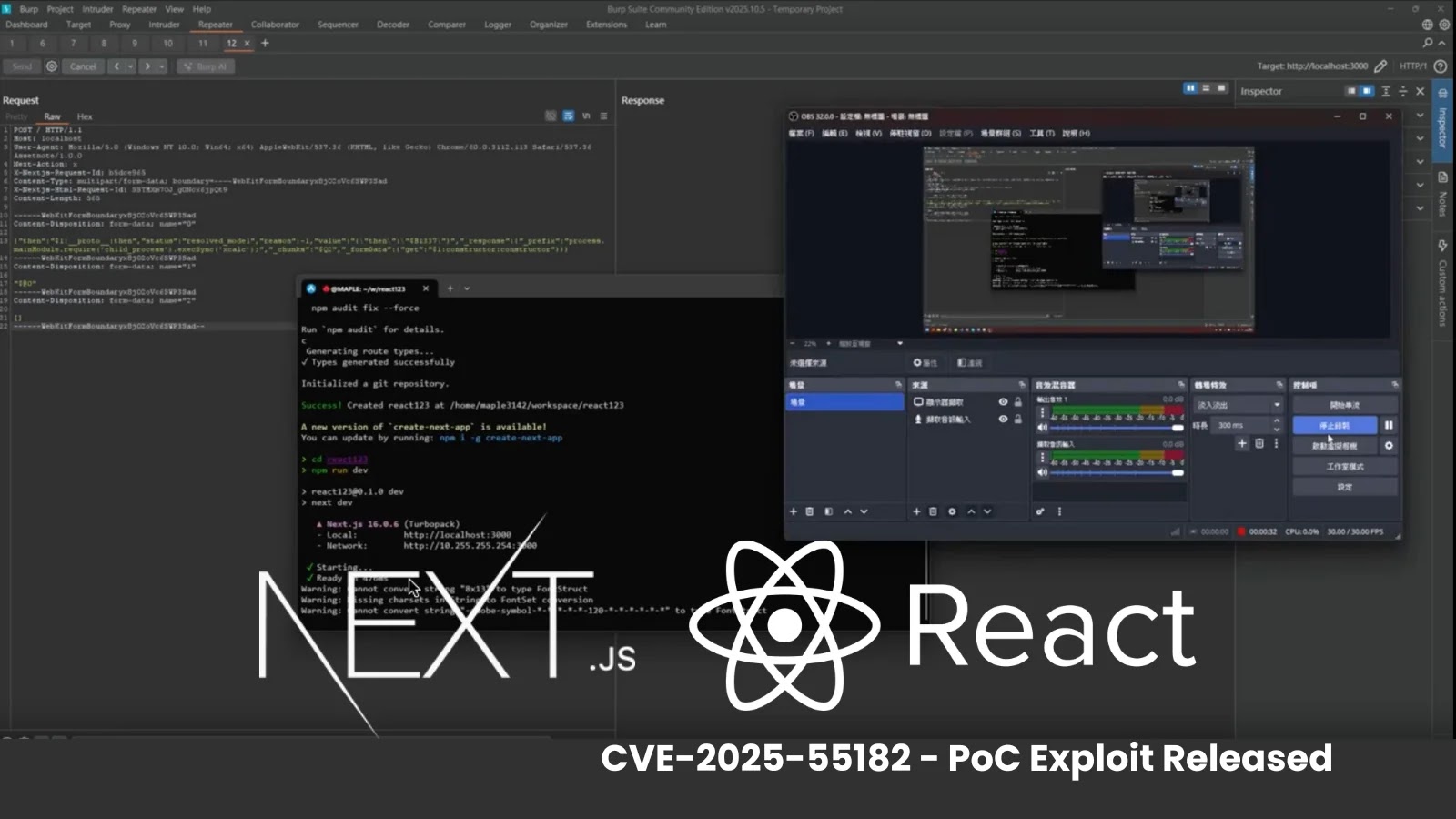
A proof-of-concept (PoC) exploit for CVE-2025-55182, a maximum-severity distant code execution (RCE) flaw in React Server Elements, surfaced publicly this week, heightening alarms for builders worldwide.
Dubbed “React2Shell” by some researchers, the vulnerability carries a CVSS rating of 10.0 and impacts React variations 19.0.0 via 19.2.0, in addition to Subsequent.js 15.x and 16.x utilizing App Router. Even functions not explicitly implementing server features stay uncovered in the event that they help React Server Elements (RSC).
Safety researcher @maple3142 demonstrated the exploit through a Twitter submit, showcasing a easy multipart HTTP request that injects a Node.js payload.
The demo triggers little one course of, popping open a Linux calculator on the goal server with out authentication.
An accompanying video captures a curl-like command exploiting the flaw via React’s Flight protocol, bypassing serialization safeguards with strategies like Blob references labeled “$B1337.” Framed as a CTF-style “JS jail” problem, the shared gist drew reward from the group alongside questions on evasion strategies.
The basis trigger lies in insecure deserialization throughout the RSC Flight protocol, the place malformed payloads pollute object prototypes and hijack server-side execution.
Found by Lachlan Davidson and responsibly disclosed to Meta and Vercel on November 29, the problem went public on December 3, prompting swift patches.
A brand new scanner device was additionally launched to determine susceptible endpoints on the community for CVE-2025-55182.
Amazon risk intelligence reported exploitation makes an attempt by China-nexus teams like Earth Lamia inside hours of disclosure. Wiz Analysis estimates 39% of cloud environments host susceptible cases, scanning over 968,000 servers.
Palo Alto Networks Unit 42 and others confirmed the assault requires solely a crafted POST request to RSC endpoints, attaining near-100% reliability in exams. React’s official advisory urges instant upgrades, noting the flaw persists in default configurations of common frameworks.
Builders ought to audit deployments, apply patches from React 19.2.1+ and Subsequent.js updates, and monitor for anomalies.
Whereas no widespread breaches are confirmed but, the PoC’s simplicity amplifies dangers in manufacturing environments. This incident underscores the perils of server-side rendering in fashionable JavaScript stacks.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.