Cybersecurity experts have uncovered a sophisticated ClickFix campaign leveraging compromised legitimate websites to distribute a newly identified remote access trojan, MIMICRAT, also known as AstarionRAT. This campaign, which was detailed in a recent report by Elastic Security Labs, highlights the strategic use of varied industries and geographies as a delivery network for this malicious software.
Operational Sophistication Uncovered
The ClickFix campaign showcases a high degree of operational complexity. It utilizes a multi-stage PowerShell sequence to bypass Event Tracing for Windows (ETW) and Antimalware Scan Interface (AMSI) protections before deploying a Lua-scripted shellcode loader. The final payload communicates via HTTPS on port 443, emulating legitimate web analytics traffic.
MIMICRAT, developed in C++, includes capabilities for Windows token impersonation, SOCKS5 tunneling, and executing 22 distinct commands for post-exploitation activities. This campaign was identified earlier this month and shares tactical similarities with another ClickFix operation that utilizes the Matanbuchus 3.0 loader as a precursor for the same RAT, aiming at potential ransomware attacks or data theft.
Infection Pathway and Techniques
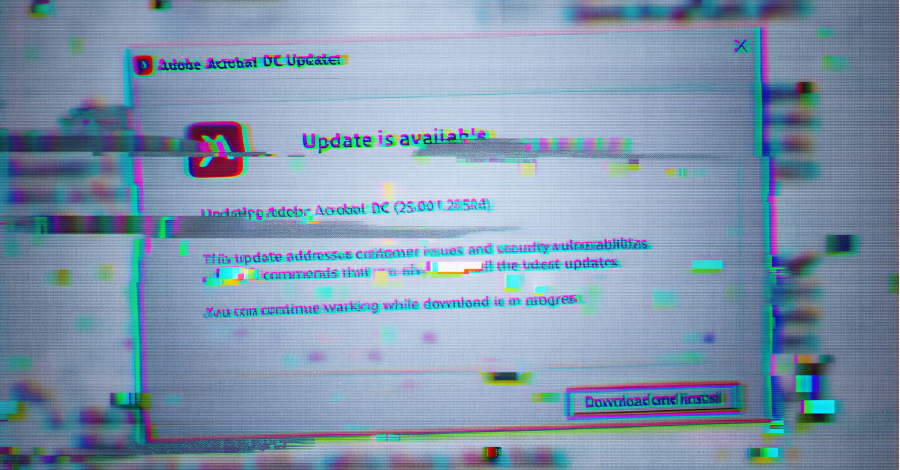
The infection process, as described by Elastic, begins with bincheck[.]io, a legitimate service for Bank Identification Number validation that was compromised to inject harmful JavaScript. This script loads an externally hosted PHP file, presenting a fake Cloudflare verification page. Victims are misled into executing a command in the Windows Run dialog, initiating a PowerShell command that connects to a command-and-control server.
This server then delivers a second-stage PowerShell script, which patches Windows event logging and antivirus scanning functions before deploying a Lua-based loader. The loader decrypts and executes in-memory shellcode, ultimately installing MIMICRAT. The trojan communicates with its control server over HTTPS, supporting a range of commands for system manipulation and network operations.
Global Reach and Targeting
The campaign’s lure content is dynamically localized in 17 different languages based on the victim’s browser settings, significantly expanding its reach. Documented victims include a university in the USA and numerous Chinese-speaking users, indicating the campaign’s broad and opportunistic targeting strategy.
Security researcher Salim Bitam noted the widespread nature of the campaign, emphasizing its potential impact across various sectors and regions. As cybersecurity teams work to understand and mitigate this threat, the importance of robust security measures and vigilance against such sophisticated campaigns is underscored.
In conclusion, the ClickFix campaign represents a significant threat with its advanced techniques and global targeting. Continued research and collaboration among cybersecurity professionals are essential to countering these evolving threats.