Jan 16, 2026Ravie LakshmananMalware / Cyber Espionage
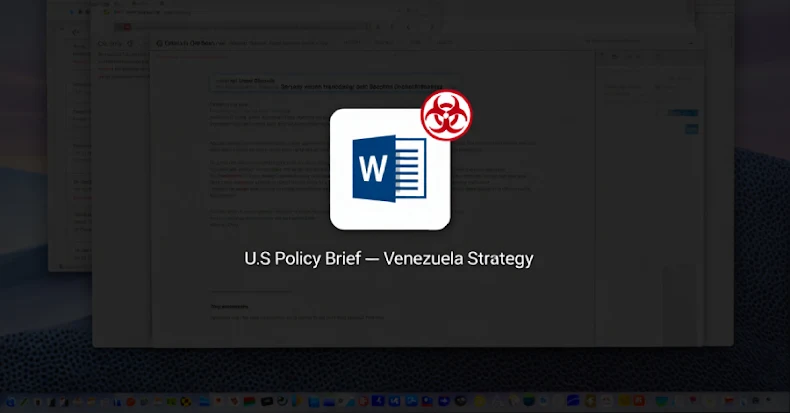
Safety specialists have disclosed particulars of a brand new marketing campaign that has focused U.S. authorities and coverage entities utilizing politically themed lures to ship a backdoor often called LOTUSLITE.
The focused malware marketing campaign leverages decoys associated to the latest geopolitical developments between the U.S. and Venezuela to distribute a ZIP archive (“US now deciding what’s subsequent for Venezuela.zip”) containing a malicious DLL that is launched utilizing DLL side-loading methods. It is not identified if the marketing campaign managed to efficiently compromise any of the targets.
The exercise has been attributed with reasonable confidence to a Chinese language state-sponsored group often called Mustang Panda (aka Earth Pret, HoneyMyte, and Twill Hurricane), citing tactical and infrastructure patterns. It is value noting that the menace actor is thought for extensively counting on DLL side-loading to launch its backdoors, together with TONESHELL.
“This marketing campaign displays a continued development of focused spear phishing utilizing geopolitical lures, favoring dependable execution methods reminiscent of DLL side-loading over exploit-based preliminary entry,” Acronis researchers Ilia Dafchev and Subhajeet Singha mentioned in an evaluation.
The backdoor (“kugou.dll”) employed within the assault, LOTUSLITE, is a bespoke C++ implant that is designed to speak with a hard-coded command-and-control (C2) server utilizing Home windows WinHTTP APIs to allow beaconing exercise, distant tasking utilizing “cmd.exe,” and knowledge exfiltration. The entire listing of supported instructions is as follows –
0x0A, to provoke a distant CMD shell
0x0B, to terminate the distant shell
0x01, to ship instructions by way of the distant shell
0x06, to reset beacon state
0x03, to enumerate information in a folder
0x0D, to create an empty file
0x0E, to append knowledge to a file
0x0F, to get beacon standing
LOTUSLITE can also be able to establishing persistence by making Home windows Registry modifications to make sure that it is routinely executed every time the person logs in to the system.
Acronis mentioned the backdoor “mimics the behavioral shenanigans of Claimloader by embedding provocative messages.” Claimloader is the identify assigned to a DLL that is launched utilizing DLL side-loading and is used to deploy PUBLOAD, one other Mustang Panda instrument. The malware was first documented by IBM X-Drive in June 2025 in reference to a cyber espionage marketing campaign aimed on the Tibetan group.
“This marketing campaign demonstrates how easy and well-tested methods can nonetheless be efficient when paired with focused supply and related geopolitical lures,” the Singaporean cybersecurity firm concluded. “Though the LOTUSLITE backdoor lacks superior evasion options, its use of DLL sideloading, dependable execution move, and primary command-and-control performance displays a concentrate on operational dependability somewhat than sophistication.”
The disclosure comes as The New York Instances revealed particulars a few purported cyber assault undertaken by the U.S. to disrupt electrical energy for many residents within the capital metropolis of Caracas for a couple of minutes, earlier than the January 3, 2026, navy operation that captured Venezuelan President Nicolás Maduro. The mission
“Turning off the ability in Caracas and interfering with radar allowed US navy helicopters to maneuver into the nation undetected on their mission to seize Nicolás Maduro, the Venezuelan president who has now been dropped at america to face drug expenses,” the Instances reported.
“The assault triggered most of Caracas’s residents to lose their energy for a couple of minutes, although some neighborhoods close to the navy base the place Mr. Maduro was captured had been left with out electrical energy for as much as 36 hours.”