Cloudflare, an organization that gives internet safety and infrastructure, lately reported that it stopped an enormous cyber assault.
This assault reached a file excessive of 11.5 terabits per second (Tbps). It was a kind of assault known as a Distributed Denial-of-Service (DDoS) assault, particularly a UDP flood. A lot of the assault got here from compromised assets on the Google Cloud Platform.
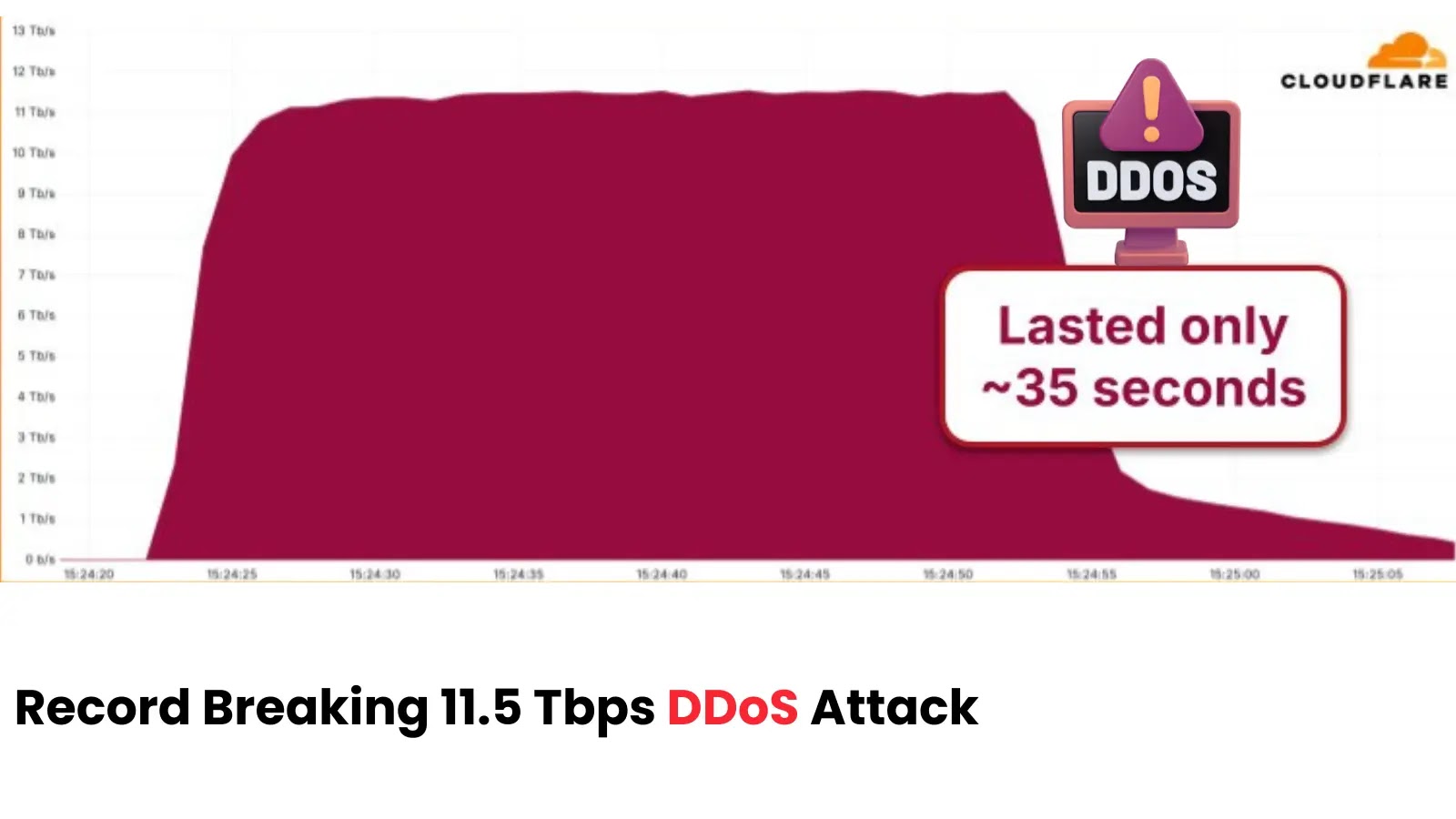
The corporate’s automated protection programs detected and neutralized the hyper-volumetric assault, which, regardless of its immense measurement, lasted for less than about 35 seconds.
A picture shared by Cloudflare detailed the assault’s temporary however highly effective lifecycle, exhibiting a fast spike to 11.5 Tbps earlier than being introduced beneath management.
Cloudflare confirmed its programs “autonomously detected and mitigated” the menace, highlighting the essential position of automated defenses in combating fashionable cyberattacks that may materialize and vanish in minutes.
DDoS Assault Graph (Supply: Cloudflare)
This record-shattering occasion shouldn’t be an remoted incident. In line with Cloudflare, its safety infrastructure has been beneath intense stress over the previous few weeks, having blocked “a whole bunch of hyper-volumetric DDoS assaults.”
Amongst these was one other vital assault that registered 5.1 billion packets per second (Bpps), demonstrating the various and chronic nature of the threats concentrating on on-line providers.
A UDP (Consumer Datagram Protocol) flood is a kind of DDoS assault the place the attacker overwhelms a goal server with an enormous variety of UDP packets.
As a result of UDP is a “connectionless” protocol, the server will be shortly exhausted because it makes an attempt to course of and reply to every incoming packet, ultimately rendering it unable to deal with professional site visitors.
The origination of such a large-scale assault from a serious public cloud supplier like Google Cloud highlights a persistent problem within the cybersecurity panorama.
Malicious actors usually exploit the huge assets and scalability of cloud platforms to construct highly effective botnets, able to launching assaults with a magnitude that may be tough to realize with conventional {hardware}.
Cloudflare has indicated {that a} extra detailed technical evaluation of the assault can be supplied in an upcoming report.
Discover this Story Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates.