Google has introduced the general public preview of its Alert Triage and Investigation agent, a big development in synthetic intelligence-driven safety operations.
The clever agent is now embedded straight inside Google Safety Operations, serving to safety groups course of alerts sooner and extra successfully.
The brand new agent represents a big step towards Google’s imaginative and prescient of an “Agentic SOC,” a safety operations heart powered by clever automation.
As a substitute of getting safety analysts verify each alert by hand, the agent checks them itself, collects info, and decides whether or not they’re actual threats or innocent.
This functionality permits safety groups to focus their consideration on alerts that genuinely require human experience.
Throughout personal preview testing, the agent investigated lots of of hundreds of alerts throughout numerous organizations and industries.
Suggestions from monetary providers corporations and main retailers revealed substantial time financial savings. Google analysts reported that the agent’s complete investigation summaries enabled sooner decision-making.
Whereas consolidating advanced info that will in any other case require handbook queries and evaluation.
The investigation course of begins when alerts are generated in Google’s detection engine. The agent critiques every alert and creates a dynamic investigation plan on line with Mandiant specialists’ finest practices.
How the Agent Works
It then executes a number of analytical capabilities, together with YARA-L searches, to retrieve related occasions.
Menace intelligence enrichment utilizing Google Menace Intelligence, command-line evaluation for encoded or obfuscated instructions, and course of tree reconstruction to know the total scope of potential assaults.
After finishing its investigation, the agent decides whether or not the alert is actual and assigns a confidence rating indicating how certain it’s.
Google emphasizes explainability all through the agent’s course of. The system references its sources and descriptions investigation steps so analysts perceive how suggestions had been reached.
The corporate makes use of a number of analysis strategies, together with comparisons with human specialists and AI analysis strategies, to make sure accuracy and steady enchancment.
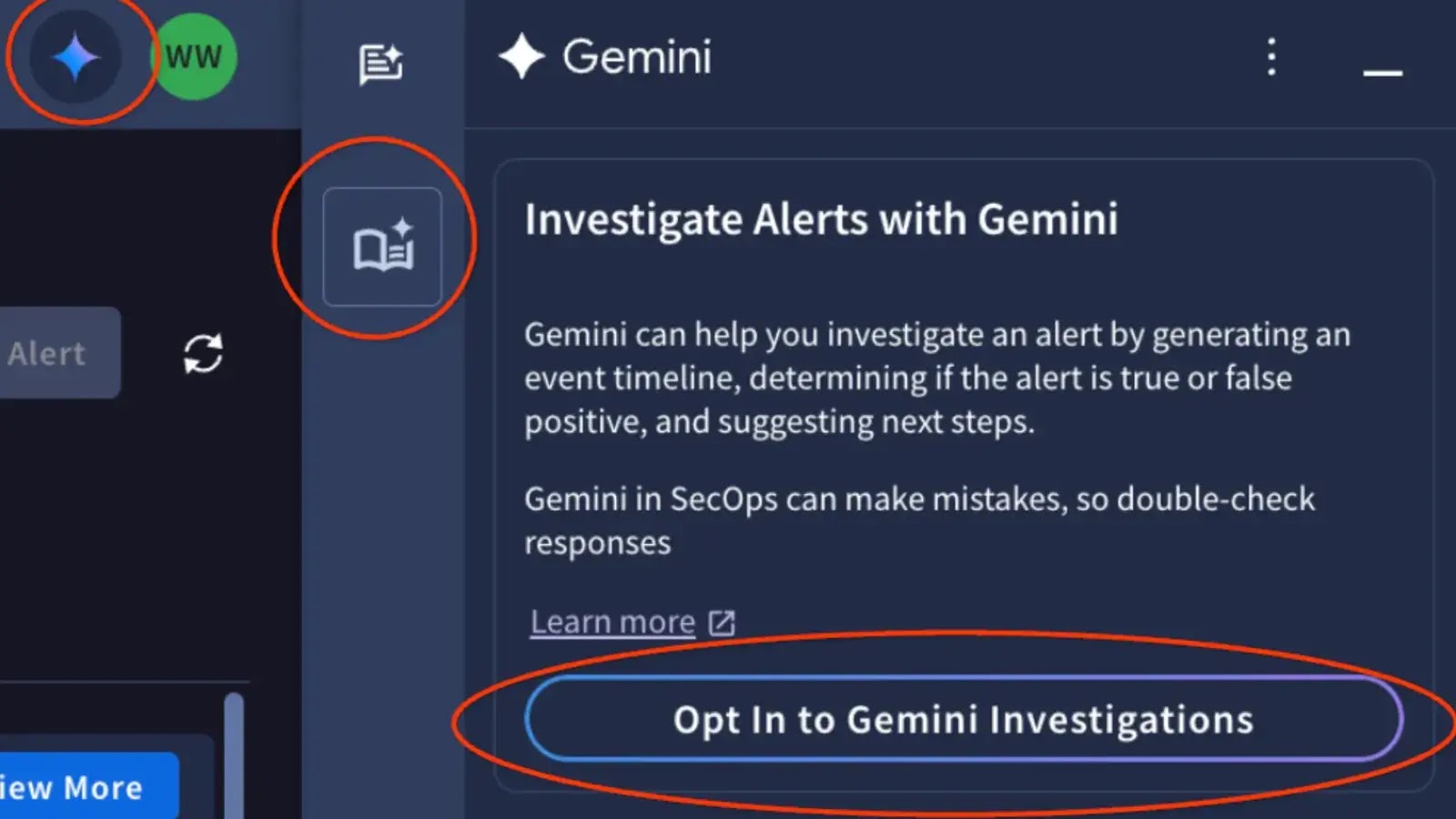
All eligible Google Safety Operations Enterprise and Enterprise Plus customers can choose into the general public preview instantly by clicking the Gemini icon inside Google Safety Operations.
Investigations start mechanically after enrollment, although customers may also set off investigations manually. Google plans to carry the agent to basic availability in 2026 with further enhancements to investigation depth and workflow integration.
Comply with us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.