ZIP archive and exfiltrated to the server.
“System keyrings retailer credentials for essential providers together with e mail purchasers (Outlook, Thunderbird), cloud storage sync instruments (Dropbox, Google Drive, OneDrive), VPN connections (Cisco AnyConnect, OpenVPN), password managers, SSH passphrases, database connection strings, and different purposes that combine with the OS credential retailer,” Socket stated.
“By focusing on the keyring instantly, the malware bypasses application-level safety and harvests saved credentials of their decrypted type. These credentials present rapid entry to company e mail, file storage, inside networks, and manufacturing databases.”