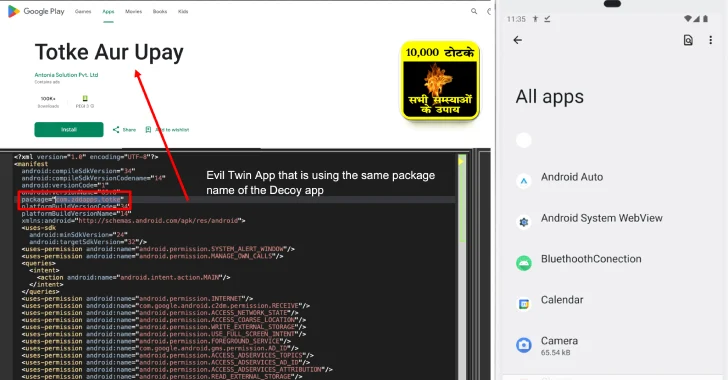
Cybersecurity researchers have found a brand new, subtle variant of a recognized Android malware known as Konfety that leverages the evil twin approach to allow advert fraud.
The sneaky strategy primarily includes a situation whereby two variants of an utility share the identical package deal identify: A benign “decoy” app that is hosted on the Google Play Retailer and its evil twin, which is distributed through third-party sources.
It is value stating that the decoy apps do not must be essentially revealed by menace actors themselves and might be reputable. The one caveat is that the malicious apps share the very same package deal names as their actual counterparts already accessible on the Play Retailer.
“The menace actors behind Konfety are extremely adaptable, constantly altering their focused advert networks and updating their strategies to evade detection,” Zimperium zLabs researcher Fernando Ortega stated. “This newest variant demonstrates their sophistication by particularly tampering with the APK’s ZIP construction.”
Through the use of malformed APKs, the tactic permits menace actors to sidestep detection and problem reverse engineering efforts. Apart from dynamically loading the primary DEX (Dalvik Executable) payload at runtime, the newly found variations allow the general-purpose bit flag by setting it to “Bit 0,” signaling to the system that the file is encrypted.
This conduct, in flip, triggers a false password immediate when trying to examine the Android package deal, thereby blocking entry and complicating makes an attempt to research its contents.
The second approach entails falsely declaring the usage of BZIP compression methodology within the app’s manifest XML file (“AndroidManifest.xml”), inflicting evaluation instruments like APKTool and JADX to crash because of a parsing failure. An identical compression-based protection evasion approach was beforehand highlighted by Kaspersky in one other Android malware known as SoumniBot.
Using dynamic code loading to execute the first payload affords added stealth throughout preliminary scans or reverse engineering, Zimperium famous. Throughout execution, the DEX payload is decrypted and loaded straight into reminiscence with out attracting any crimson flags.
“This multi-layered obfuscation strategy, combining encrypted property, runtime code injection, and misleading manifest declarations, demonstrates the evolving sophistication of the Konfety operation and its steady efforts to evade evaluation and bypass detection mechanisms,” Ortega stated.
Just like the earlier iteration reported by HUMAN final yr, Konfety abuses the CaramelAds software program growth package (SDK) to fetch advertisements, ship payloads, and preserve communication with attacker-controlled servers.
It comes with capabilities to redirect customers to malicious web sites, immediate undesirable app installs, and set off persistent spam-like browser notifications. Moreover, the malware hides its app icon and makes use of geofencing to change its performance primarily based on the sufferer’s area.
The event comes as ANY.RUN detailed a Chinese language Android packer instrument often known as Ducex that is primarily designed to hide embedded payloads like Triada inside pretend Telegram apps.
“The packer employs critical obfuscation via operate encryption utilizing a modified RC4 algorithm with added shuffling,” ANY.RUN researcher Alina Markova stated. “Ducex creates main roadblocks for debugging. It performs APK signature verification, failing if the app is re-signed. It additionally employs self-debugging utilizing fork and ptrace to dam exterior tracing.”
On high of that, Ducex is designed to detect the presence of fashionable evaluation instruments reminiscent of Frida, Xposed, and Substrate, and if current, terminate itself.
The findings additionally comply with a brand new research revealed by a workforce of researchers from TU Wien and the College of Bayreuth a couple of novel approach dubbed TapTrap that may be weaponized by a malicious app to covertly bypass Android’s permission system and acquire entry to delicate knowledge or execute damaging actions.
The assault, in a nutshell, hijacks person interactions on Android gadgets by overlaying animations or video games on a person’s display screen, whereas surreptitiously launching person interface parts beneath that trick customers into performing undesirable actions, reminiscent of putting in malware or granting the app intrusive permissions.
“Usually, Android reveals an animation when the display screen adjustments, reminiscent of the brand new display screen sliding or fading in,” researchers Philipp Beer, Marco Squarcina, Sebastian Roth, and Martina Lindorfer stated. “Nevertheless, the app can inform the system {that a} customized animation needs to be used as an alternative that’s long-running and makes the brand new display screen totally clear, protecting it hidden from you.”
“Any faucets you make throughout this animation go to the hidden display screen, not the seen app. The app can then use this to lure you into tapping on particular areas of the display screen that correspond to delicate actions on the hidden display screen, permitting it to carry out actions with out your data.”
In a hypothetical assault situation, a menace actor-released recreation put in by the sufferer can secretly open an online browser session and dupe them into granting digital camera permissions to a malicious web site.
That stated, TapTrap’s influence extends past the Android ecosystem, opening the door to tapjacking and internet clickjacking assaults. The problem has been addressed in GrapheneOS, Chrome 135 (CVE-2025-3067), and Firefox 136 (CVE-2025-1939). Android 16 continues to stay prone to the assault.
Discovered this text fascinating? Comply with us on Twitter and LinkedIn to learn extra unique content material we publish.