Key Points
- Notepad++ hosting was compromised by the China-linked Lotus Blossom group.
- A backdoor named Chrysalis was delivered to users.
- The hosting breach was fixed with an update in December 2025.
- Rapid7 linked the attack to previous campaigns by the same group.
Introduction to the Notepad++ Hosting Breach
The open-source text editor Notepad++ recently found its hosting infrastructure compromised by a hacking group linked to China, known as Lotus Blossom. This breach was identified after the attackers managed to deliver a backdoor called Chrysalis to the software’s users. The cybersecurity firm Rapid7 has provided new insights into this incident, highlighting the vulnerabilities exploited by the threat actors.
The breach occurred at the hosting provider level, allowing the attackers to redirect update requests to malicious servers. This operation took advantage of inadequate update verification controls present in older versions of Notepad++. The issue was addressed in December 2025 when a new version was released to patch the vulnerability.
Details of the Attack and Its Implications
According to Rapid7’s findings, the attackers gained access to Notepad++’s hosting infrastructure, redirecting traffic to deliver a compromised update. This update included a backdoor that enabled the attackers to gather system information and potentially execute further commands on affected systems. However, the security measures implemented after the breach have since mitigated these threats.
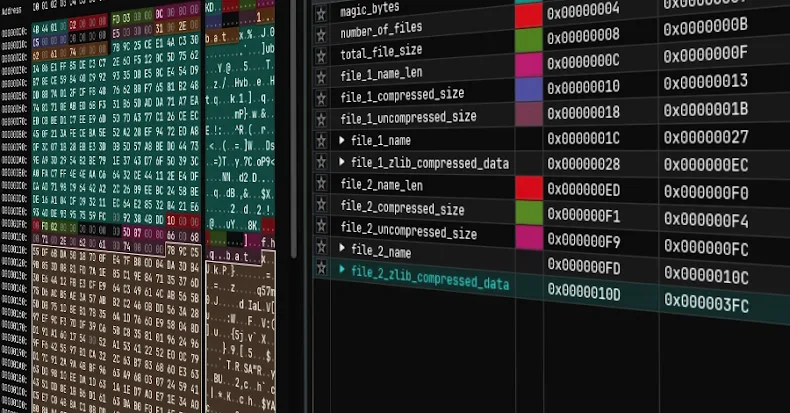
The attack mechanism involved several components, including a suspicious process named ‘update.exe’ downloaded from a specific IP address. This file is an installer containing multiple files, such as an installation script and a malicious DLL designed for side-loading.
- An NSIS installation script
- BluetoothService.exe for DLL side-loading
- BluetoothService, encrypted shellcode
- log.dll, a malicious DLL
Chrysalis Backdoor: Features and Analysis
The Chrysalis backdoor, a custom implant used in this attack, is capable of various operations. It connects to an external server and processes HTTP responses to execute commands, manage files, and potentially uninstall itself. Although the command-and-control server is currently offline, the backdoor’s design suggests it was actively developed over time.
Rapid7’s analysis also identified a component within Chrysalis intended to retrieve a Cobalt Strike beacon using a custom loader. This loader employs Microsoft’s Warbird framework for code protection, adding another layer of sophistication to the attack.
Conclusion and Future Outlook
The breach of Notepad++’s hosting infrastructure underscores the persistent threat posed by state-sponsored hacking groups like Lotus Blossom. Despite the vulnerabilities being patched, the incident highlights the need for continuous vigilance and robust security measures to protect open-source projects. Moving forward, maintaining updated software and employing rigorous security protocols will be critical in defending against such sophisticated attacks.
Frequently Asked Questions
- What is Chrysalis?
Chrysalis is a backdoor used by the Lotus Blossom group to gather system information and execute commands on infected systems. - How was the Notepad++ breach discovered?
The breach was identified through analysis by Rapid7, which linked the attack to previous campaigns by Lotus Blossom. - What measures were taken to secure Notepad++?
The vulnerability was patched with a new software version in December 2025, and the hosting provider was changed to enhance security. - Who is the Lotus Blossom group?
Lotus Blossom is a hacking group linked to China, known for using sophisticated techniques in cyberattacks. - Is the Chrysalis backdoor still active?
The command-and-control server for Chrysalis is currently offline, reducing its immediate threat.