Energetic Listing (AD) stays the muse of authentication and authorization in Home windows environments. Menace actors concentrating on the NTDS.dit database can harvest each area credential, unlock lateral motion, and obtain full area compromise.
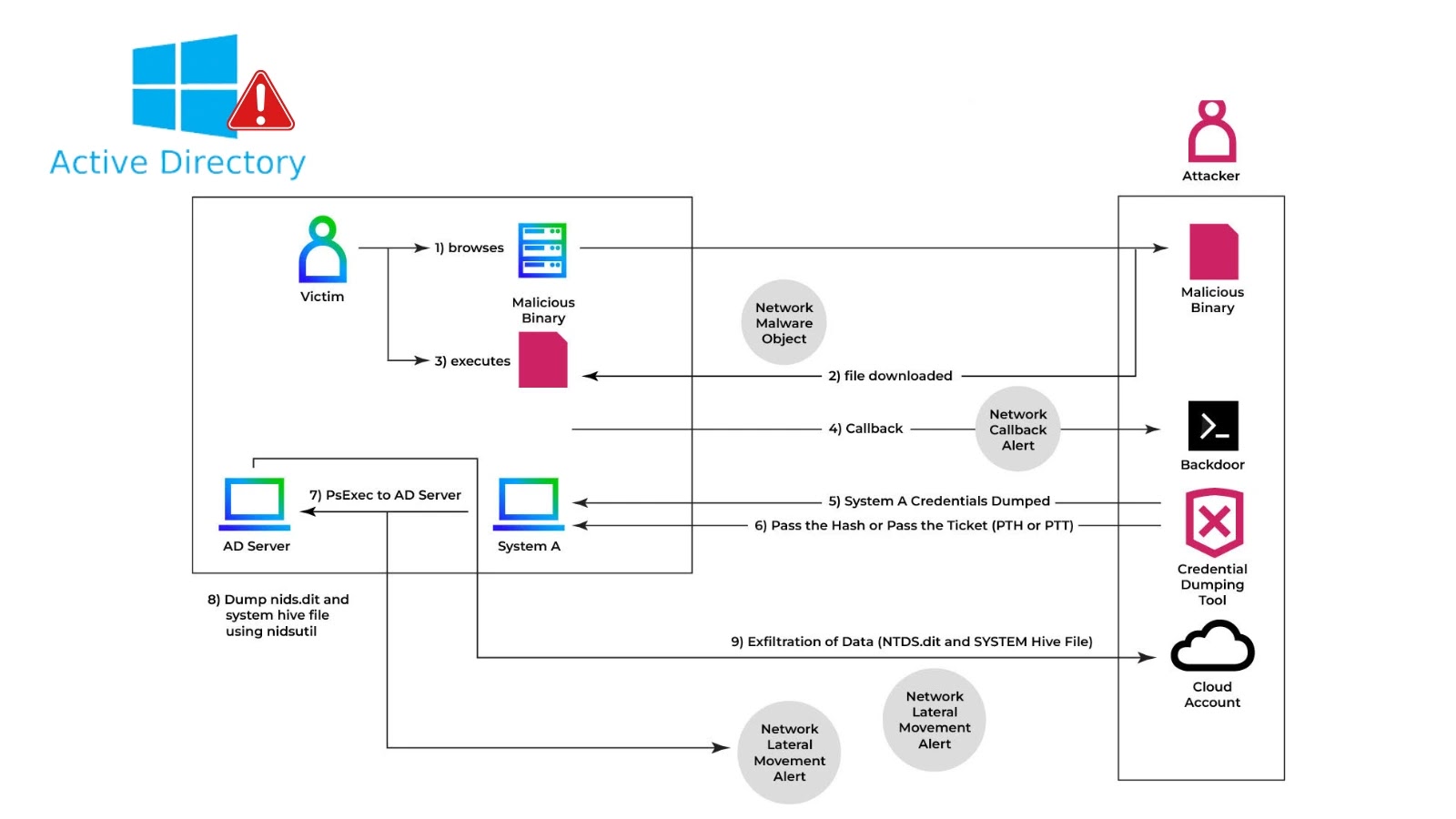
Attackers leveraged native Home windows utilities to dump and exfiltrate NTDS.dit, bypassing customary defenses.
The adversary on this case obtained DOMAIN ADMIN privileges by way of a profitable phishing marketing campaign and subsequent privilege escalation. As soon as elevated, they executed:
To create a Quantity Shadow Copy and extract NTDS.dit, silently bypassing file locks. With the SYSTEM hive obtained, attackers decrypted the database offline utilizing secretsdump.py from Impacket:
This chain enabled harvesting of NTLM and AES hashes for all area accounts with out triggering conventional endpoint alarms.
Full Kill Chain
After archiving and compressing the dump with tar -czf ntds.tar.gz c:tempntds.dit c:tempSYSTEM, the attackers exfiltrated information over SMB to a compromised file share.
NTDS.dit file dump
Trellix detected this exercise by way of two high-fidelity signatures: anomalous SMB write patterns exceeding baseline quantity and a customized exfiltration signature for big NTDS file transfers.
Behavioral detection flagged sudden esentutl processes working outdoors upkeep home windows, and protocol anomaly alerts triggered on shadow copy reads to C:$VolumeShadowCopy.
Via Trellix Sensible, AI-driven alert correlation highlighted the development from VSS creation to SMB add, lowering analyst workload by 60% and reducing imply time to detect (MTTD) by 45%.
The theft of NTDS.dit poses an existential risk to Home windows domains, offering attackers full management over all credentials.
NTDS.dit archived for exfiltration
Conventional defenses usually miss the low-and-slow strategies employed throughout shadow copy creation and offline decryption.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.