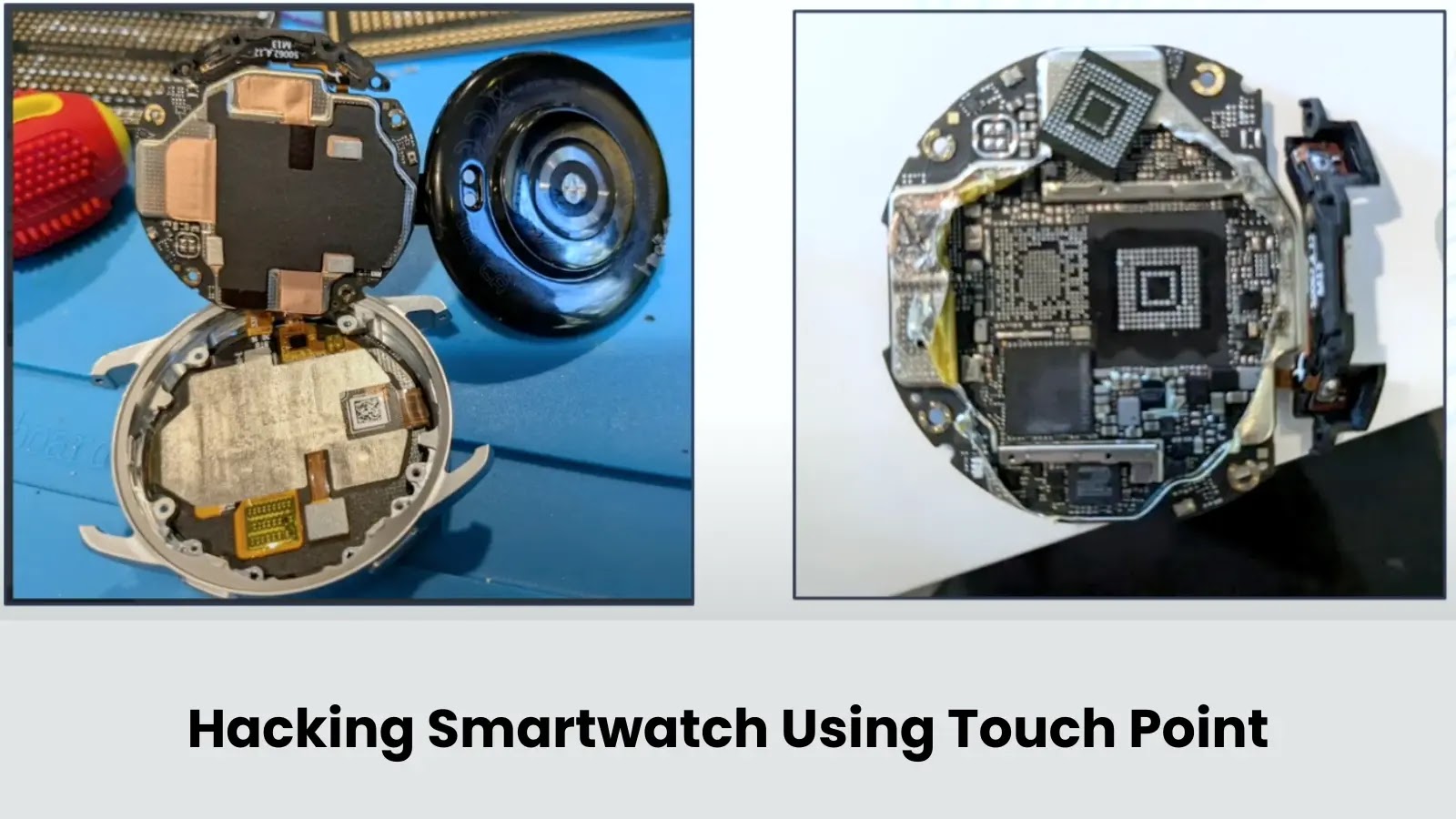
Safety researcher Sergei Volokitin has offered findings on {hardware} vulnerabilities found in Xiaomi gadgets, together with the corporate’s S3 smartwatch, throughout a presentation at a significant cybersecurity convention.
The analysis was carried out as a part of a collaborative safety occasion the place researchers and distributors work collectively to establish and tackle machine vulnerabilities.
The safety analysis was carried out in the course of the convention’s “Exhausting Pwn” occasion in November 2024, the place impartial safety researchers gathered to look at varied shopper electronics for potential vulnerabilities.
The occasion, which takes place yearly within the Netherlands and the US, brings collectively safety consultants and machine producers in a collaborative atmosphere targeted on enhancing {hardware} safety.
Throughout the multi-day occasion, researchers have been supplied with professional-grade gear, together with soldering irons, warmth weapons, and oscilloscopes, to conduct their {hardware} evaluation.
The format allows safety consultants to collaborate straight with vendor representatives to establish vulnerabilities and report findings that may improve machine safety.
Xiaomi Smartwatch Hacked
The 2024 occasion particularly featured Xiaomi merchandise, together with Mi Band health trackers, smartwatches, headphones, and different shopper electronics. Earlier years have seen comparable collaborative safety examinations of gadgets from main know-how corporations, together with Meta’s Oculus merchandise and Google’s Nest ecosystem.
Sergei Volokitin, who makes a speciality of low-level safety evaluation and conducts impartial safety analysis alongside bug bounty work and safety consultancy, targeted their consideration on two major Xiaomi gadgets in the course of the occasion.
Initially analyzing an outside digicam system, the researcher found that recorded footage was saved in plain textual content format on the machine’s file system, permitting potential attackers to recuperate video content material.
The digicam evaluation revealed further safety issues past unencrypted storage. The researcher recognized that safety tokens used for backend communication have been saved in accessible places on the machine’s file system.
These tokens may doubtlessly be exploited by attackers who acquire bodily entry to the machine. Each vulnerabilities have been reported to Xiaomi, and the corporate acknowledged the safety findings.
Following the digicam analysis, the safety knowledgeable shifted focus to Xiaomi’s S3 smartwatch, noting that the machine offered attention-grabbing safety challenges on account of its restricted third-party software help.
Fashionable smartwatches, the researcher defined, operate equally to smartphones with restricted capabilities however nonetheless deal with delicate consumer knowledge, together with textual content notifications, calendar info, health and well being metrics, and cost card knowledge for contactless transactions.
The smartwatch additionally helps Bluetooth connectivity for cellphone integration and NFC capabilities for each funds and machine unlocking options with Xiaomi smartphones. This mix of delicate knowledge entry and a number of connectivity choices makes such gadgets engaging targets for safety analysis.
The analysis highlights the rising significance of {hardware} safety in shopper electronics, significantly for gadgets that customers carry day by day and will lose or have stolen.
In contrast to stationary gadgets in safe environments, wearable know-how faces distinctive safety challenges on account of its transportable nature and the delicate private knowledge it shops and processes.
The collaborative method demonstrated at HardPwn represents an business pattern towards proactive safety analysis, the place producers work straight with safety researchers to establish and tackle vulnerabilities earlier than malicious actors can exploit them.
This partnership mannequin permits for accountable disclosure and safety enhancements that profit all customers of those more and more linked gadgets.
Meet the cyber warriors Who Stopped the WannaCry Ransomware assault => Free Reside Webinar